Google will integrate Gemini into its Chrome browser for users in the US just weeks after a federal judge spared…
The University of Sydney has kicked off recruitment for a permanent chief information security officer following the departure of Steven Bennett…
ShadowLeak: Radware Uncovers Zero-Click Attack on ChatGPT Pierluigi Paganini September 18, 2025 Radware discovered a server-side data theft attack, dubbed…
The problems echo a broader pattern across the country, where watchdogs and courts have flagged overcrowding, poor sanitation, and blocked…
Now, especially in a very competitive environment, it is essential to make your name shine. Enterprise SEO solutions are crucial…
OpenAI is finally rolling out a toggle that allows you to decide how hard the GPT-5-thinking model can think. This…
The cyberthreat landscape has witnessed the emergence of another sophisticated ransomware operation as GOLD SALEM, a new threat actor group…
Federal agencies are increasingly incorporating artificial intelligence into the cyberdefenses of government networks, and there’s more still to come, acting…
The Russian covert influence network CopyCop has significantly expanded its disinformation campaign, establishing over 200 new fictional media websites since…
Qilin remained the top ransomware group in August, but two rapidly emerging competitors are threatening to shake up the threat…
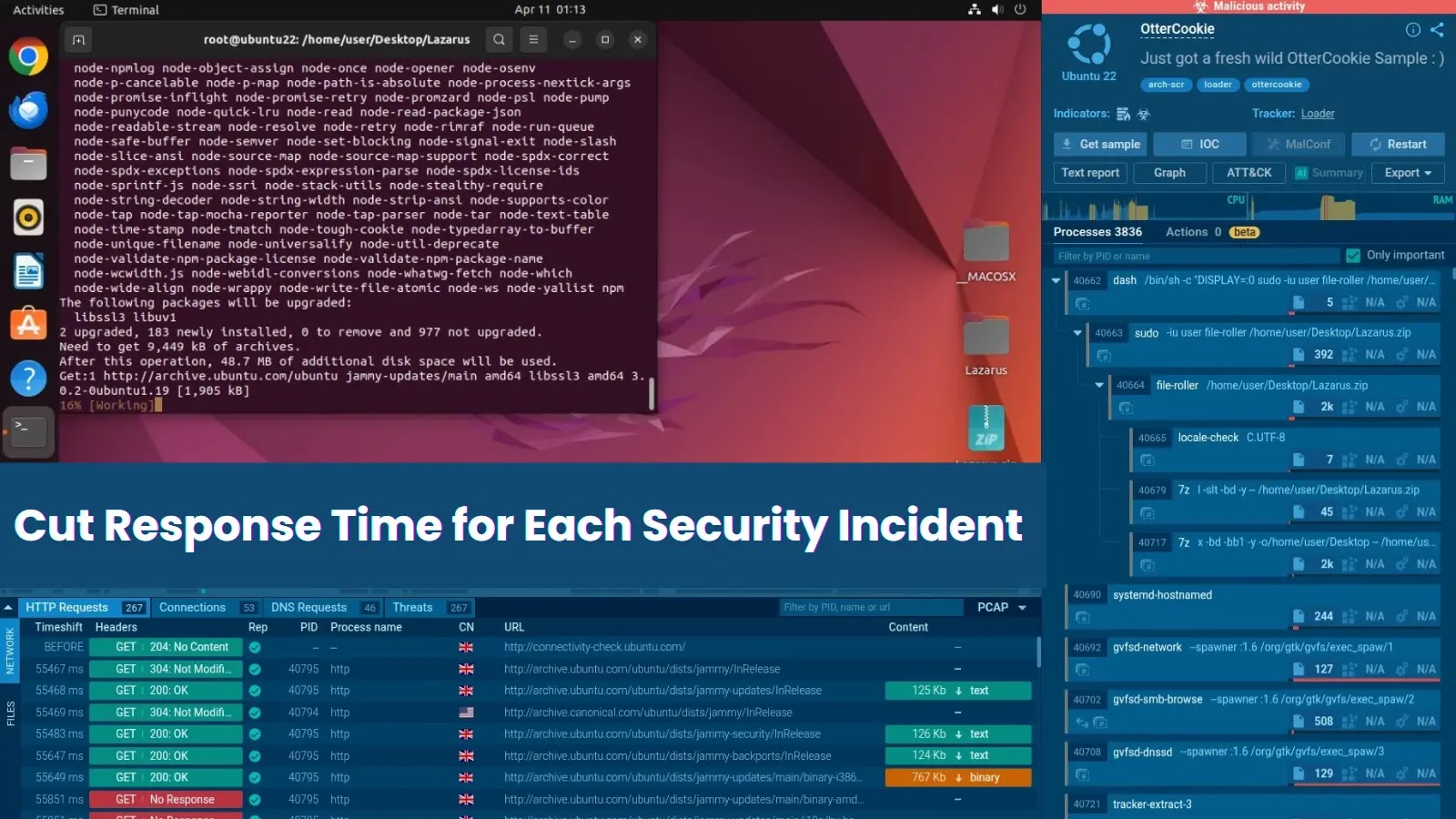
When an incident happens, there’s no time to waste. SOC teams must react fast to protect their organization, and this…
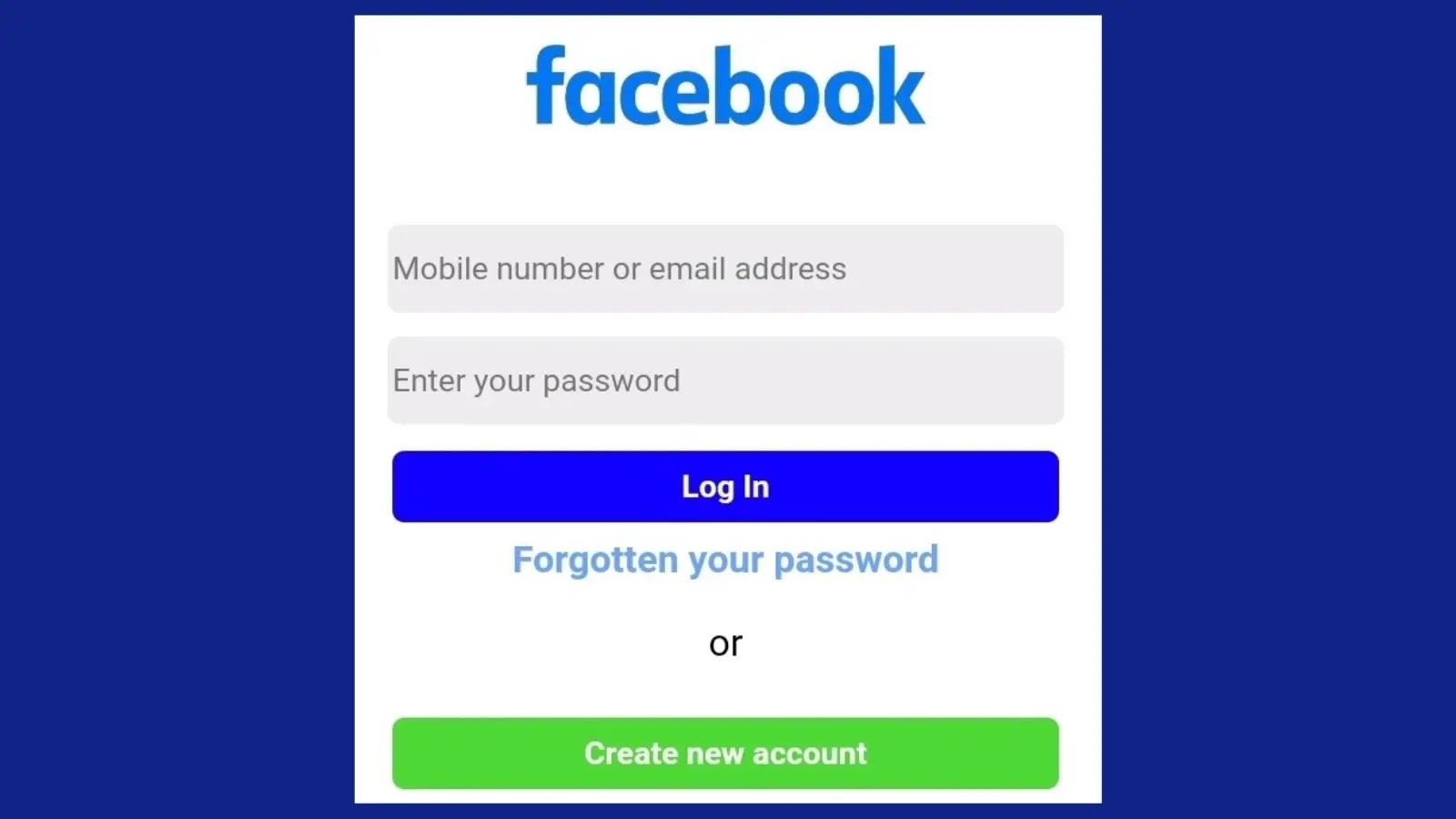
A newly discovered phishing campaign is exploiting Facebook’s external URL warning feature to dupe users into handing over their login…