Sep 23, 2025Ravie LakshmananSEO Poisoning / Malware Cybersecurity researchers are calling attention to a search engine optimization (SEO) poisoning campaign…
On Wednesday, Angus McCullough KC will publish a report that promises to be one of the most consequential examinations of…
Car manufacturing giant Stellantis has disclosed a data breach involving a third-party service provider’s platform. The incident, the company said…
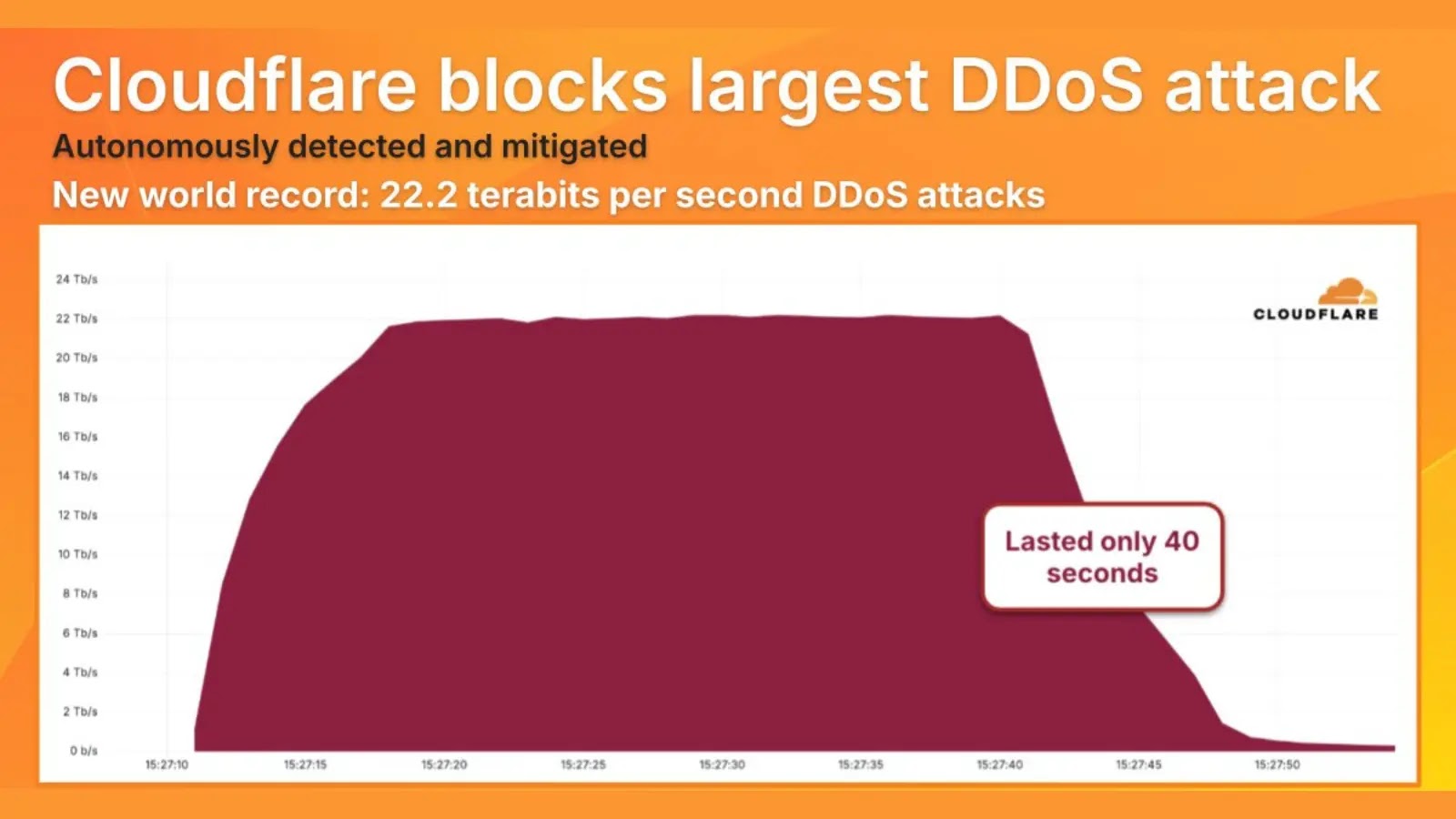
Cloudflare announced today that it has successfully mitigated the largest distributed denial-of-service (DDoS) attack ever recorded. The hyper-volumetric assault peaked…
Canada’s RCMP closes TradeOgre, seizes $40M in country’s largest crypto bust Pierluigi Paganini September 23, 2025 RCMP shuts down TradeOgre,…
Over the weekend, a sophisticated ransomware attack compromised Collins Aerospace’s Muse check-in and boarding systems, forcing key hubs including Heathrow,…
A critical security flaw in Libraesva ESG email security gateways has been identified and patched, allowing threat actors to execute…
Passengers across Europe are facing another day of flight delays after a cyber-attack struck the company behind the check-in and…
Application Security Engineer PayPal | USA | On-site – View job details As an Application Security Engineer, you will apply…
Cloudflare announced it had autonomously mitigated the largest distributed denial-of-service (DDoS) attack ever recorded. The hyper-volumetric attack peaked at an…
Cybersecurity researchers have uncovered a new phishing campaign that exploits GitHub’s official notification system to deliver malicious links and credential-stealing…
Regardless of their size, all law firms hold valuable data, including client communications, financial records, and confidential legal strategies. That…