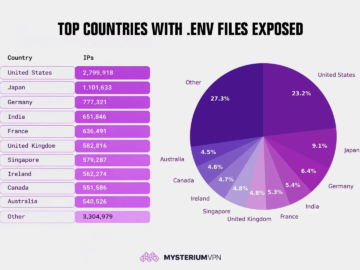
12 Million exposed .env files reveal widespread security failures Pierluigi Paganini February 27, 2026 Mysterium VPN found 12M IPs exposing…
Cybercriminals have found a new way to get past users’ defenses — by hiding malware inside gaming tools that look…
The cybersecurity community is witnessing a rise in credential‑stuffing attacks targeting corporate Single Sign‑On (SSO) systems, with recent campaigns focusing…
Personal liability is becoming a routine part of the CISO job. In Splunk’s 2026 CISO Report, titled From Risk to…
Ravie LakshmananFeb 27, 2026Online Scam / Digital Advertising Meta on Thursday said it’s taking legal action to tackle scams on…
India’s rapidly expanding space sector has received a major policy push with the release of new space cyber security guidelines…
When the open-source AI agent for OpenClaw burst onto the scene, it did so with astonishing speed. In just five days, the…
North Korea-linked threat group APT37 has launched a sophisticated new campaign using a fresh set of custom malware tools specifically…
The Dutch telecommunications company Odido suffered a massive data breach that exposed the personal information of nearly 700,000 customers. The…
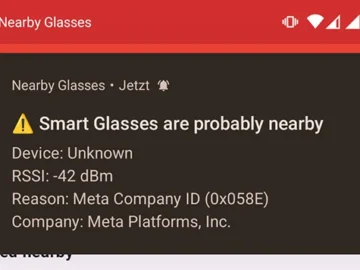
Smart glasses with built-in cameras are showing up in more public spaces, and a growing number of people want a…
Claude Code Hacked RCE Hijacked Organization API keys Critical vulnerabilities in Anthropic’s Claude Code, an AI-powered command-line development tool. The…
A Go‑based remote administration tool known as Vshell is emerging as a favored alternative to Cobalt Strike among both red teams and…