Microsoft Defender for Endpoint is currently experiencing a bug that generates false positive alerts concerning out-of-date Basic Input/Output System (BIOS)…
ASX-listed insurer QBE Insurance Group has shifted its cyber security leadership to the United States as part of an effort…
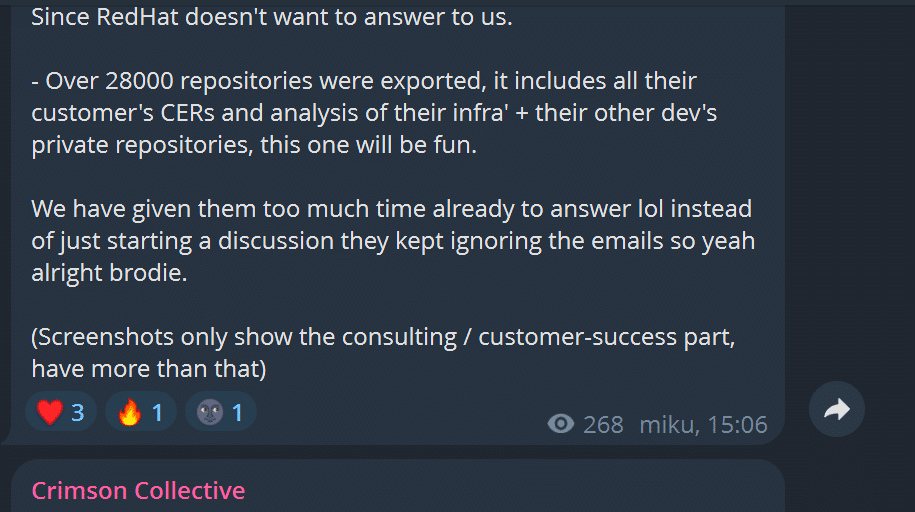
Red Hat on Thursday confirmed an attacker gained access to and stole data from a GitLab instance used by its…
Renault UK is informing customers that their personal data may have been compromised following a cyberattack on one of its…
The PSNI has commissioned a senior lawyer to review whether there was any misconduct by police officers following an independent…
Queensland’s Department of Child Safety has tapped Deloitte Australia to audit its Unify client management system. The audit into the…
Emails sent to Oracle customers by members of the Clop ransomware group assert that the cybercriminals are solely interested in…
Microsoft says Outlook for Web and the new Outlook for Windows will no longer display risky inline SVG images that…
Meta has announced that conversations with its AI assistant will soon be used for targeted advertising. If you’re the kind…
Hackers claim to have breached a Red Hat GitHub instance and stolen sensitive customer data. The claims were made in…
CERT-UA warns UAC-0245 targets Ukraine with CABINETRAT backdoor Pierluigi Paganini October 02, 2025 CERT-UA warns UAC-0245 targets Ukraine with CABINETRAT…
Networking hardware maker DrayTek released an advisory to warn about a security vulnerability in several Vigor router models that could…