Other VPNs We’ve Tested Private Internet Access (PIA) has a long history in the VPN space, and it’s maintained a…
RevengeHotels, also known as TA558, has escalated its long-standing cybercrime campaign by incorporating artificial intelligence into its infection chains, deploying…
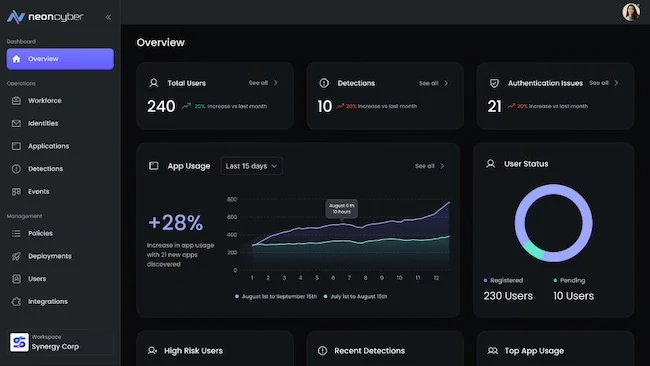
Neon Cyber announced its emergence from stealth and unveiled the first Workforce Cybersecurity Platform (WCP), delivering protection across browsers, SaaS…
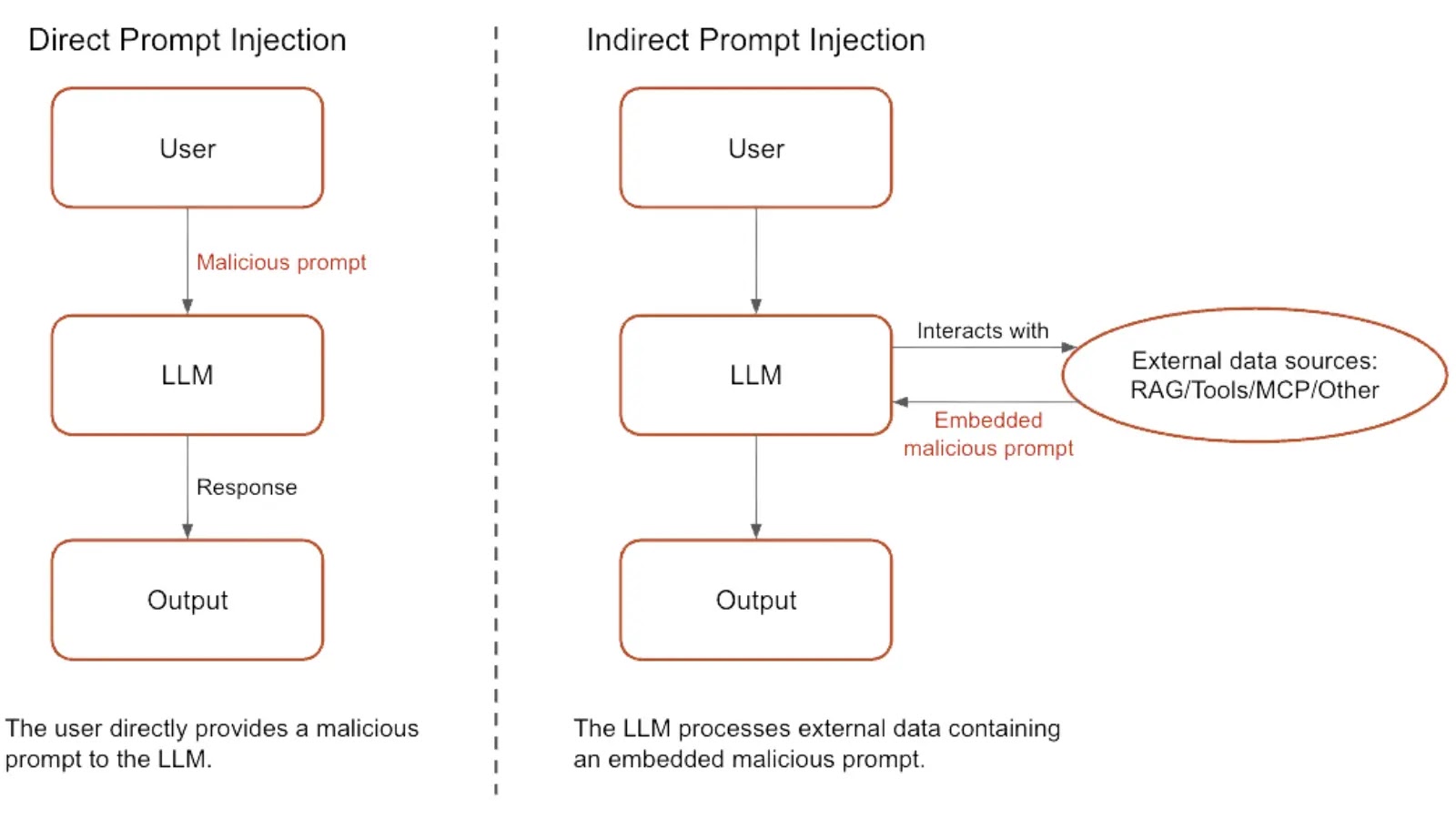
If you are under the impression that cybercriminals need to get their hands on compromised AI chatbots to help them…
The National Grid will pilot the use of a technology that promises to allow artificial intelligence (AI) datacentres to flexibly…
Constant visibility and security of data with the right level of security to maintain safe operational use. Tel Aviv, Israel-based…
Jaguar Land Rover (JLR) announced today that it will extend the production shutdown for another week, following a devastating cyberattack…
Modern development workflows increasingly rely on AI-driven coding assistants to accelerate software delivery and improve code quality. However, recent research…
AI code assistants integrated into IDEs, like GitHub Copilot, offer powerful chat, auto-completion, and test-generation features. However, threat actors and…
Source code is a critical asset for every company, and platforms like GitHub and Atlassian serve as secure vaults for it. Organizations…
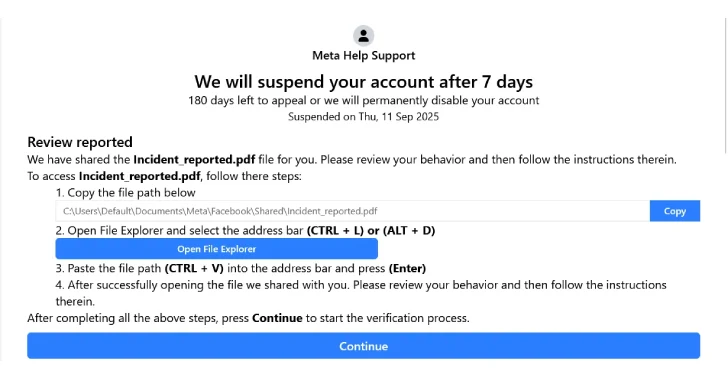
Sep 16, 2025Ravie LakshmananMalware / Social Engineering Cybersecurity researchers have warned of a new campaign that’s leveraging a variant of…
Turkey has tightened government control over telecommunications in recent weeks, preceding its moves with official statistics that seemed to vindicate…