A successful phishing attack against a developer has resulted in one of the largest supply chain compromises to date, adding…
Research from the Australian Institute of Criminology reveals that just two ransomware operations, Conti and LockBit, were responsible for nearly…
For Dean Swan, Vice President and General Manager of monday.com in APJ, the management framework is proving just as powerful…
Sep 09, 2025Ravie LakshmananCyber Espionage / Telecom Security Threat hunters have discovered a set of previously unreported domains, some going…
Media streaming platform Plex is warning customers to reset passwords after suffering a data breach in which a hacker was…
Federal authorities on Monday imposed sanctions on 19 people and organizations allegedly involved in major cyberscam hubs in Burma and…
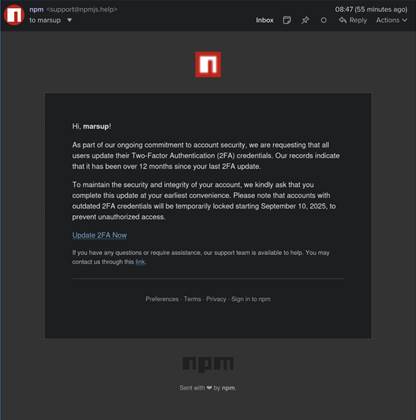
At least 18 popular JavaScript code packages that are collectively downloaded more than two billion times each week were briefly…
Google-owned security firm Mandiant has determined the root cause for the expanding breach of AI-powered marketing platform Salesloft, whose artificial…
Having spent the best part of a year and a half working to unify its products and tools with those…
When Apple debuts new iPhones this week, analysts say its biggest challenge will be to ride out another ho-hum launch…
Large network scans have been targeting Cisco ASA devices, prompting warnings from cybersecurity researchers that it could indicate an upcoming flaw in…
mecwacare, a not-for-profit Melbourne aged care services provider, is consolidating 17 core systems into one and redesigning over 200 processes…