Education can be an incredibly rewarding but demanding profession, as the workload of teachers is ever increasing. The progress of…
UK authorities have arrested a 19-year-old UK national alleged to be a key figure in the Scattered LAPSUS$ Hunters threat…
Listen to the article 2 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
Microsoft 365 has become the central nervous system of modern business — and cybercriminals know it. Just as Windows became…
SquareX first discovered and disclosed Last Mile Reassembly attacks at DEF CON 32 last year, warning the security community of…
EclecticIQ analysts assess with high confidence that ShinyHunters is expanding its operations by combining AI-enabled voice phishing, supply chain compromises,…
Artificial intelligence (AI) and AI agents are seemingly everywhere. Be it with conference show floors or television adverts featuring celebrities,…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. British authorities…
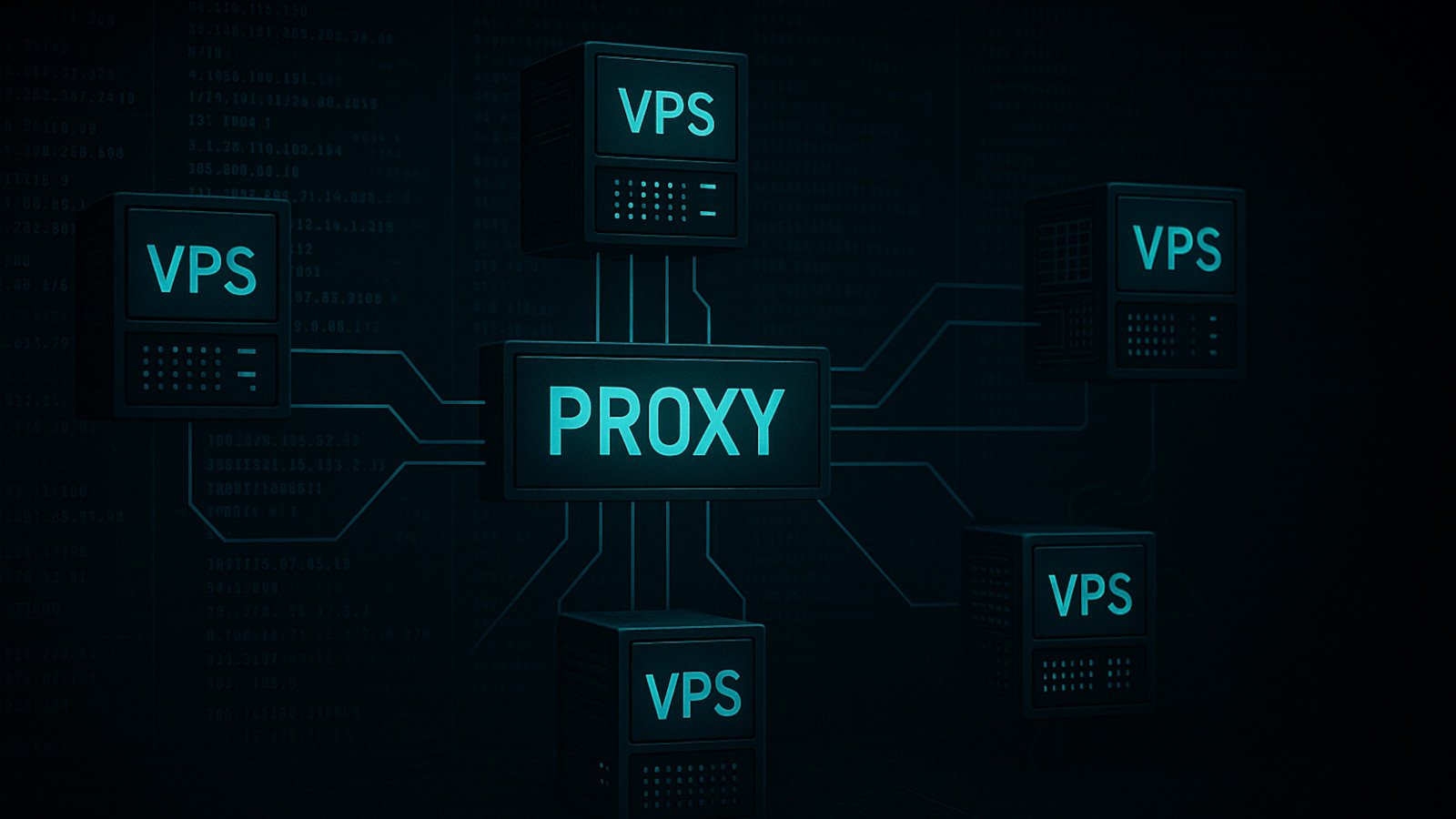
The operators of the SystemBC proxy botnet are hunting for vulnerable commercial virtual private servers (VPS) and maintain an average…
A zero-click vulnerability discovered in ChatGPT’s Deep Research agent allowed attackers to exfiltrate sensitive data from a user’s Gmail account…
“Necessity is the mother of invention” has never been more fitting—whether you’re talking about America’s post-WWII highway boom or the…
As businesses around the world have shifted their digital infrastructure over the last decade from self-hosted servers to the cloud,…