A ransomware attack at Motility Software Solutions, a provider of dealer management software (DMS), has exposed the sensitive data of…
A sophisticated malicious package has infiltrated the Python Package Index (PyPI), masquerading as a legitimate SOCKS5 proxy tool while harboring…
WestJet, a leading Canadian airline based in Calgary, has confirmed that a cybersecurity attack exposed personal information belonging to some…
German Chancellor Friedrich Merz vowed to make Europe’s biggest economy competitive again after the cabinet approved measures aimed at reducing…
Adobe is warning its Analytics customers that an ingestion bug caused data from some organizations to appear in the analytics instances…
Ukrainian security agencies have issued an urgent warning regarding a sophisticated malware campaign targeting government and critical infrastructure sectors through…
A new Android banking and remote access trojan (RAT) dubbed Klopatra disguised as an IPTV and VPN app has infected…
Cybersecurity researchers have uncovered a sophisticated Android malware campaign targeting seniors through fraudulent travel and social activity promotions on Facebook….
The EU threat landscape is dominated by hacktivism, DDoS attacks and ransomware, according to the new 2025 ENISA Threat Landscape…
Microsoft is investigating a known issue that causes the classic Outlook email client to crash upon launch, which can only…
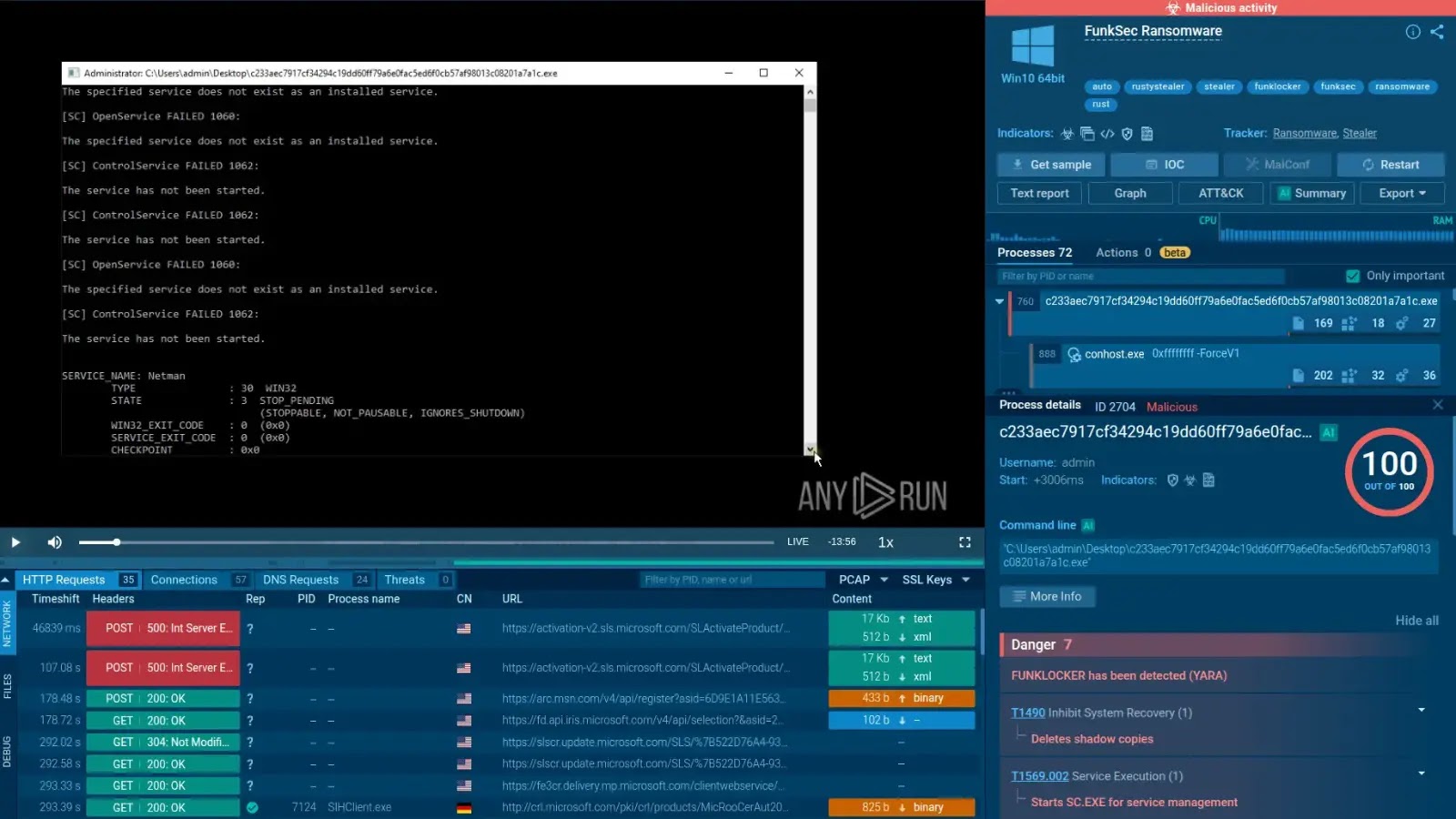
A new ransomware strain, dubbed FunkLocker, is leveraging artificial intelligence to expedite its development, while relying on the abuse of…
NVIDIA has issued a critical security bulletin revealing multiple vulnerabilities in its NVIDIA App software that can enable attackers to…