Apple has released a comprehensive security update for iOS 26 and iPadOS 26, addressing 27 vulnerabilities across multiple system components. The update,…
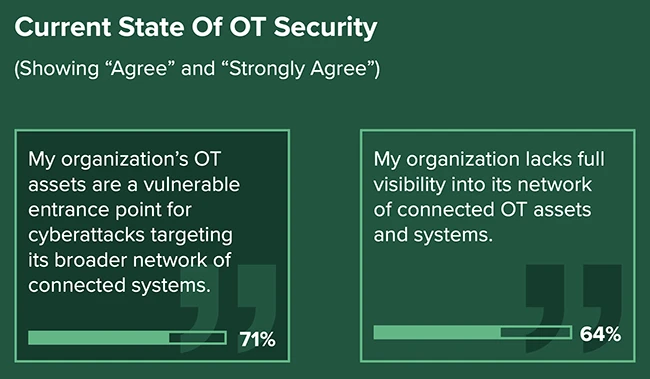
Cyberattacks keep hitting the OT systems that critical infrastructure operators run, according to new research from Forrester. In a survey…
Sep 16, 2025Ravie LakshmananHardware Security / Vulnerability A team of academics from ETH Zürich and Google has discovered a new…
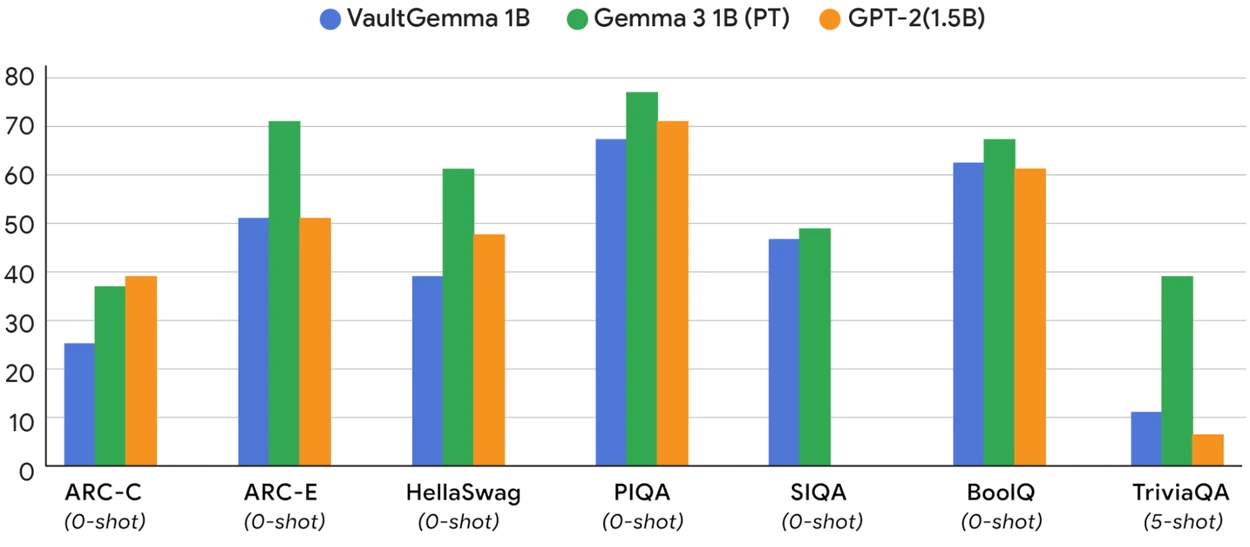
Google has released VaultGemma, a large language model designed to keep sensitive data private during training. The model uses differential…
Insider breach at FinWise Bank exposes data of 689,000 AFF customers Pierluigi Paganini September 16, 2025 An ex-employee caused an…
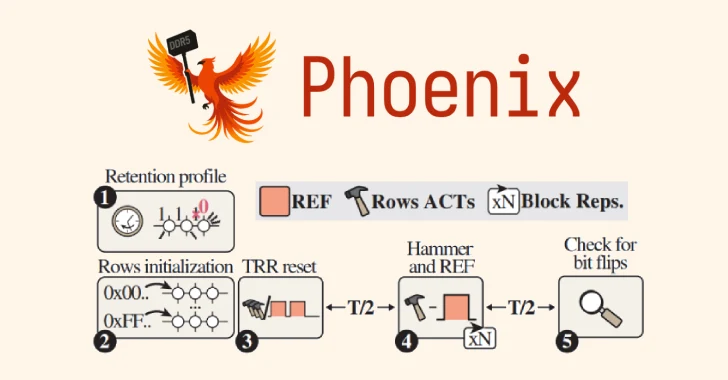
A new Rowhammer attack variant named Phoenix can bypass the latest protections in modern DDR5 memory chips, researchers have revealed….
In this Help Net Security interview, Nir Rothenberg, CISO at Rapyd, discusses global differences in payment security maturity and the…
Dean Swan, Vice President and General Manager of monday.com in APJ, says it’s a model that keeps organisations looking in…
Microsoft has addressed a widespread audio issue affecting Bluetooth speakers, headsets, and integrated laptop speakers in Windows 11 version 24H2….
AI-powered video surveillance brings up big questions about privacy. On one hand, it can make us feel safer, but on…
Sep 16, 2025Ravie LakshmananMalware / Cyber Attack Cybersecurity researchers have flagged a fresh software supply chain attack targeting the npm…
Clean Links is a handy app that shows you exactly where a link will take you before you click it….