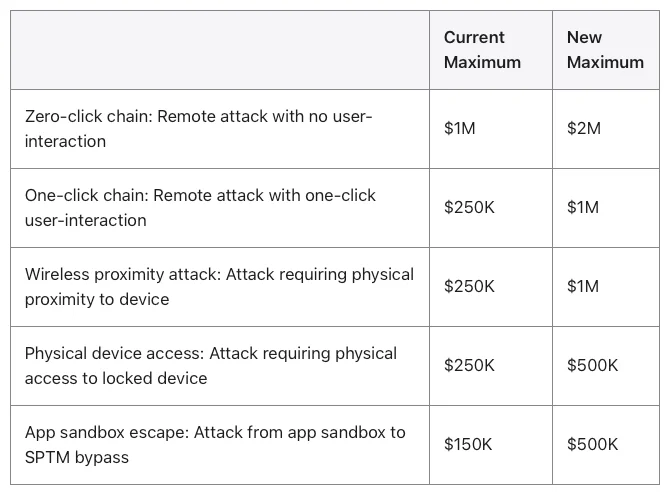
Apple bug bounty program’s categories are expanding and rewards are rising, and zero-click exploit chains may now earn researchers up…
Oct 10, 2025Ravie LakshmananCybercrime / Malware Cybersecurity researchers have flagged a new set of 175 malicious packages on the npm…
An emergent strain of ransomware known as Warlock – which was linked to multiple attacks orchestrated via vulnerabilities in on-premise…
Three exploitation campaigns targeting Cisco and Palo Alto Networks firewalls and Fortinet VPNs originate from IPs on the same subnets,…
A significant uptick in Akira ransomware attacks has been observed exploiting unpatched SonicWall SSL VPN devices between July and August…
In a Cybercrime Magazine Podcast episode this week, our producer and Editor-in-Chief Steve Morgan shares a real-life scam incident he encountered, telling listeners exactly…
Cybernews discovered how two AI companion apps, Chattee Chat and GiMe Chat, exposed millions of intimate conversations from over 400,000…
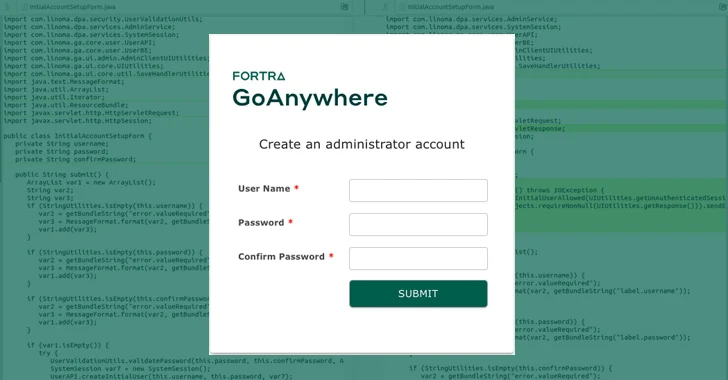
Oct 10, 2025Ravie LakshmananVulnerability / Network Security Fortra on Thursday revealed the results of its investigation into CVE-2025-10035, a critical…
The Competition and Markets Authority (CMA) has given Google strategic market status (SMS) for search and search advertising. The regulator…
A newly identified botnet takes a ‘shotgun’ approach to compromising devices, packing over 50 exploits targeting routers, servers, cameras, and…
2025 has been one of Wallarm’s biggest years yet. In the last few months alone, we unveiled our industry-first API…
Microsoft Defender for Endpoint is incorrectly flagging specific versions of SQL Server as having reached their end-of-life, causing potential confusion…