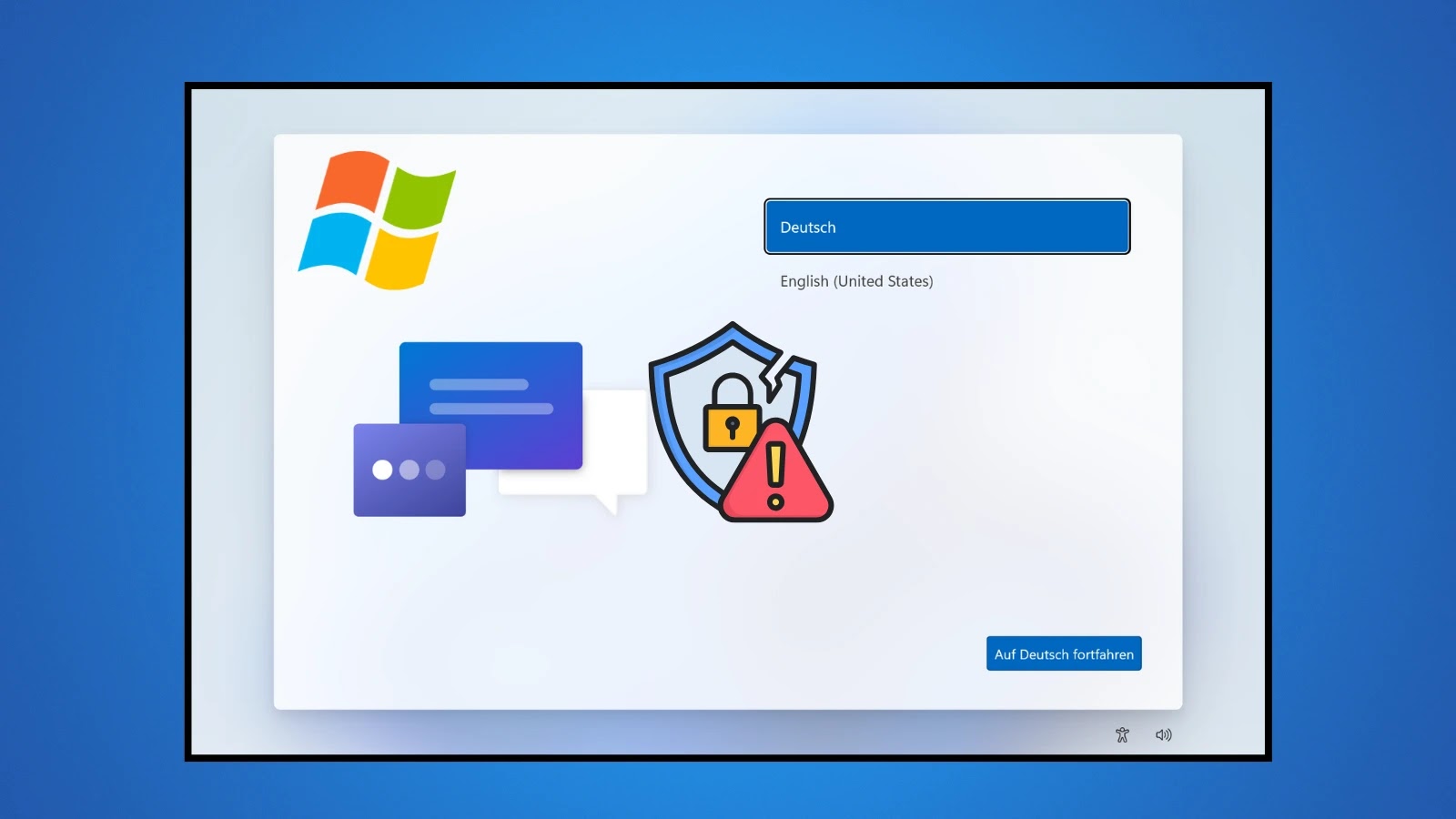
A new method has been identified to exploit Windows Out-of-Box-Experience (OOBE) that bypasses existing protections and grants administrative command line…
A severe security vulnerability has been discovered in a popular WordPress plugin used by over 70,000 websites worldwide, potentially exposing…
The Zelle lawsuit 2025 is making headlines as New York Attorney General Letitia James takes legal action against Early Warning…
A sophisticated cybercriminal organization known as VexTrio has been orchestrating a massive fraud empire through deceptive CAPTCHA robots and malicious…
Security researchers have disclosed critical vulnerabilities in Xerox FreeFlow Core that enable unauthenticated remote attackers to execute arbitrary code on…
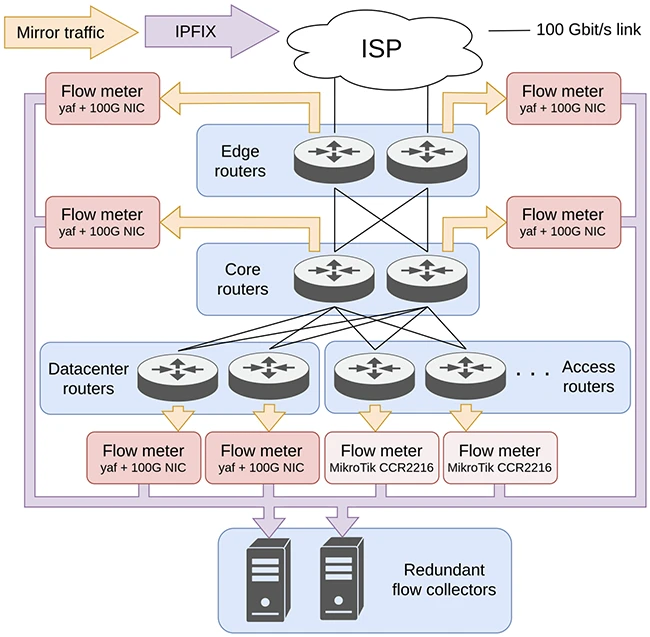
Flow monitoring tools are useful for tracking traffic patterns, planning capacity, and spotting threats. But many off-the-shelf solutions come with…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued urgent alerts regarding two critical vulnerabilities in N-able N-Central that are…
Learn how AI technologies can be applied to enhance security, create safe and responsible applications, develop intelligent agents, and improve…
Aug 14, 2025Ravie LakshmananVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added two security…
Critical security vulnerabilities in Microsoft Exchange Server enable attackers to perform spoofing and tampering attacks over network connections. The vulnerabilities…
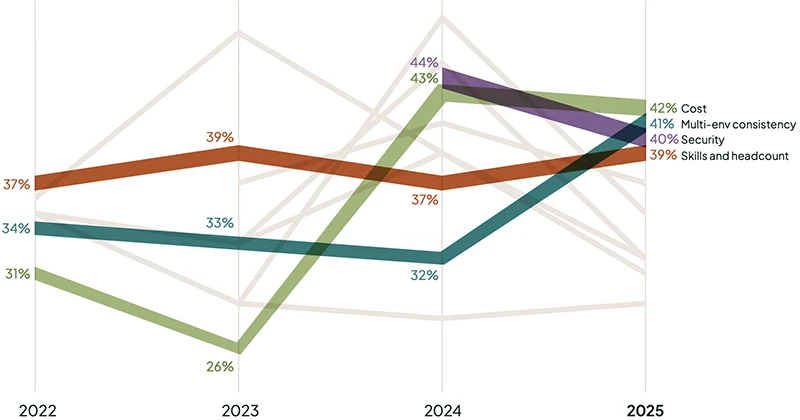
AI is changing how enterprises approach Kubernetes operations, strategy, and scale. The 2025 State of Production Kubernetes report from Spectro…
The rise of the ‘hyper connected’ consumer is transforming retail and prompting sector leaders to implement secure, responsive networks to…