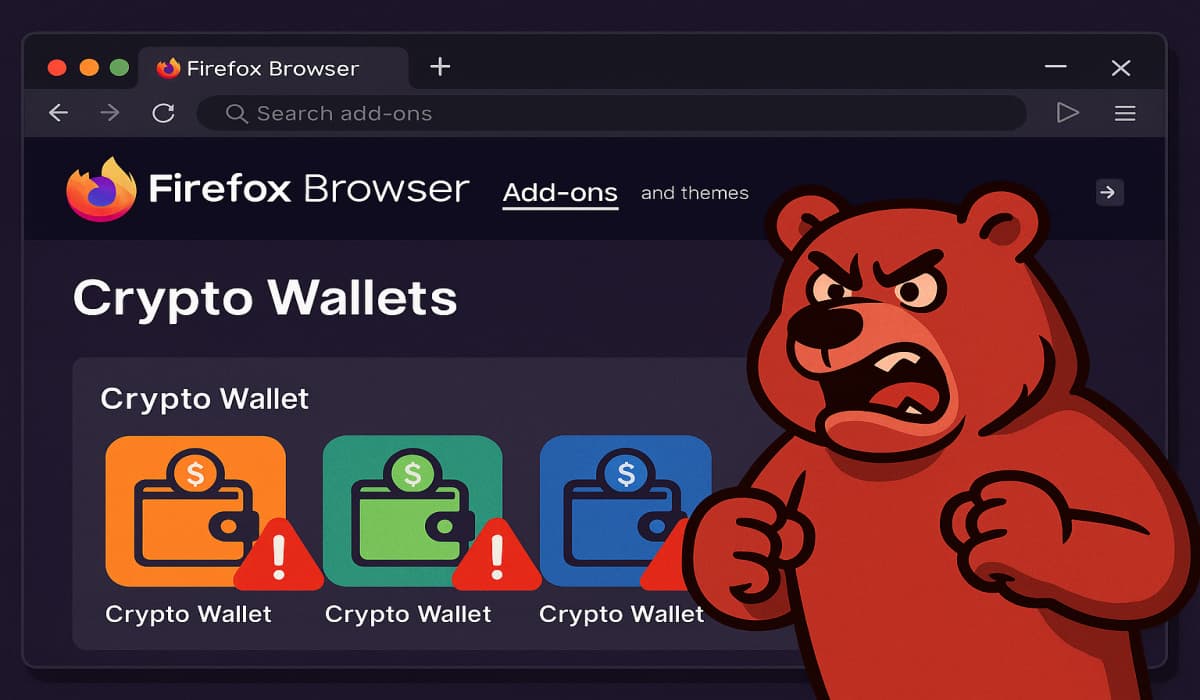
A sophisticated and large-scale cybercrime campaign, named GreedyBear, has been exposed for stealing at least a million dollars from cryptocurrency…
When an organization’s credentials are leaked, the immediate consequences are rarely visible—but the long-term impact is far-reaching. Far from the…
Microsoft has announced that the Microsoft 365 apps for Windows will start blocking access to files via the insecure FPRPC…
Columbia University has disclosed a major cybersecurity incident where an unauthorized third party accessed and extracted a significant volume of…
OpenAI has officially launched ChatGPT-5, marking a significant leap forward in artificial intelligence technology with a revolutionary unified system that…
The government is on a mission to make the UK an artificial intelligence (AI) superpower, by accelerating the adoption of…
Microsoft announced that it will phase out the Microsoft Lens PDF scanner app for Android and iOS devices starting in September….
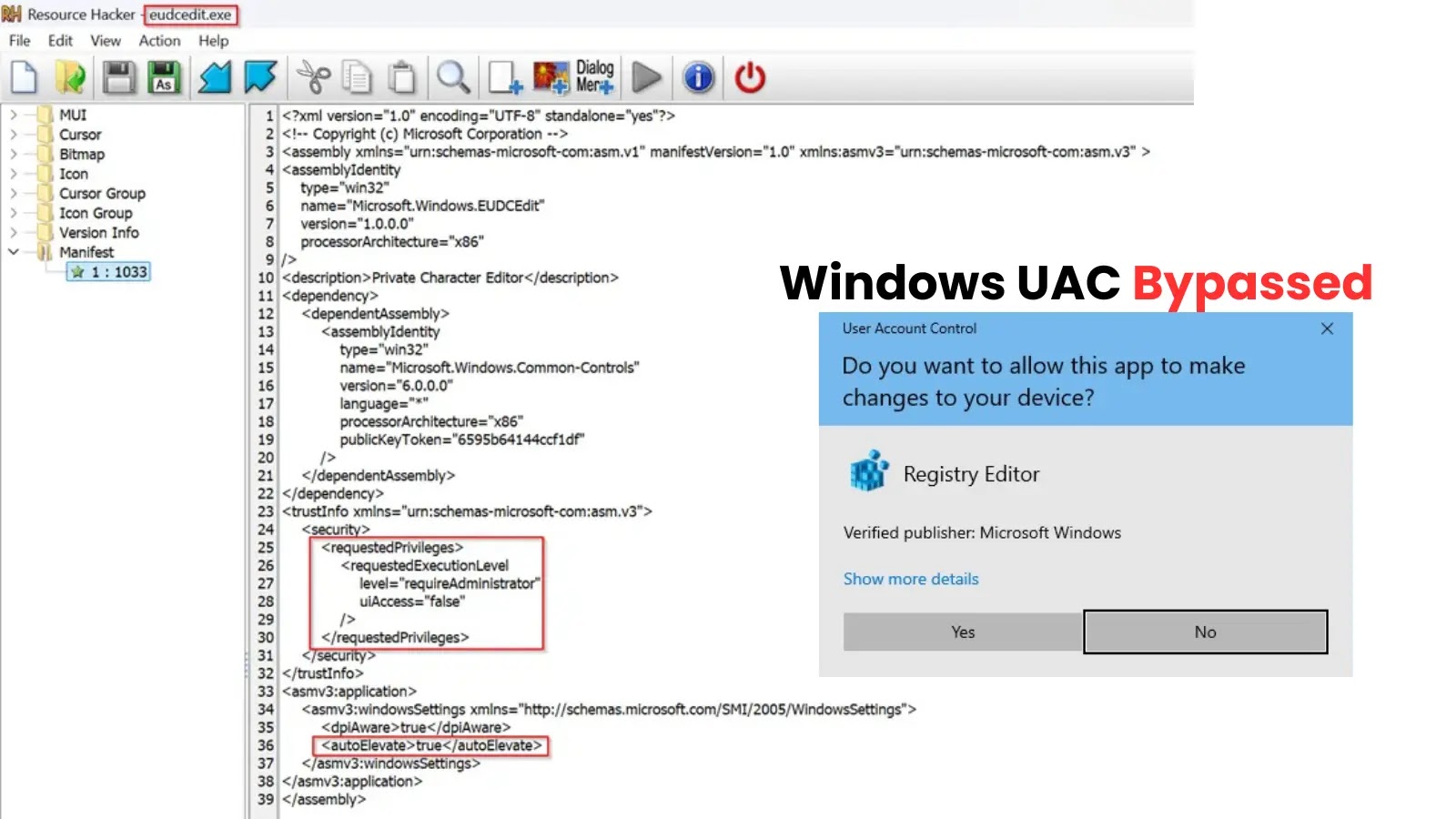
A sophisticated new technique that exploits the Windows Private Character Editor to bypass User Account Control (UAC) and achieve privilege…
The Cybersecurity and Infrastructure Security Agency (CISA) has released ten industrial control systems (ICS) advisories on August 7, 2025, highlighting…
OpenAI has updated its large language model (LLM) in ChatGPT to GPT-5, which it says takes a significant step towards…
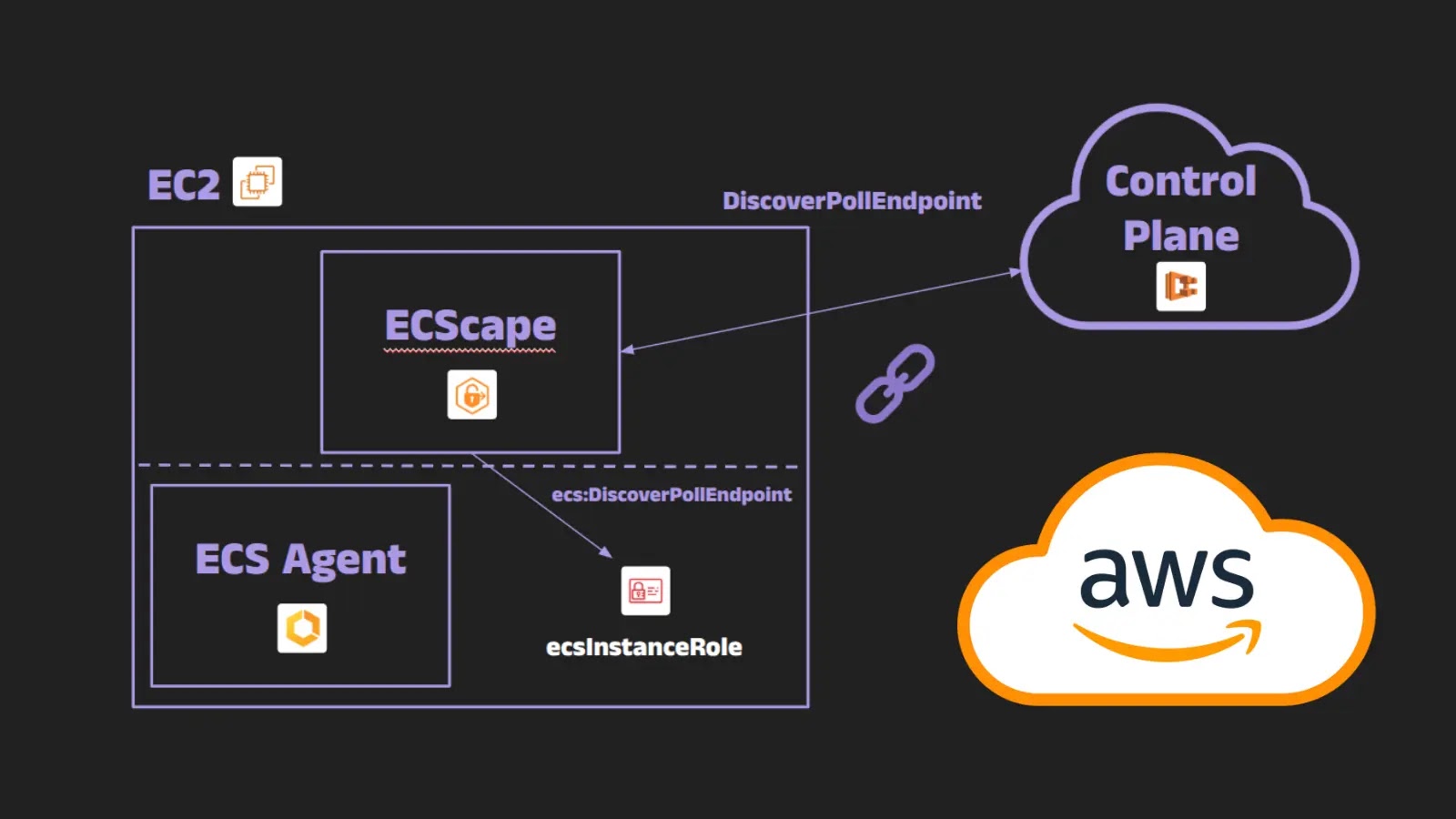
A sophisticated technique dubbed “ECScape” that allows malicious containers running on Amazon Elastic Container Service (ECS) to steal AWS credentials…
Security researchers have disclosed a critical vulnerability in Amazon Elastic Container Service (ECS) that allows malicious containers to steal AWS…