A first-of-its-kind marketplace rolled out on Tuesday offering free and discounted privacy and security services to America’s 23 million current…
SAP’s Security Patch Day on September 9, 2025, introduced fixes for 21 newly discovered vulnerabilities across its product portfolio and…
A single cyber incident can halt production lines, dent customer confidence, and wipe millions off a company’s share price –…
A new technique to exploit a complex use-after-free (UAF) vulnerability in the Linux kernel successfully bypasses modern security mitigations to gain root…
Jaguar Land Rover’s UK factories will remain closed until at least Wednesday as the company continues to recover from a…
It’s budget season. Once again, security is being questioned, scrutinized, or deprioritized. If you’re a CISO or security leader, you’ve…
Elastic has disclosed a security incident stemming from a third-party breach at Salesloft Drift, which resulted in unauthorized access to…
The Akamai Hunt Team has uncovered a new strain of malware that targets exposed Docker APIs with expanded infection capabilities….
In this Help Net Security video, Matt Fangman, Field CTO at SailPoint, discusses whether an AI culture war is inevitable….
A sophisticated new cybercrime toolkit named SpamGPT is enabling hackers to launch massive and highly effective phishing campaigns by combining…
Cybersecurity researchers at FortiGuard Labs have uncovered a sophisticated phishing campaign that deploys the MostereRAT remote access trojan to compromise…
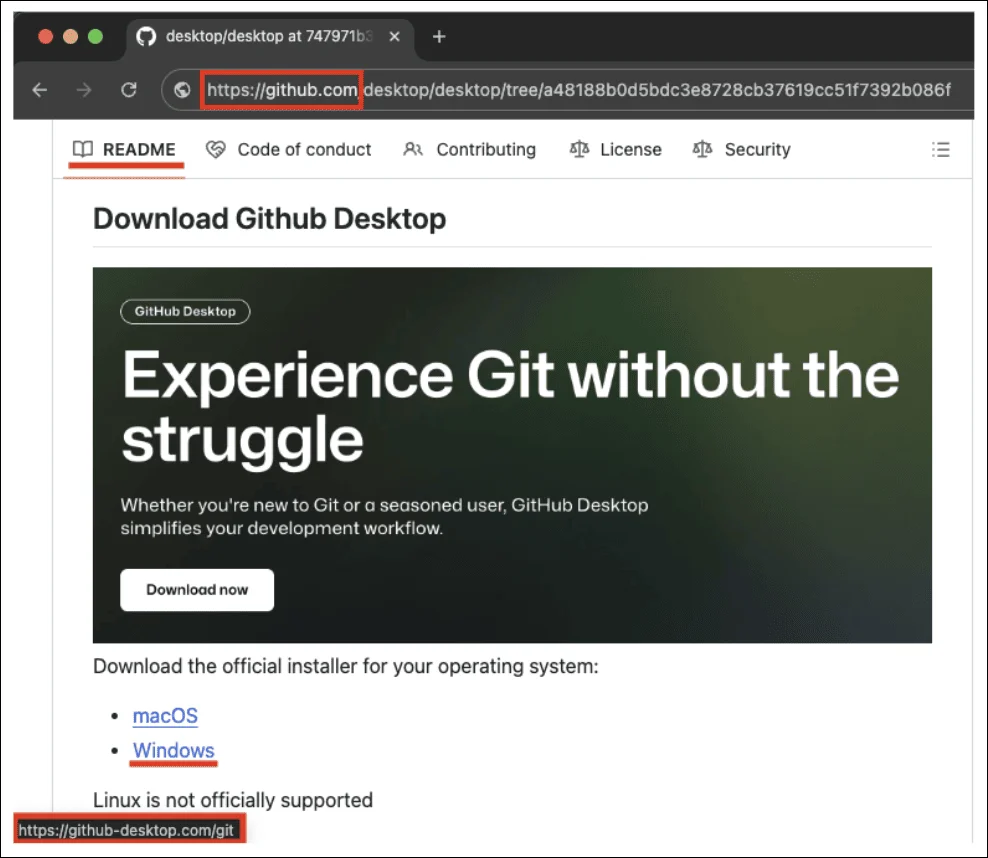
Researchers have spotted a malvertising (and clever malware delivery) campaign targeting IT workers in the European Union with fake GitHub…