The cybersecurity landscape for macOS users has taken a dangerous turn as cybercriminals increasingly target Apple’s ecosystem with sophisticated malware…
After a security breach, forensic investigators work quickly to follow the attacker’s trail. Security experts have analyzed this situation and…
Groundbreaking research reveals the inner workings of cybercriminal networks targeting Australia and allied nations. Australian researchers have completed a comprehensive…
Puppet’s 2024 State of DevOps report was subtitled “the evolution of platform engineering”. Platform engineering, it said, can be a…
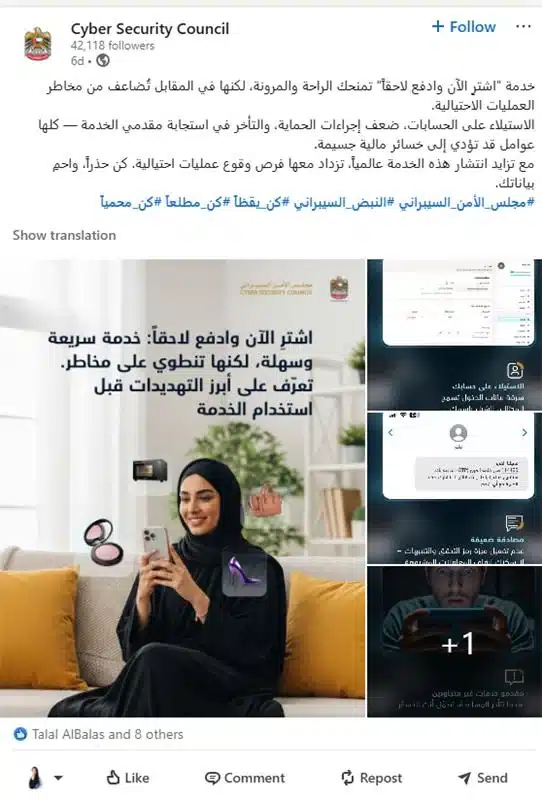
The UAE Cyber Security Council (CSC) has issued a stark warning that 70 per cent of smart home devices are…
U.S. federal authorities have launched an investigation into a sophisticated malware campaign that targeted sensitive trade negotiations between Washington and…
Tenable, a well-known cybersecurity company, has confirmed that it was affected by a recent large-scale data theft campaign. The attack…
InterceptSuite is an open-source, cross-platform network traffic interception tool designed for TLS/SSL inspection, analysis, and manipulation at the network level….
September 5, 2025 – A hacker cracked into a database of video recordings taken from Nexar-branded cameras, which are built…
Ransomware has emerged as one of the most devastating cybercrime threats in the contemporary digital landscape, with criminal organizations operating…
Cybercriminals have escalated their attacks against macOS users by deploying a sophisticated new campaign that leverages a fraudulent Microsoft Teams…
The Linux Kernel Runtime Guard (LKRG) is a kernel module that checks the Linux kernel while it’s running. It looks…