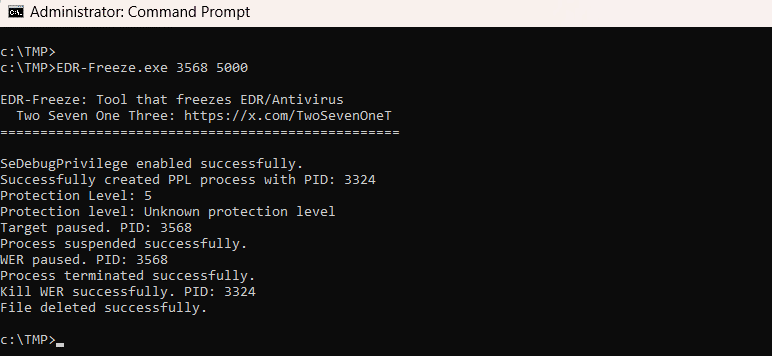
Endpoint detection and response (EDR) bypass and evasion tools and techniques are commonly used by threat and ransomware groups to…
Cisco has disclosed a zero-day vulnerability, CVE-2025-20352, in its widely used IOS and IOS XE software, confirming it is being…
British authorities arrested a man in his 40s from West Sussex in connection with a ransomware incident that knocked out…
Kali Linux has released version 2025.3, the third version of 2025, featuring ten new tools, Nexmon support, and NetHunter improvements….
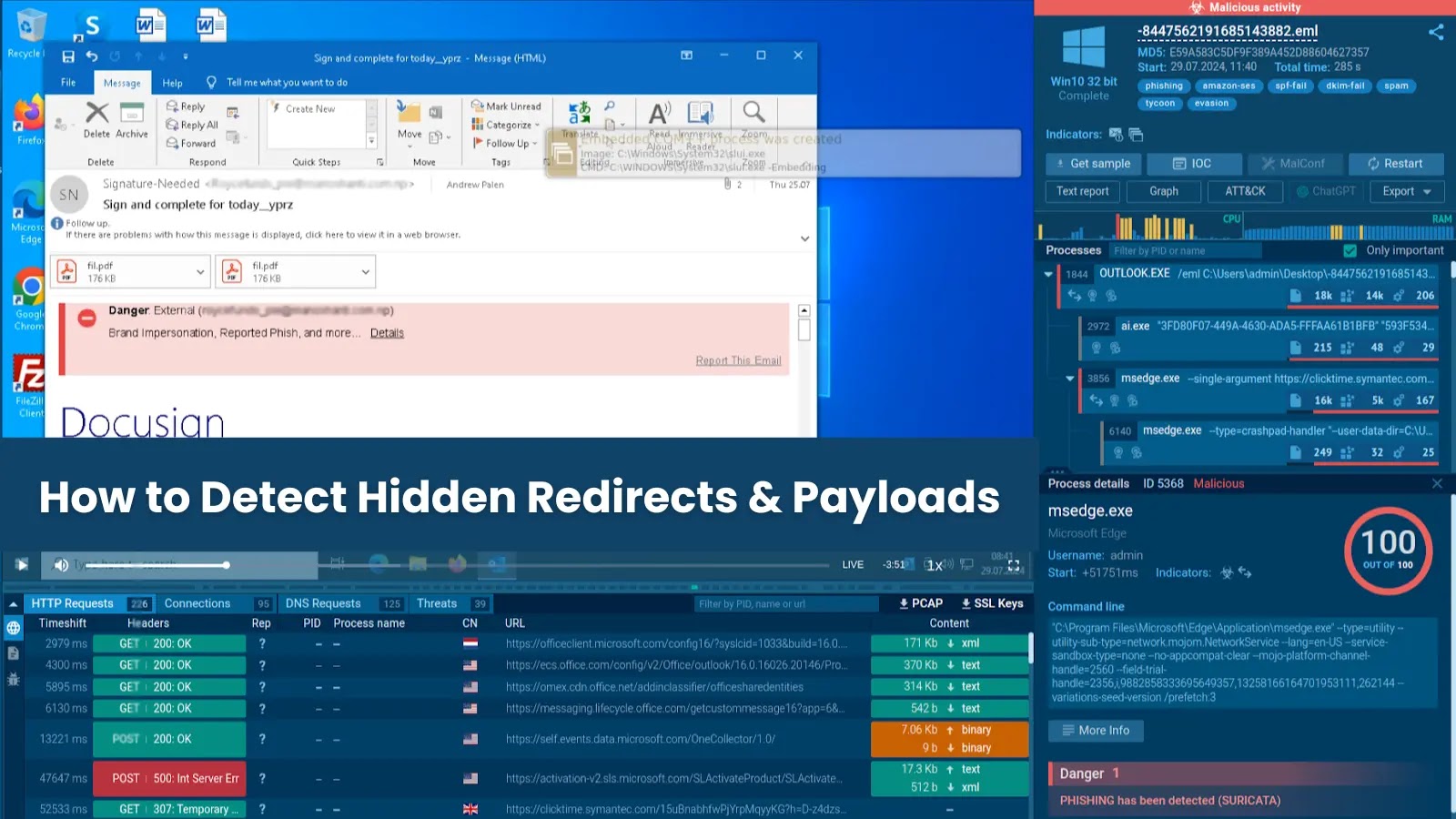
Phishing campaigns are getting harder to spot, sometimes hiding in files you’d never suspect. ANY.RUN’s cybersecurity analysts recently uncovered one…
Suspected Chinese hackers have used the Brickstorm malware in long-term persistence espionage operations against U.S. organizations in the technology and…
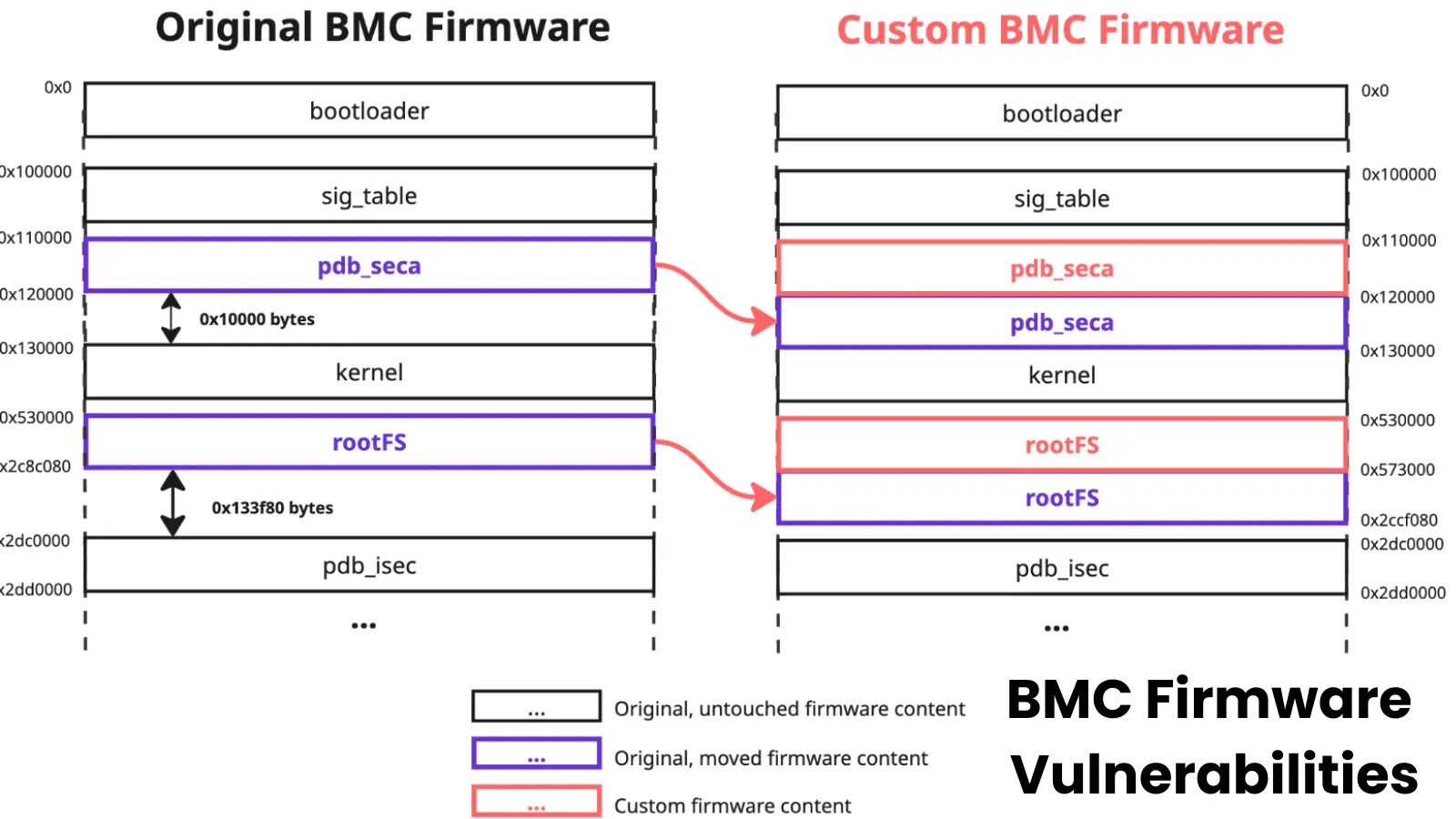
In January 2025, Supermicro released patches addressing critical vulnerabilities in its Baseboard Management Controller (BMC) firmware validation logic. Despite these…
The Python Software Foundation (PSF) is warning developers about a fresh phishing campaign that targets users of the Python Package…
Sep 24, 2025Ravie LakshmananVulnerability / Network Security A suspected cyber espionage activity cluster that was previously found targeting global government…
Cisco has released security updates to address a high-severity zero-day vulnerability in Cisco IOS and IOS XE Software that is…
A new study has uncovered a method for silently installing custom extensions on Chromium-based browsers running in Windows domain environments….
The National Crime Agency (NCA) has arrested and released on bail a man in his forties in connection with the…