UNSW Sydney has bought 10,000 licences of ChatGPT Edu for all fixed-term and permanent staff, in what’s being touted as…
In this Help Net Security video, Jérôme Segura, VP of Threat Research at Datadome, explains why intent, not just identifying…
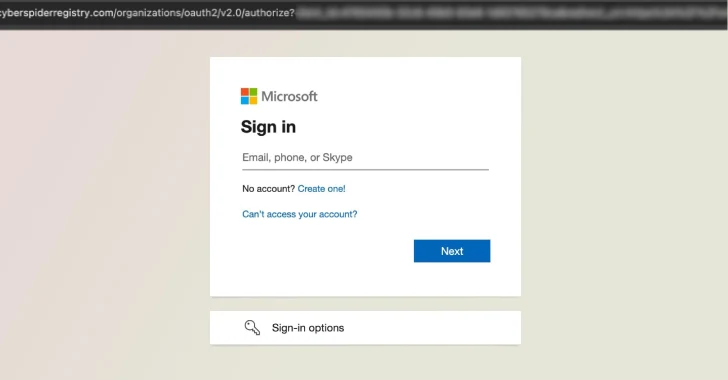
Microsoft’s Digital Crimes Unit said it teamed up with Cloudflare to coordinate the seizure of 338 domains used by RaccoonO365,…
Environment Protection Authority (EPA) Victoria is using SAP SuccessFactors to underpin a strategic workforce planning initiative, assembling a “talent pool”…
Attackers are finding new ways to blend in with everyday business tools, hiding their activity inside formats and processes that…
The NSW government is to overhaul how it sources and manages whole-of-government infrastructure and core technology services, in a move…
Ever-improving security tools have become critical to ensuring business resilience, but a technical expert has warned that many companies are…
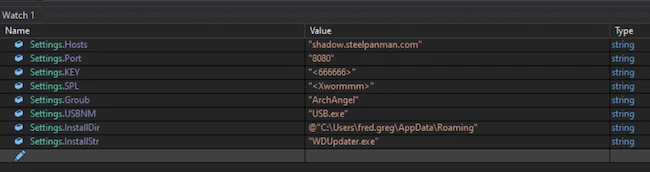
A new supply chain attack on npm, the node package manager, has injected the first malware with self-replicating worm behaviour…
Australia urged social media platforms to employ “minimally invasive” methods to check the age of users covered by its world-first…
Medibank has gone live with SuccessFactors-powered enterprise service management, with the ambition to set it up as a single system…
CrowdStrike on Tuesday said that it would acquire Pangea, a company specializing in AI security, to expand its Falcon platform…
A man who pleaded guilty in 2023 for charges related to his work as founder and operator of the notorious…