26 Sep The 7 Cybersecurity Trends Of 2026 That Everyone Must Be Ready For Posted at 08:45h in Blogs by…
TechCrunch reports about a “bizarre app” inviting you to record and share your audio calls so that it can sell the…
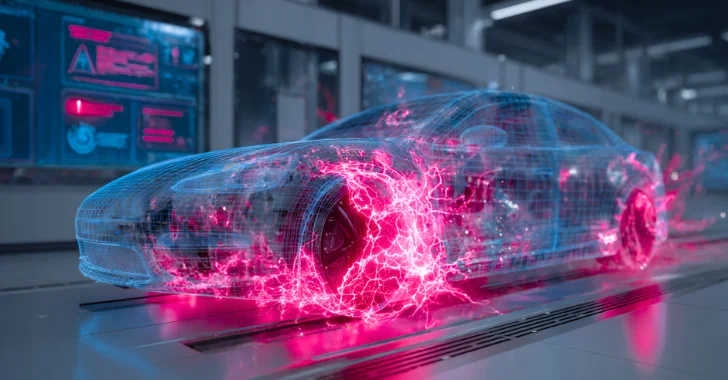
Sep 26, 2025The Hacker NewsSecurity Validation / Enterprise Security Car makers don’t trust blueprints. They smash prototypes into walls. Again…
Australia’s strong economy and high per-capita wealth have made it a prime target for ransomware groups, with the country facing…
Microsoft said Thursday it had disabled services to a unit within the Israeli military after a company review had determined…
The first-ever malicious Model-Context-Prompt (MCP) server discovered in the wild, a trojanized npm package named postmark-mcp that has been secretly…
Sep 26, 2025The Hacker NewsSecurity Validation / Enterprise Security Car makers don’t trust blueprints. They smash prototypes into walls. Again…
The North Korean threat actor behind the DeceptiveDevelopment campaign is supplying stolen developer information to the country’s horde of fraudulent…
UK NCSC warns that attackers exploited Cisco firewall zero-days to deploy RayInitiator and LINE VIPER malware Pierluigi Paganini September 26,…
Active Directory (AD) remains the foundation of authentication and authorization in Windows environments. Threat actors targeting the NTDS.dit database can harvest…
Malware operators aligned with North Korea have forged a sophisticated partnership with covert IT workers to target corporate organizations worldwide….
A widespread campaign aimed at breaching organizations via zero-day vulnerabilities in Cisco Adaptive Security Appliances (ASA) has been revealed by…