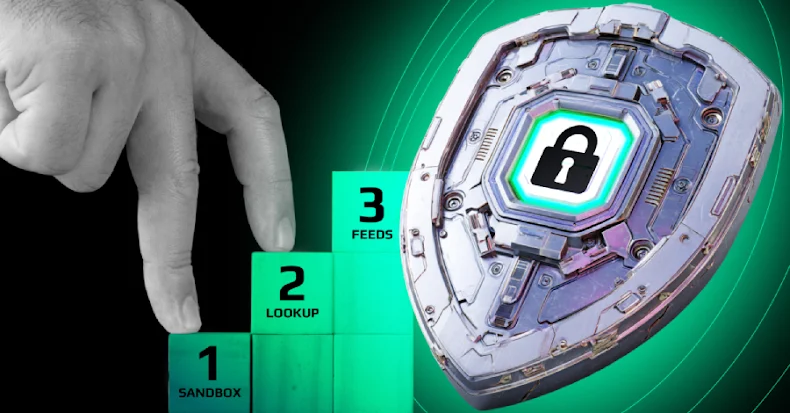
Penetration testing is critical to uncovering real-world security weaknesses. With the shift into continuous testing and validation, it is time…
Canadian airline WestJet is notifying roughly 1.2 million people that their personal information was stolen in a June 2025 cyberattack….
The government has unveiled 14 Regional Tech Booster projects as part of its £1m programme to provide businesses and entrepreneurs…
Dealership software company Motility Software Solutions is notifying over 766,000 people that their personal information was compromised in a ransomware…
An extortion group calling itself the Crimson Collective claims to have breached Red Hat’s private GitHub repositories, stealing nearly 570GB…
Running a SOC often feels like drowning in alerts. Every morning, dashboards light up with thousands of signals; some urgent,…
Cybercrime group claims to have breached Red Hat ‘s private GitHub repositories Pierluigi Paganini October 02, 2025 The cybercrime group…
For this Cybersecurity Awareness Month, we thought it important to draw attention to some of the most common and dangerous…
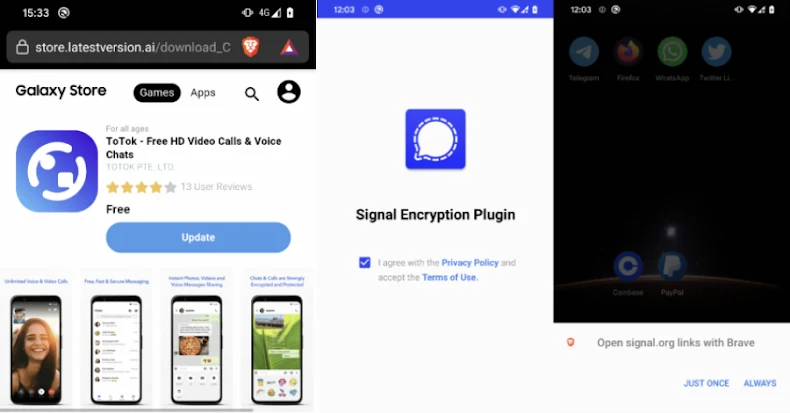
Two new spyware campaigns that researchers call ProSpy and ToSpy lured Android users with fake upgrades or plugins for the…
A new wave of phishing attacks has been detected by the cybersecurity research firm, Blackpoint Cyber, that is exploiting users’…
A significant number of organizations have received extortion emails from hackers who claim to have stolen sensitive information from their…
Cybersecurity researchers have discovered two Android spyware campaigns dubbed ProSpy and ToSpy that impersonate apps like Signal and ToTok to…