A critical weakness in GitHub Copilot Chat discovered in June 2025 exposed private source code and secrets to attackers. Rated…
Juniper Networks has announced patches for nearly 220 vulnerabilities in Junos OS, Junos Space, and Security Director, including nine critical-severity…
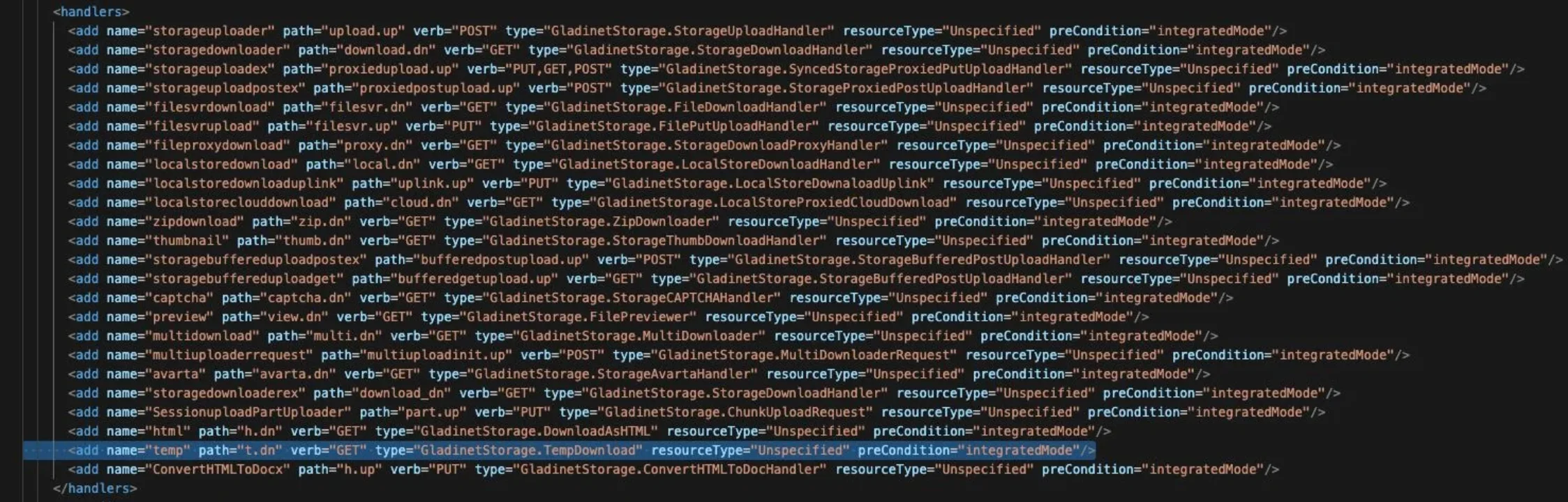
An active in-the-wild exploitation of a zero-day vulnerability in Gladinet CentreStack and Triofox products. Tracked as CVE-2025-11371, the unauthenticated Local…
LLM-enabled malware poses new challenges for detection and threat hunting as malicious logic can be generated at runtime rather than…
CVE-2025-11371, a unauthenticated Local File Inclusion vulnerability in Gladinet CentreStack and Triofox file-sharing and remote access platforms, is being exploited…
Oct 10, 2025Ravie LakshmananVulnerability / Zero-Day Cybersecurity company Huntress said it has observed active in-the-wild exploitation of an unpatched security…
Trend Micro’s Zero Day Initiative (ZDI) this week published 13 advisories describing unpatched vulnerabilities in Ivanti Endpoint Manager. One of…
Emerging from a recent wave of targeted campaigns, SnakeKeylogger has surfaced as a potent infostealer that capitalizes on PowerShell and…
“The plans are being used and being built,” says Michael “Barni” Barnhart, a leading authority in North Korean hacking and…
Gladinet CentreStack and Triofox have come under active attack as threat actors exploit an unauthenticated local file inclusion flaw (CVE-2025-11371)….
Microsoft Threat Intelligence has revealed a spate of financially motivated cyberattacks against universities across the United States. The threat actor,…
Apple on Friday announced significant updates to its bug bounty program and the company is now offering up to $2…