The Metropolitan Police has secured a conviction in what they described as the world’s largest cryptocurrency seizure, a case that…
Vulnerability management company Mondoo on Tuesday announced that it has raised $17.5 million in a Series A extension funding round….
Microsoft has released the KB5065789 preview cumulative update for Windows 11 24H2, which includes 41 improvements, including new AI actions…
A security vulnerability in Tesla’s Telematics Control Unit (TCU) allowed attackers with physical access to bypass security measures and gain…
Japanese beer and beverage giant Asahi Group Holdings has been forced to halt production at its domestic factories as a…
30 Sep Talent Shortage: AI-Driven Cybersecurity Requires Skilled Human Oversight Posted at 08:36h in Blogs by Taylor Fox This week…
DeepMind, an AI research laboratory founded in London in 2010, was acquired by Google in 2014. In April 2023, it…
Broadcom has released security updates to patch two high-severity VMware NSX vulnerabilities reported by the U.S. National Security Agency (NSA)….
Lunar Spider, a newly observed malware strain, has emerged as a potent threat to Windows environments by compromising systems in…
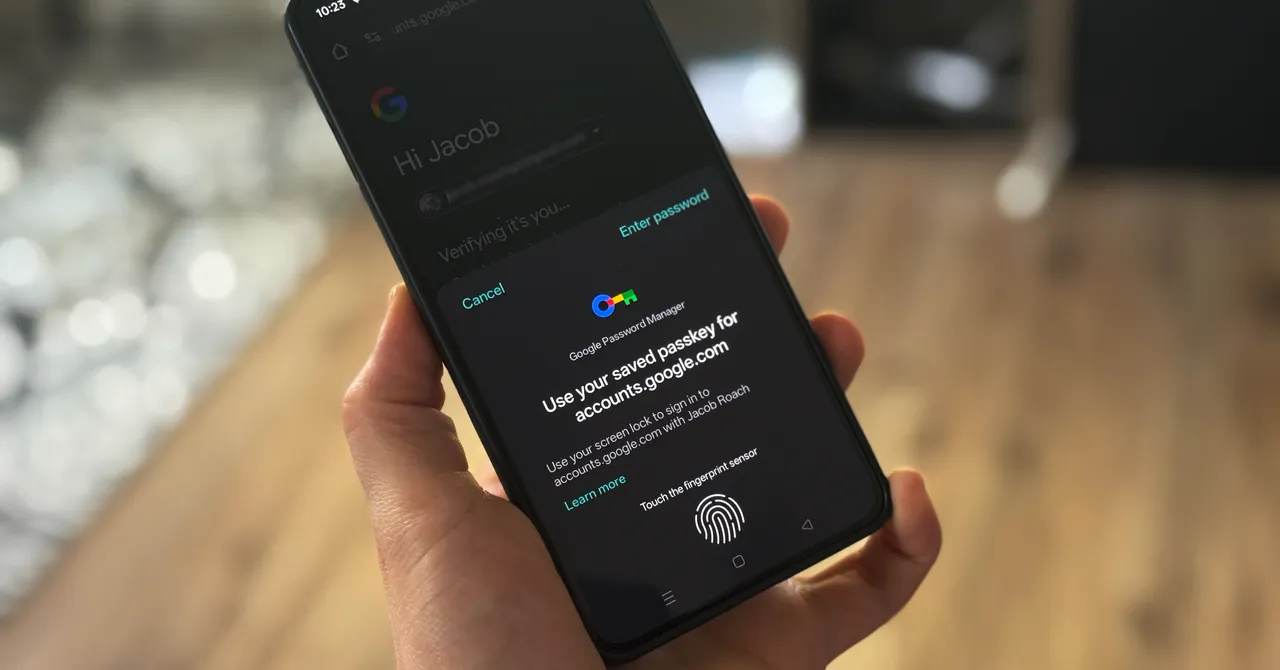
Google wants you to start using passkeys. Its vision is to “progress toward a passwordless future,” allowing you to store…
Cybercriminals are exploiting the growing popularity of artificial intelligence tools by distributing malicious Chrome browser extensions that masquerade as legitimate…
Join Picus Security, SANS, Hacker Valley, and leading CISOs at The BAS Summit 2025 to learn how AI is redefining…