UK grants £1.5B loan to Jaguar Land Rover after cyberattack Pierluigi Paganini September 29, 2025 UK grants Jaguar Land Rover…
Asahi Group Holdings, Ltd (Asahi), the brewer of Japan’s top-selling beer, has disclosed a cyberattack that disrupted several of its…
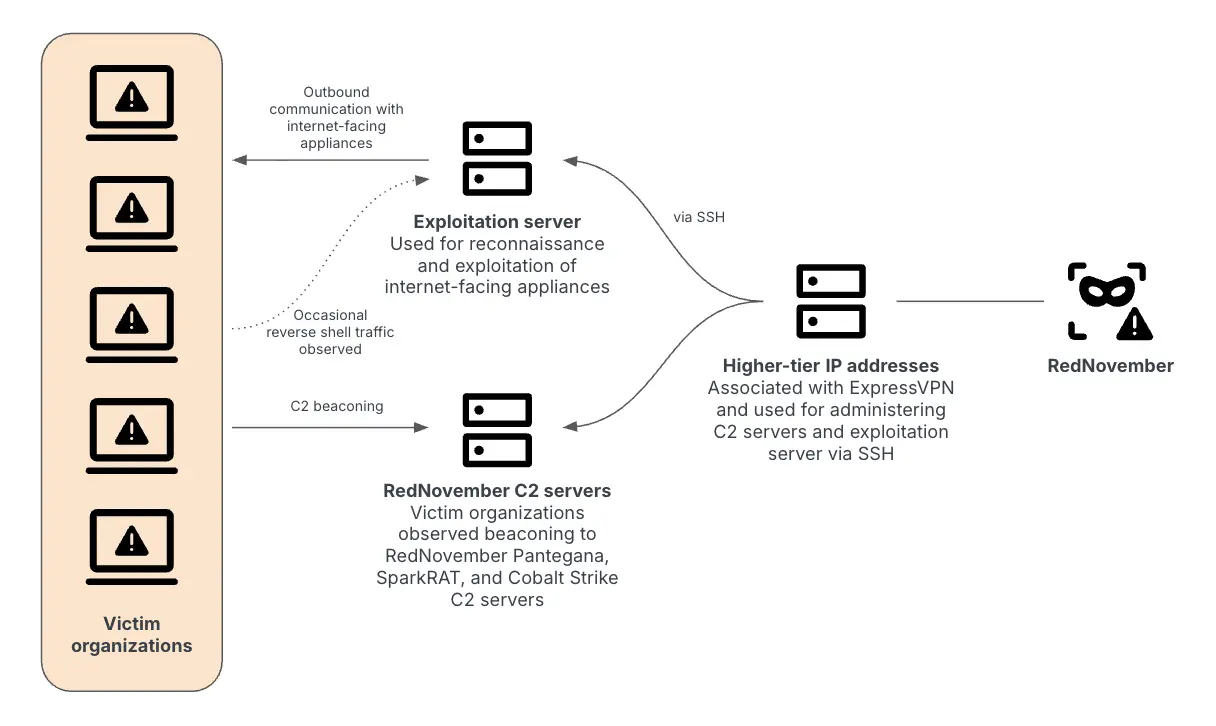
A long-running threat campaign linked to a Chinese state-sponsored cyber-espionage group highlights the importance of patching and protecting edge devices…
Authorities arrested 260 cybercrime suspects during a two-week operation spanning 14 African countries, Interpol announced Friday. The globally coordinated summertime…
Threat actors claiming to represent the Medusa ransomware gang tempted a BBC correspondent to become an insider threat by offering…
The cybersecurity community is currently observing a surge in interest around Olymp Loader, a recently unveiled Malware-as-a-Service (MaaS) platform written…
Two 17-year-old boys from the Netherlands have been arrested on suspicion of spying for pro-Russian hackers, Dutch authorities recently confirmed….
An ongoing campaign of cyber attacks orchestrated through vulnerabilities found in the Cisco Adaptive Security Appliance (ASA) family of unified…
Brave Software, the creator of the privacy-focused web browser and search engine, has introduced a new subsystem called Ask Brave…
A sophisticated cyber campaign is exploiting the trust users place in popular collaboration software, tricking them into downloading a weaponized…
Threat actors have been observed using seemingly legitimate artificial intelligence (AI) tools and software to sneakily slip malware for future…
Finland’s long-term ambition to position itself as the most attractive low-cost Nordic cold climate hub for datacentres could be derailed…