In this Help Net Security interview, Fred Kwong, VP, CISO at DeVry University, outlines how the university balances academic openness…
Odido Data Breach A major data breach has hit Odido, one of the Netherlands’ prominent telecommunications providers, with cybercriminals publishing…
Microsoft Defender researchers have uncovered a new campaign that abuses trojanized gaming utilities to deliver multi‑stage malware with remote access,…
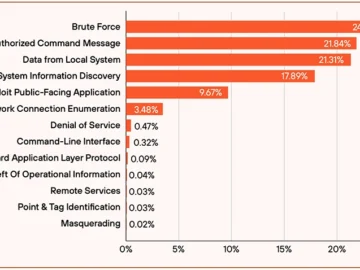
Industrial operators continue to run remote access portals, building automation servers, and other operational technology services on public IP address…
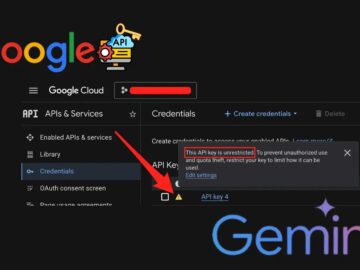
Security researchers at Truffle Security discovered that legacy public-facing Google API keys can silently gain unauthorized access to Google’s sensitive…
Here’s a look at the most interesting products from the past month, featuring releases from Aikido Security, Avast, Armis, Black…
In response, the Women in Cyber Security Summit is returning for its second year. Bigger, bolder, and more determined to…
Madhu Gottumukkala is out as acting director of the Cybersecurity and Infrastructure Security Agency, with current agency executive director for…
Researchers have devised a method that allows large language models (LLMs) to strip anonymity from pseudonymous online accounts at scale…
A critical privilege escalation vulnerability affecting Google Cloud API keys specifically how legacy public-facing keys now silently grant unauthorized access…
Trend Micro fixes two critical flaws in Apex One Pierluigi Paganini February 26, 2026 Trend Micro fixed two critical Apex…
A global law enforcement effort has taken root to combat The Com, a sprawling nihilistic network of thousands of minors…