A recently disclosed security vulnerability in Unity has prompted security updates and, in some cases, game removals across platforms like Steam….
The recent data theft and extortion campaign targeting Oracle E-Business Suite customers has been confirmed to be the work of…
With the release of Kali Linux 2025.3, a major update introduces an innovative tool that combines artificial intelligence and cybersecurity:…
Cybercriminals have ramped up attacks on WordPress websites by stealthily modifying theme files to serve unauthorized third-party scripts. This campaign…
Japanese brewing giant Asahi Group Holdings has confirmed that a ransomware attack has caused the week-long outage at its domestic…
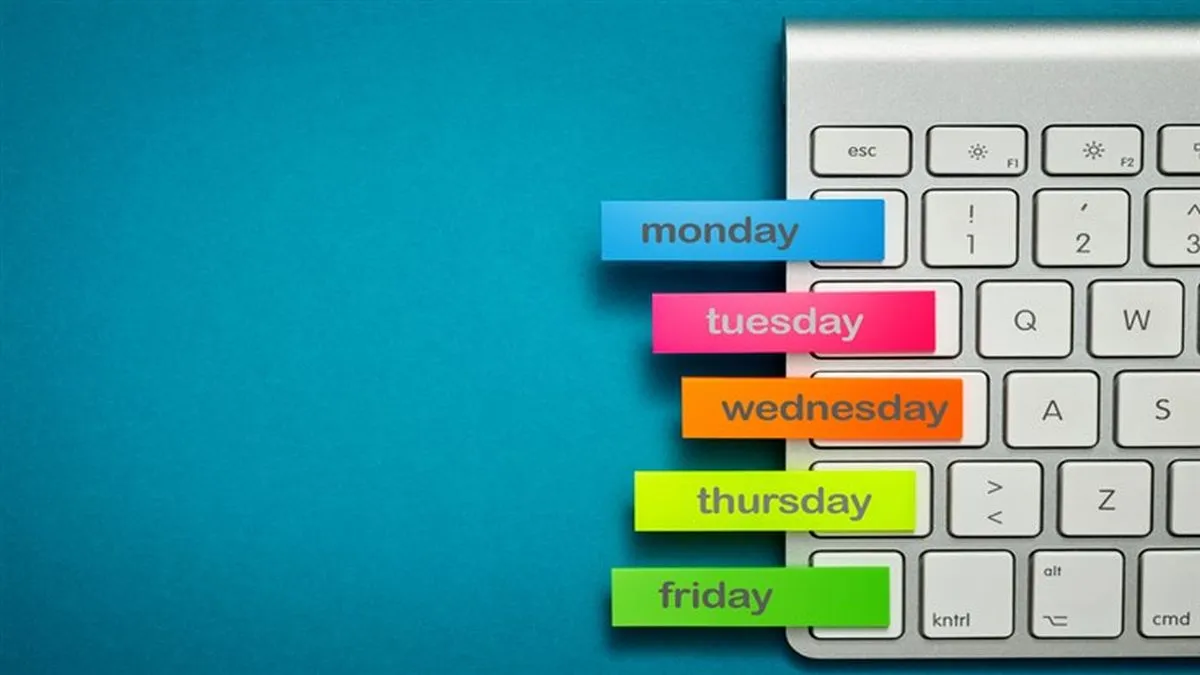
Zimbra users targeted in zero-day exploit using iCalendar attachments Pierluigi Paganini October 06, 2025 Threat actors exploited a Zimbra zero-day…
A publicly available proof-of-concept (PoC) exploit has been released for CVE-2025-32463, a local privilege escalation (LPE) flaw in the Sudo…
Modern ransomware operations have evolved far beyond simple opportunistic attacks into sophisticated, multi-stage campaigns that exploit legitimate Remote Access Tools…
October 3, 2025 – After posting children’s photos online and issuing ransom demands, cybercriminals targeting Kido nurseries say they’ve erased…
Reading the ENISA Threat Landscape 2025 report Pierluigi Paganini October 06, 2025 ENISA Threat Landscape 2025: Rising ransomware, AI phishing,…
A sophisticated technique uncovered where threat actors abuse Amazon Web Services‘ X-Ray distributed tracing service to establish covert command and…
A critical security vulnerability has been discovered in Redis Server that could allow authenticated attackers to achieve remote code execution…