As part of the health service’s 10-year plan, the NHS App is set to become the entry point to an…
Broadcom on Monday announced patches for six vulnerabilities affecting VMware Aria Operations, NSX, vCenter, and VMware Tools products, including four…
Japanese beverage conglomerate Asahi Group Holdings has halted production at its domestic factories following a significant cyberattack that crippled its…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical security alert highlighting the active exploitation of a serious…
Western Digital has fixed a critical remote code execution vulnerability (CVE-2025-30247) in the firmware powering its My Cloud network-attached storage…
Apple has released important security updates to address a critical vulnerability in FontParser—the part of MacOS/iOS/iPadOS that processes fonts. Identified…
A Chinese national has been convicted for her role in a fraudulent cryptocurrency scheme after law enforcement authorities in the…
Few businesses are achieving measurable success with their artificial intelligence (AI) strategy, but those that are appear to be driven…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has expanded its Known Exploited Vulnerabilities (KEV) Catalog by adding five new…
Live Webinar | Tuesday, September 30th at 1PM ET – Register Artificial intelligence is transforming enterprises, but with innovation comes…
The Cybersecurity and Infrastructure Security Agency (CISA) has released an urgent alert for system administrators and IT teams worldwide. Researchers…
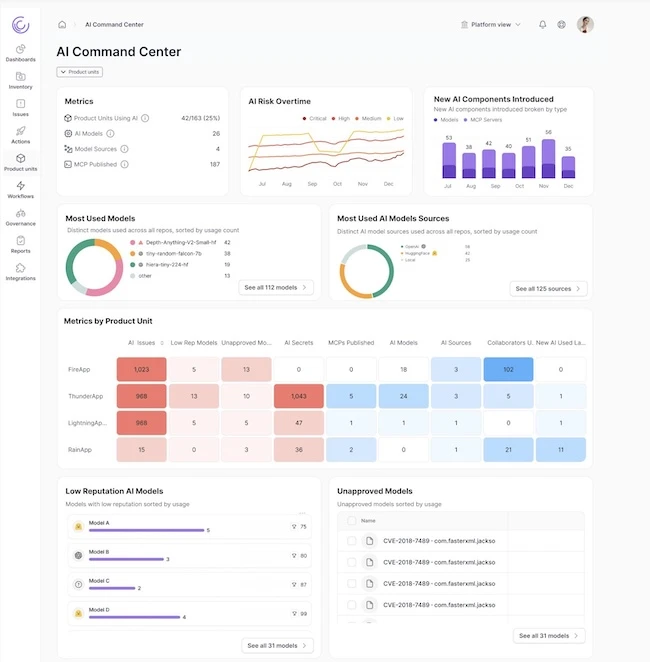
Legit Security has updated its AI Security Command Center. As vibe coding and AI-first development reshape how software is built,…