GoAnywhere MFT zero-day used by Storm-1175 in Medusa ransomware campaigns Pierluigi Paganini October 07, 2025 Storm-1175 exploits GoAnywhere MFT flaw…
A long-running theme in the use of adversarial AI since the advent of large language models has been the automation…
The Western Australian government has secured one of two core platforms it will need to build a digital twin of…
Sports betting giant DraftKings has notified an undisclosed number of customers that their accounts had been hacked in a recent…
The state of AI in software engineering report from Harness, based on a Coleman Parker poll of 900 software engineers…
BK Technologies Corporation, a provider of communications equipment for public safety and government agencies, has disclosed a cybersecurity incident in…
Oct 07, 2025Ravie LakshmananMalware / Threat Intelligence A Vietnamese threat actor named BatShadow has been attributed to a new campaign…
Spend any length of time hanging out with Okta’s in-house cyber security team and sooner or later you’re going to…
I did a short post (and a video) about how AI shouldn’t be thought of as a bubble because a…
North Korean hackers have stolen an estimated $2 billion worth of cryptocurrency assets in 2025, marking the largest annual total…
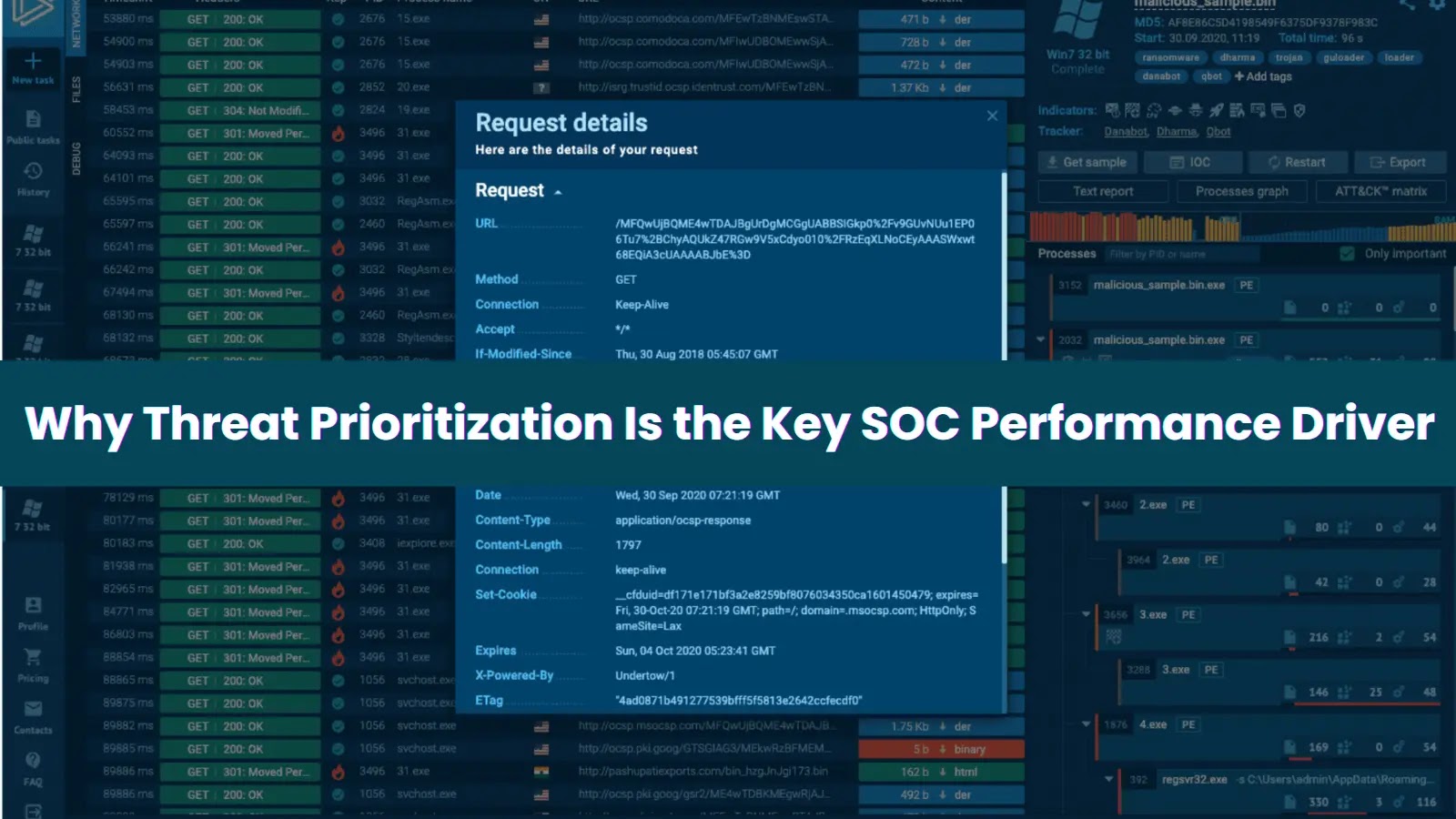
CISOs face a paradox in their SOCs every day: more data and detections than ever before, yet limited capacity to…
A new vulnerability in Redis, now known as RediShell (CVE-2025-49844), has put tens of thousands of servers at risk of…