Google rolled out version 141.0.7390.65/.66 for Windows and Mac and 141.0.7390.65 for Linux. This update fixes three critical security flaws,…
OpenAI on Tuesday said it disrupted three activity clusters for misusing its ChatGPT artificial intelligence (AI) tool to facilitate malware…
More information has come to light on the recently patched Oracle E-Business Suite (EBS) zero-day, with evidence indicating that threat…
Google has released Chrome version 141.0.7390.65/.66 for Windows and Mac, along with 141.0.7390.65 for Linux, addressing multiple critical security vulnerabilities…
A critical SQL injection vulnerability in FreePBX, designated as CVE-2025-57819, has been actively exploited by attackers to modify the database and…
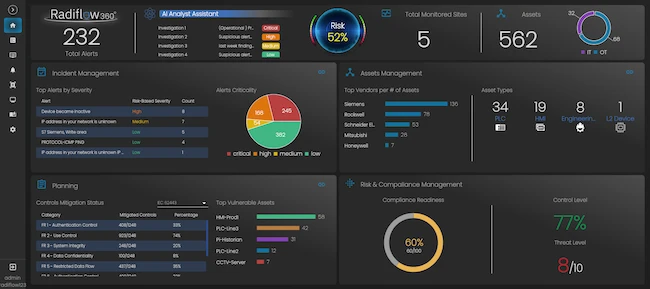
Radiflow has launched the new Radiflow360, a unified, AI-enhanced OT cybersecurity platform that delivers visibility, risk management and streamlined incident…
A newly identified threat group called Crimson Collective has emerged as a significant security concern for organizations using Amazon Web Services (AWS),…
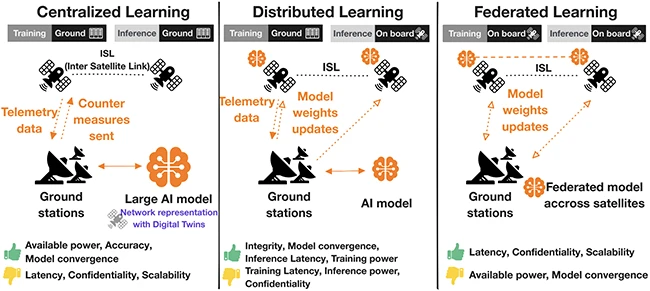
If you think managing cloud security is complex, try doing it across hundreds of satellites orbiting the planet. Each one…
BK Technologies Corporation, a Florida-based communications equipment manufacturer, disclosed a significant cybersecurity incident that compromised its IT systems and potentially…
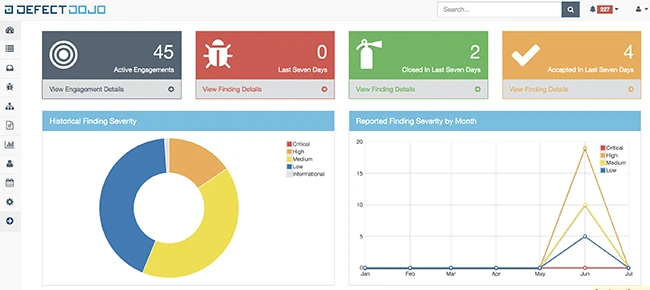
DefectDojo is an open-source tool for DevSecOps, application security posture management (ASPM), and vulnerability management. It helps teams manage security…
A groundbreaking cybersecurity vulnerability has been discovered that transforms everyday computer mice into sophisticated eavesdropping tools. Researchers have developed the…
Cybercrime is a global problem, but not every country is equally equipped to fight it. In many developing economies, cybersecurity…