Sep 16, 2025The Hacker NewsAI Security / Enterprise Security AI agents are rapidly becoming a core part of the enterprise,…
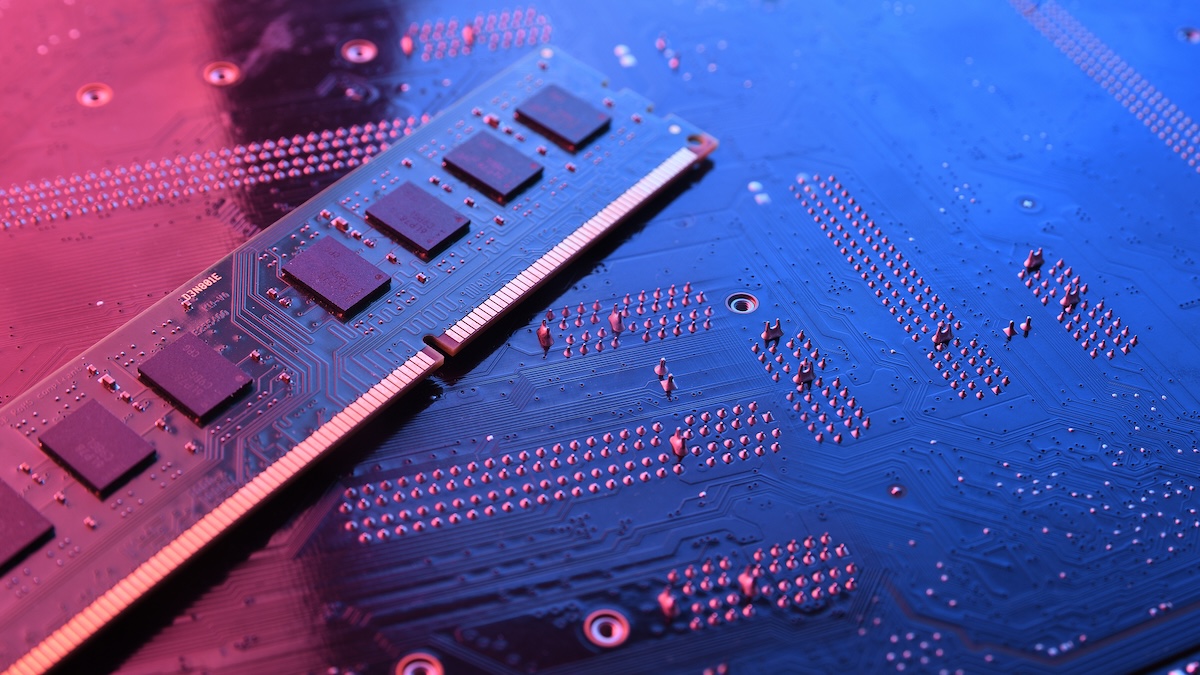
A group of security researchers from the ETH Zurich university and Google have demonstrated a practical Rowhammer attack against DDR5….
A critical authentication bypass vulnerability in the Case Theme User WordPress plugin has emerged as a significant security threat, allowing…
As more companies move their critical systems and data to Amazon Web Services (AWS), attackers are finding new ways to…
Las Vegas, United States, September 16th, 2025, CyberNewsWire Seraphic today announced at Fal.Con 2025 that its Secure Enterprise Browser (SEB)…
Sep 16, 2025Ravie LakshmananVulnerability / Spyware Apple on Monday backported fixes for a recently patched security flaw that has been…
Neon Cyber’s purpose is to move the focus of current cybersecurity from the infrastructure to the workforce. The company emerged…
Attackers are increasingly leveraging sophisticated techniques to maintain long-term access in cloud environments, and a newly surfaced tool named AWSDoor…
A critical vulnerability in the Case Theme User plugin for WordPress allows unauthenticated attackers to hijack any account on vulnerable…
As if ransomware wasn’t enough of a security problem for the sector, educational institutions also need to worry about their…
Startup Carbon3.ai is on a mission to help the UK government achieve its goal of building a sustainable and sovereign…
A new ChatGPT calendar integration can be abused to execute an attacker’s commands, and researchers at AI security firm EdisonWatch…