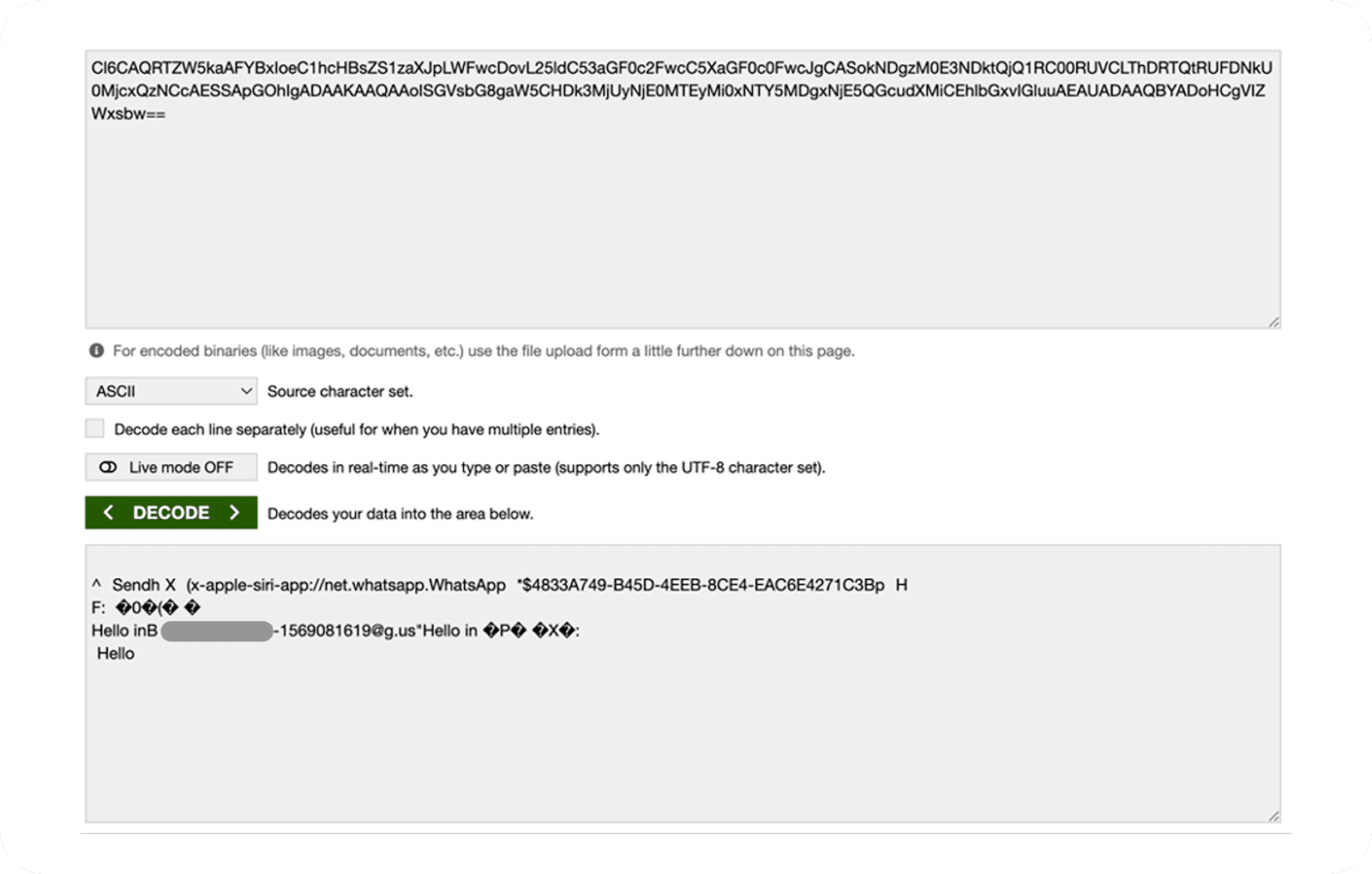
A new variant of the DarkCloud information-stealer malware has been observed targeting Microsoft Windows systems, primarily affecting Windows users by…
Cybersecurity researchers are drawing attention to a new campaign that’s using legitimate generative artificial intelligence (AI)-powered website building tools like…
The “how many r’s in strawberry” test for AI intelligence is dumb. As a writer to write a quality sentence…
Top streaming services like Netflix and Disney+ have made sustained investments over the years to lock their content down. Whenever…
Claroty’s Team82 research unit has unveiled four vulnerabilities affecting Axis Communications’ widely deployed video surveillance ecosystem, potentially endangering thousands of…
A financially motivated threat actor has been involved in a cluster of activity linked to the ToolShell vulnerability in Microsoft…
LAS VEGAS — Businesses that don’t treat security with the gravity it requires — exhibited by lackluster or nonexistent preparation,…
The U.S. Federal Judiciary confirms that it suffered a cyberattack on its electronic case management systems hosting confidential court documents…
The Python Package Index (PyPI) has announced new restrictions aimed at mitigating ZIP parser confusion attacks that could exploit discrepancies…
LAS VEGAS — One of the big worries during the generative AI boom is where exactly data is traveling when…
The Salt team has spent the last 5-10 years producing blogs, comparison documents and webinars which highlight our credentials versus…
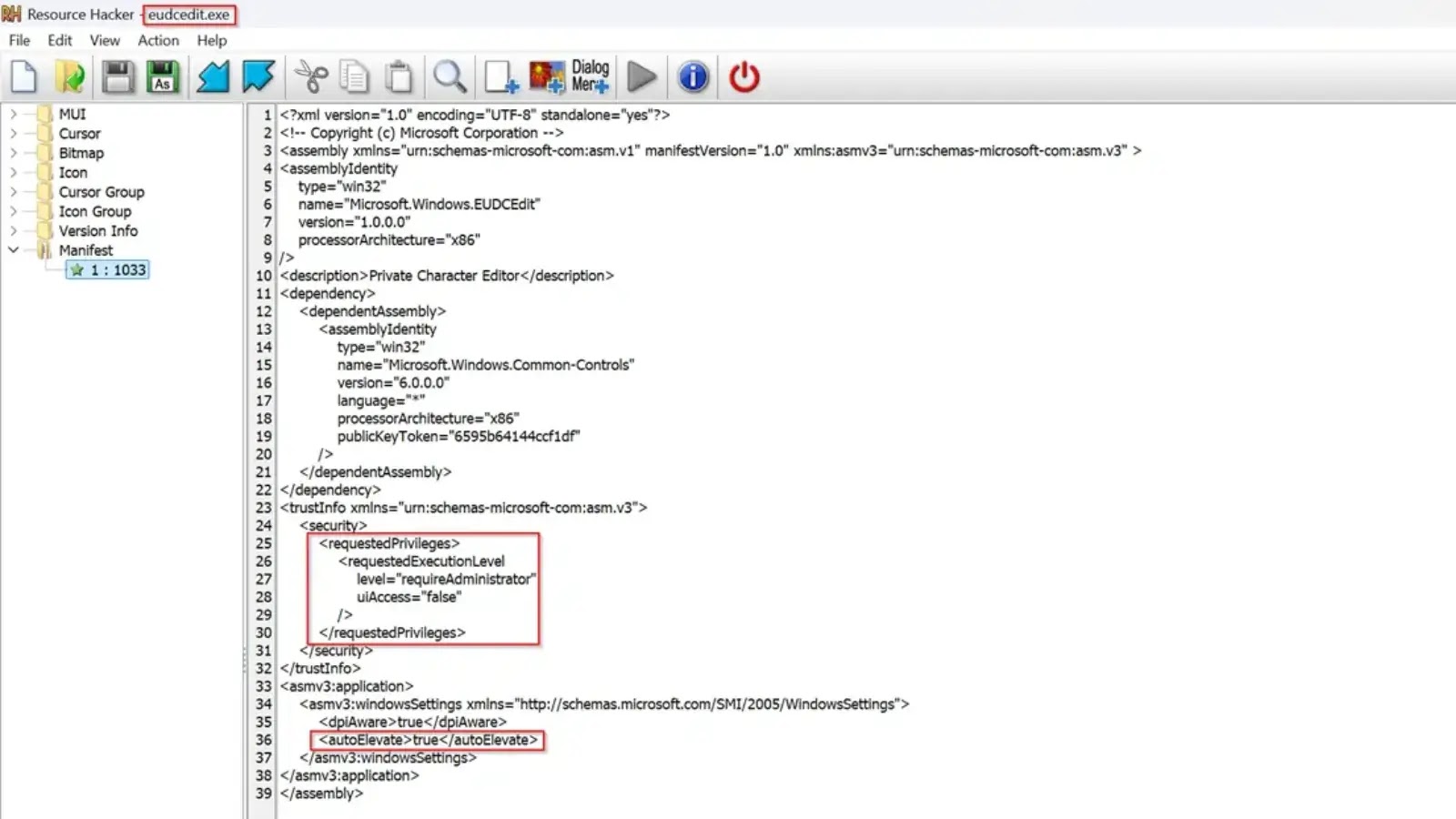
Cybersecurity researchers have uncovered a new technique that allows attackers to bypass Windows User Account Control (UAC) protections by exploiting…