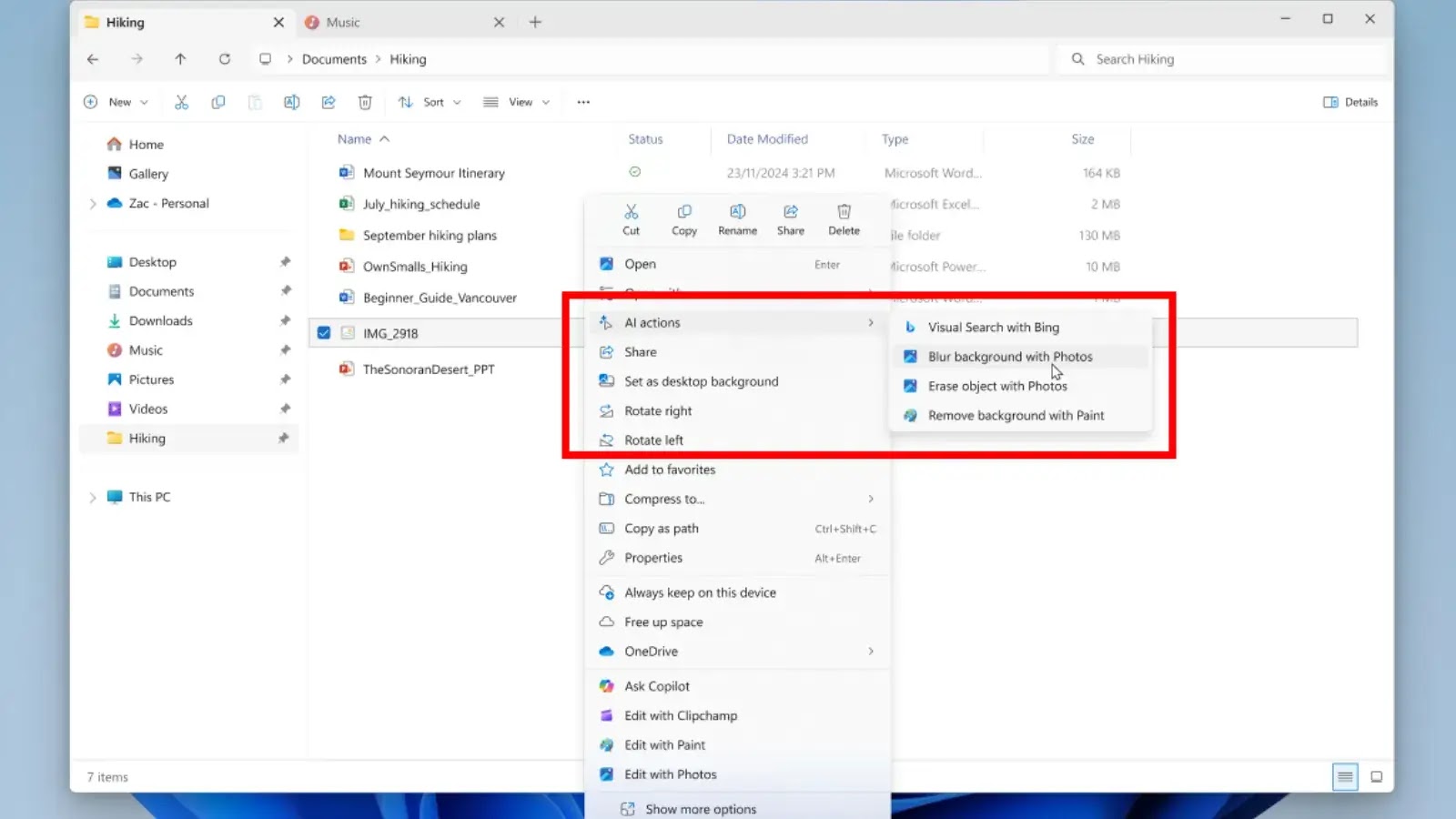
Microsoft is rolling out AI-powered actions in File Explorer, allowing users to interact with files more deeply without leaving the folder…
Accountancy firm Grant Thornton Australia has consolidated 60 terabytes of backup and disaster recovery data into Veeam over the past…
Meta is being sued by its former head of security, who claims the company ignored repeated warnings that its messaging…
Microsoft has released the KB5065429 cumulative update for Windows 10 22H2 and Windows 10 21H2, with fourteen fixes or changes, including…
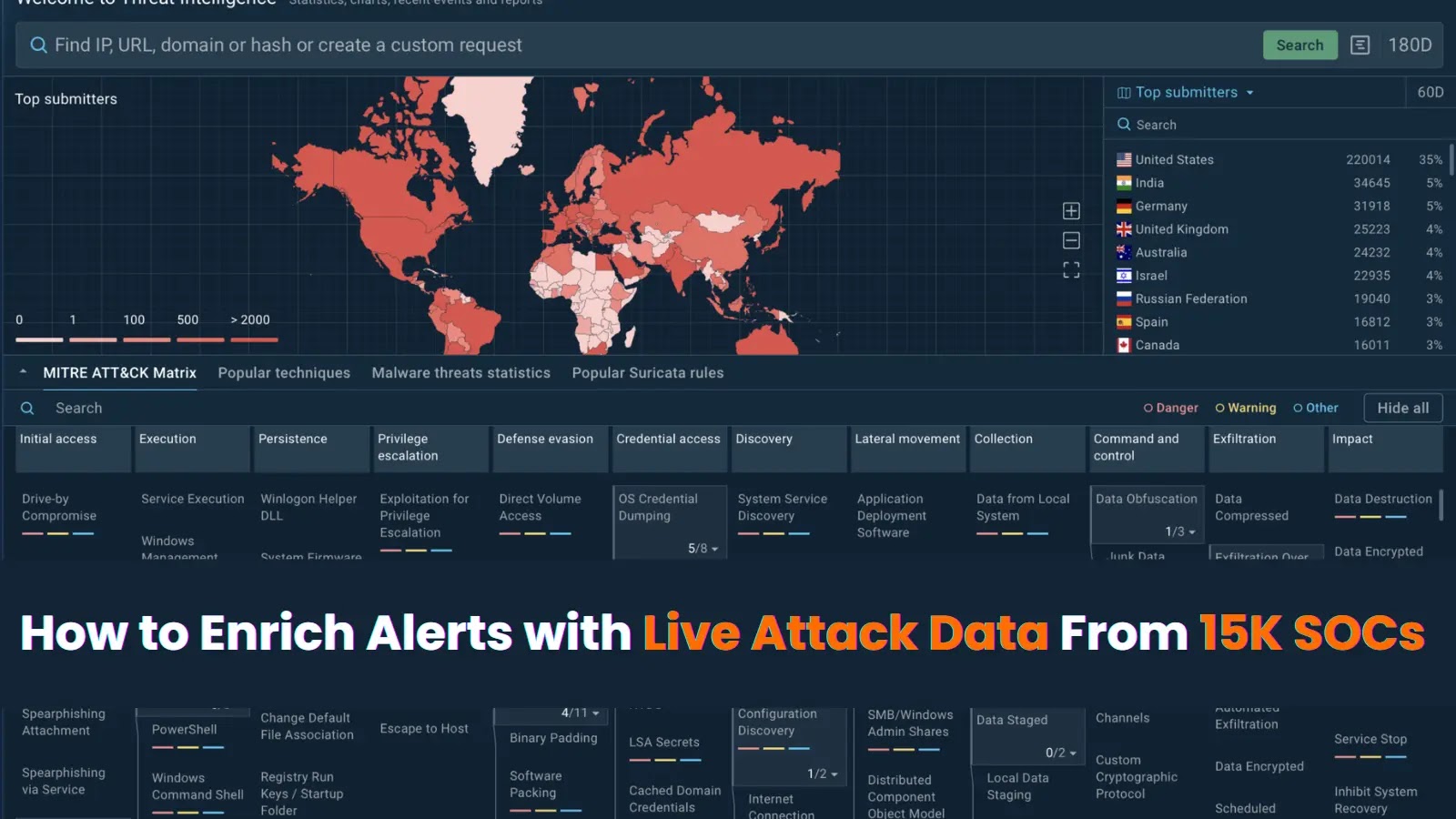
Every SOC analyst knows the frustration. Your SIEM generates hundreds, sometimes thousands of alerts daily. Each alert demands attention, but…
Microsoft has released its September 2025 Patch Tuesday update, addressing a total of 81 security vulnerabilities across its product portfolio….
Kosovo national Liridon Masurica has pleaded guilty to running BlackDB.cc, a cybercrime marketplace that has been active since 2018. Kosovar…
Ivanti has released security updates to address two high-severity vulnerabilities in its Endpoint Manager (EPM) software that could allow remote…
Zoom has released an urgent security update for its Windows client and Workplace platform to address multiple flaws, including a…
Cyble threat intelligence researchers have identified a sophisticated Linux botnet built for cryptocurrency mining, remote command execution, and dozens of…
Bridgestone Americas is continuing to investigate a cyberattack that disrupted operations at certain facilities and said it expects to return…
Adobe is warning of a critical vulnerability (CVE-2025-54236) in its Commerce and Magento Open Source platforms that researchers call SessionReaper…