WatchGuard released an advisory detailing a critical vulnerability in its Firebox line of network security appliances. Tracked as CVE-2025-9242, the…
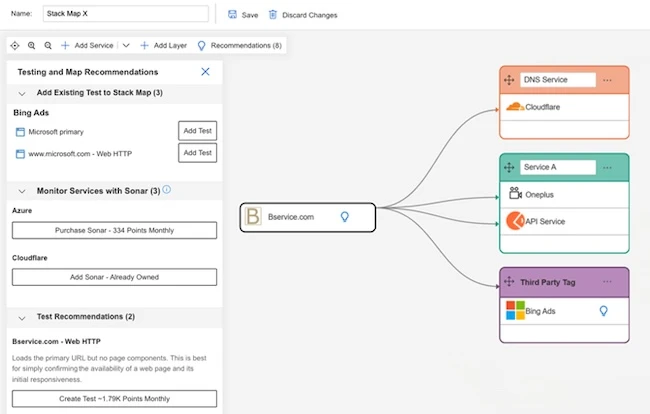
Catchpoint released two AI-powered capabilities designed to simplify digital resilience for critical applications: Catchpoint Root Cause Analysis (RCA) and Catchpoint…
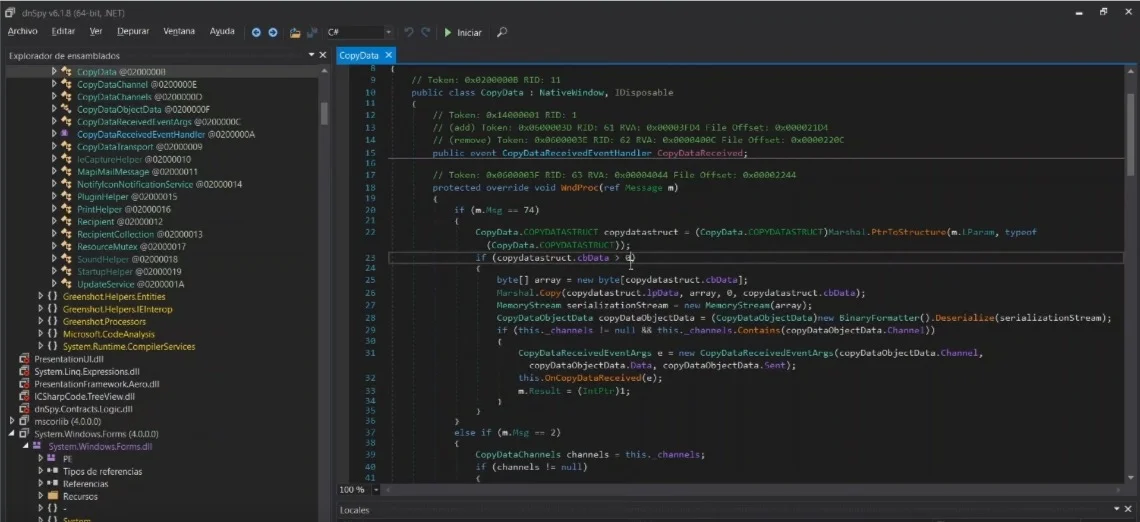
A security vulnerability has been discovered in Greenshot, the widely used open-source screenshot tool for Windows. The Greenshot vulnerability exposes…
Venture capital firm Insight Partners has revealed that the data breach disclosed earlier this year was the result of a…
A critical zero-day remote code execution (RCE) vulnerability, identified as CVE-2025-9961, has been discovered in TP-Link routers. Security research firm…
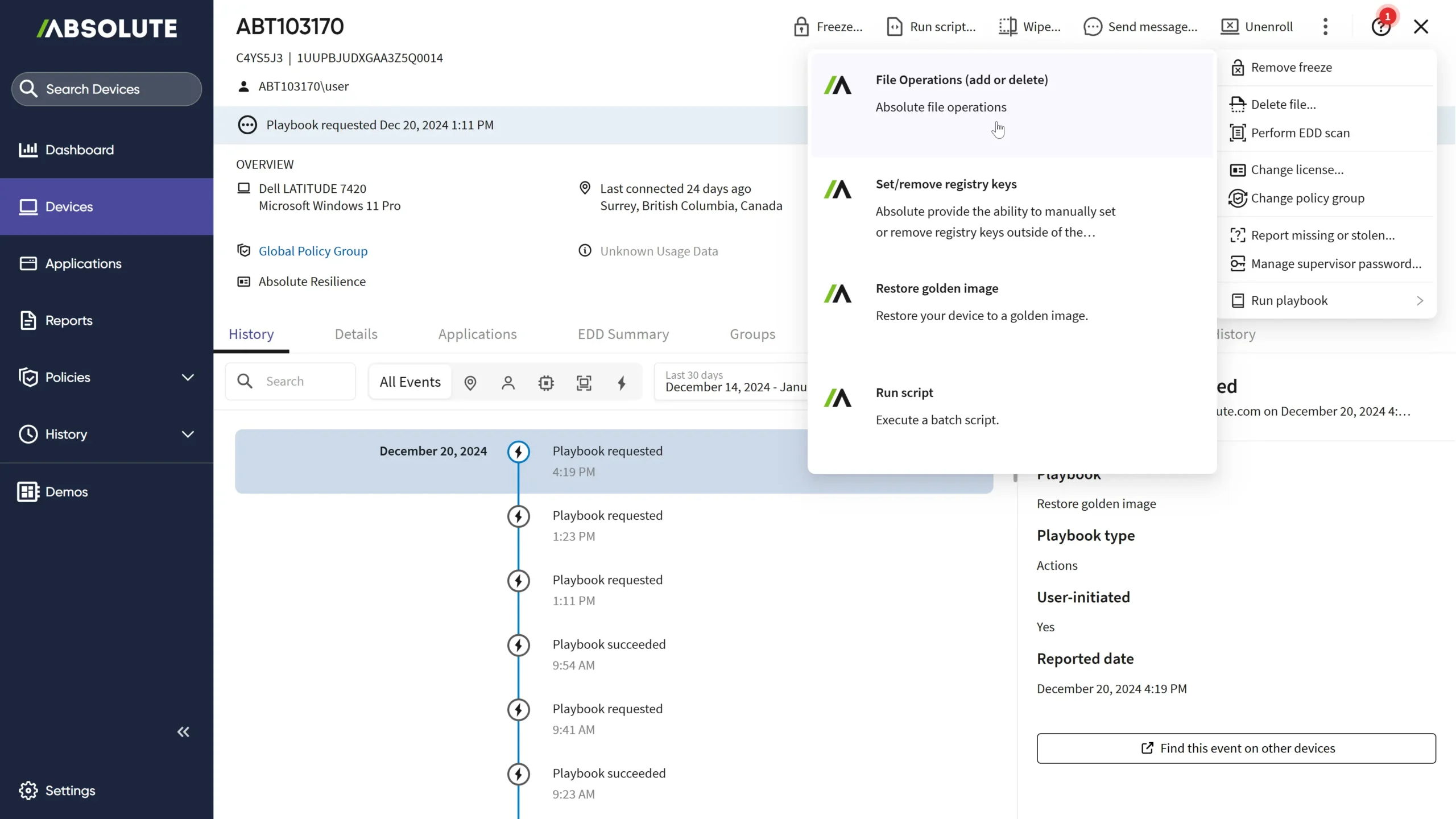
Absolute Security released Rehydrate, empowering enterprises to recover from IT or cyber incidents remotely and at scale to minimize operational…
Sep 18, 2025Ravie LakshmananVulnerability / Browser Security Google on Wednesday released security updates for the Chrome web browser to address…
The newly publicized Pixie Dust attack has once again exposed the critical vulnerabilities inherent in the Wi-Fi Protected Setup (WPS)…
On August 4, 2025, Zscaler ThreatLabz uncovered two malicious Python packages—sisaws and secmeasure—that deliver SilentSync, a Python-based remote access trojan…
In this Help Net Security interview, Daniel Stenberg, lead developer od cURL, discusses how the widely used tool remains secure…
Cybersecurity researchers at Varonis Threat Labs have uncovered a persistent vulnerability that has remained unaddressed for over a decade, allowing…
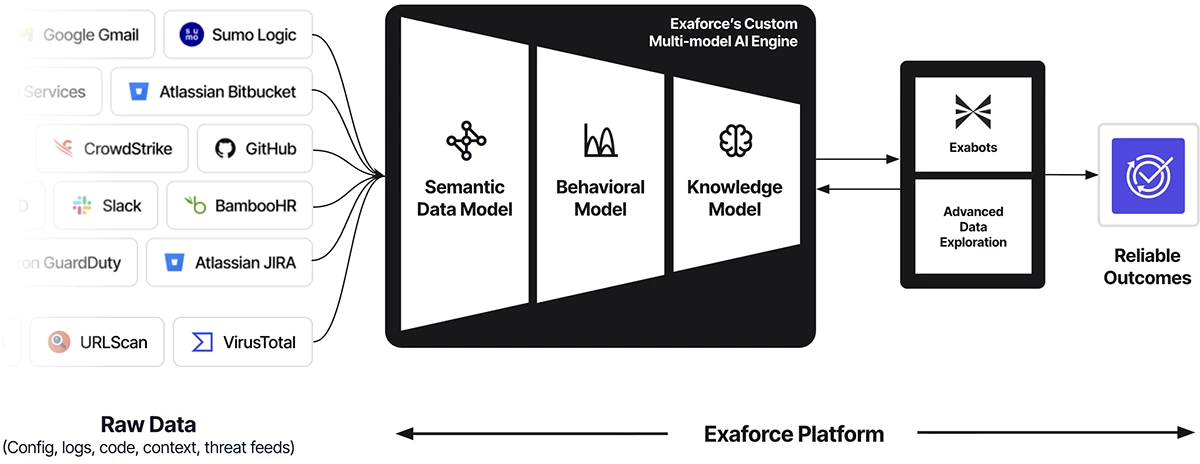
Today’s SOCs face an impossible equation: too much noise, too many gaps, and too few hands. Detection coverage gaps leave…