Amazon Web Services (AWS) released bulletin AWS-2025-020 detailing a serious flaw in the macOS version of its Client VPN software….
OpenAI’s latest “Disrupting Malicious Uses of AI” report shows that hackers and influence operators are moving toward a more organised…
People often talk about going digital and digitisation initiatives, but technology is only half the story. As Thomas Bodé, chief…
North Korean threat actors are estimated to have stolen more than $2 billion in cryptocurrency during the first nine months…
Three newly disclosed vulnerabilities have been identified in the Lua scripting engine of Redis 7.4.5, each presenting severe risks of…
Enterprise AI assistants face a hidden menace when invisible control characters are used to smuggle malicious instructions into prompts. In September…
When I first started in IT asset disposition more than two decades ago, sustainability barely registered in boardroom discussions. Regulations…
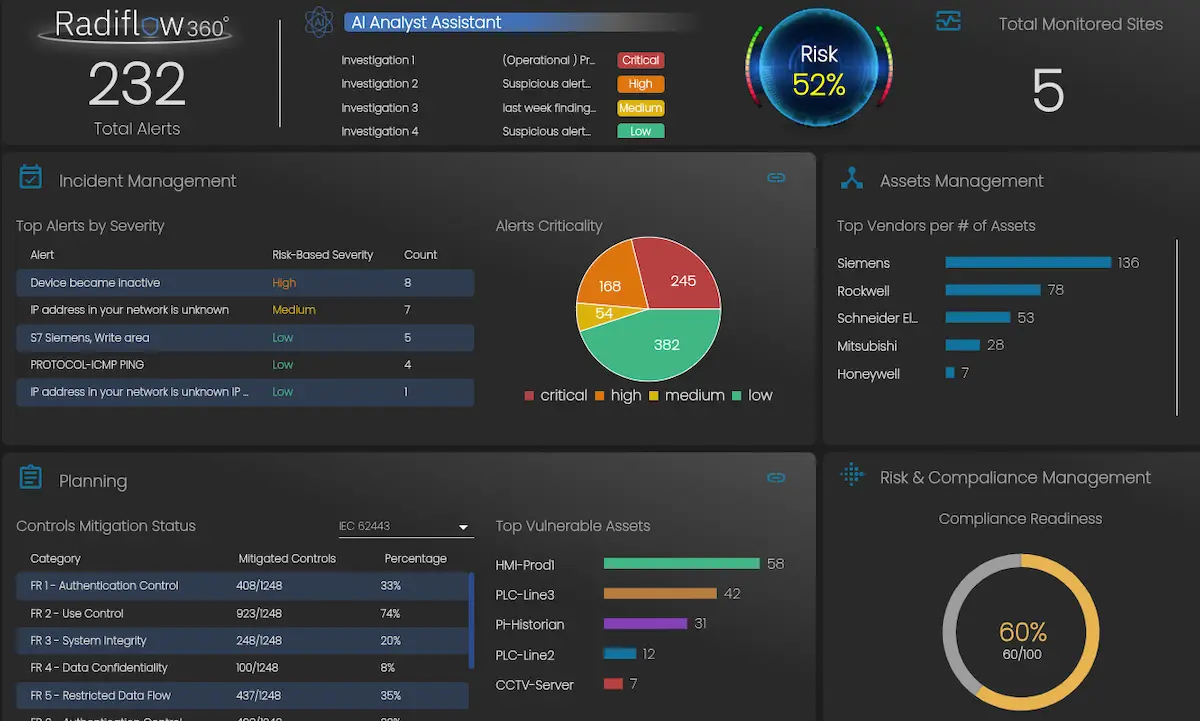
Industrial cybersecurity firm Radiflow has unveiled a new platform for mid-sized enterprises. The new platform, named Radiflow360, leverages AI to…
Redis patches 13-Year-Old Lua flaw enabling Remote Code Execution Pierluigi Paganini October 08, 2025 Redis warns of CVE-2025-49844, a Lua…
OpenAI announced it has banned a series of ChatGPT accounts linked to Chinese state-affiliated hacking groups that used the AI…
In an era where AI and SaaS applications underpin daily workflows, organizations face an unprecedented challenge: the invisible exfiltration of…
Cybersecurity researchers at Point Wild’s Lat61 Threat Intelligence Team have found a new infostealer called Shuyal Stealer, a malware strain…