WestJet confirms cyberattack exposed IDs, passports in June incident Pierluigi Paganini October 01, 2025 WestJet confirms June cyberattack that disrupted…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning about critical vulnerabilities in Cisco’s IOS and IOS XE…
Biometric technologies were originally designed to improve security and streamline authentication, but they’re often misused in ways most people don’t…
The OpenSSL Project has released a critical security advisory, addressing three significant vulnerabilities that could allow attackers to execute remote…
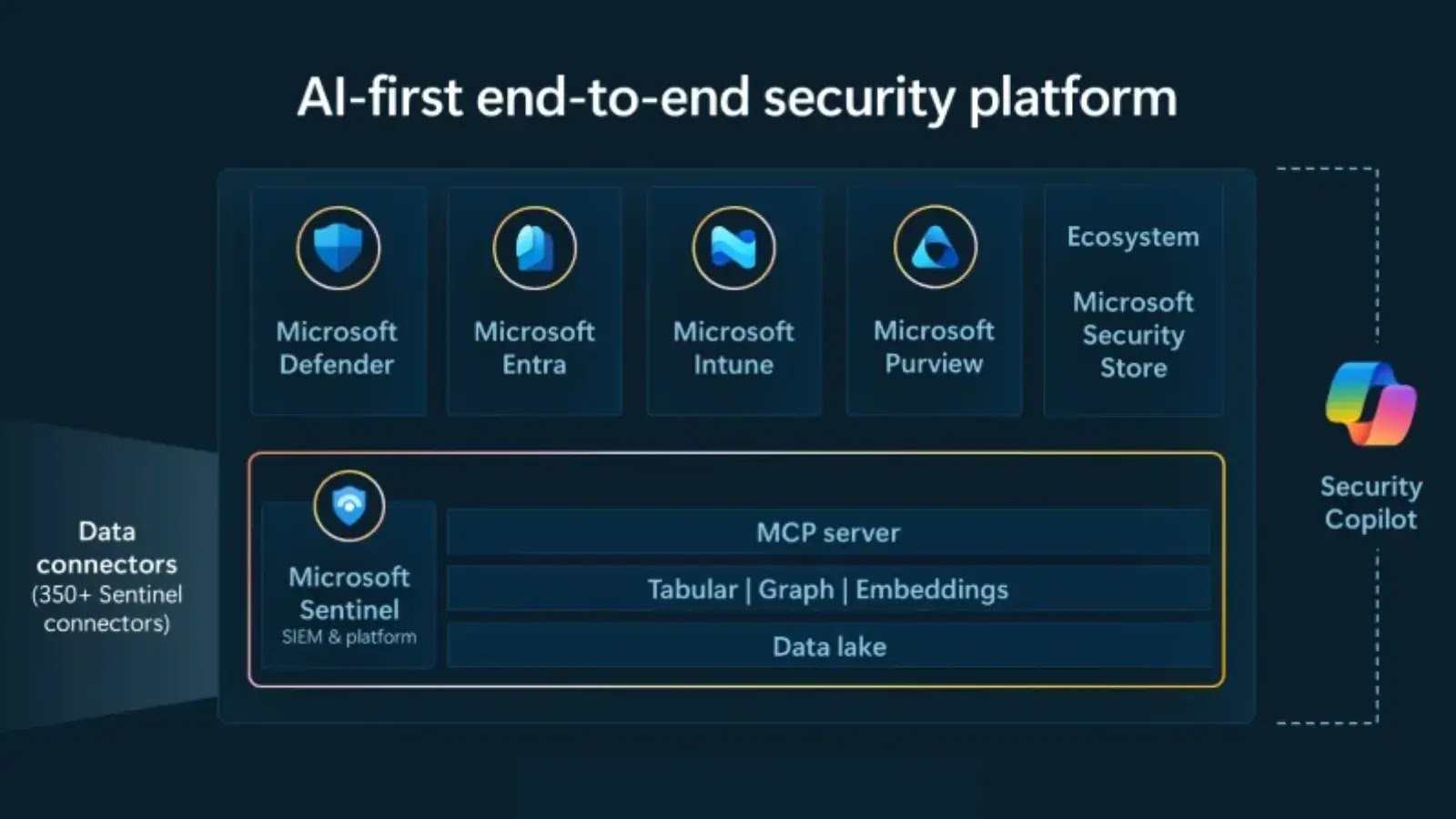
Organizations face an ever-evolving cyberthreat landscape marked by faster, more complex attacks. Today, Microsoft is answering this call with the…
Every time cyber defenders and companies discover new ways to block intrusions, attackers change their tactics and find a way…
A concerning cybersecurity trend has emerged as threat actors exploit the growing popularity of artificial intelligence tools by distributing malicious…
Cybercriminals are turning a trusted file format against users in a sophisticated new attack campaign. MatrixPDF represents a concerning evolution…
AI systems are now deeply embedded in business operations, and this introduces new security risks that traditional controls are not…
Cyber threats are shifting in 2025, and while large companies are still targets, attackers are turning their attention to smaller…
Optus is bringing on consultancy firm Kearney to “provide additional oversight” for its mobile network in the wake of the outages of…
An elusive, persistent, newly confirmed China espionage group has hit almost 10 victims of geopolitical importance in the Middle East,…