A newly published independent research report highlights Flowable’s rise in the digital process automation market. Built on open-source APIs and…
I know many of us love(d) Windows XP and Windows 7 almost as much as we dislike Windows 10 and…
Microsoft has teamed up with Barclays on a novel approach to tackling artificial intelligence (AI) and optimisation problems based on…
Google has released the September 2025 security update for Android devices, addressing a total of 84 vulnerabilities, including two actively…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert about a serious security hole in certain TP-Link…
Sep 03, 2025Ravie LakshmananMobile Security / Vulnerability Google has shipped security updates to address 120 security flaws in its Android…
Cybersecurity researchers began detecting an alarming surge in early April 2025 in UDP flood traffic emanating from compromised network video…
In today’s rapidly evolving digital landscape, the challenges surrounding cybersecurity are growing exponentially. Industrial sectors, including energy, manufacturing, and utilities,…
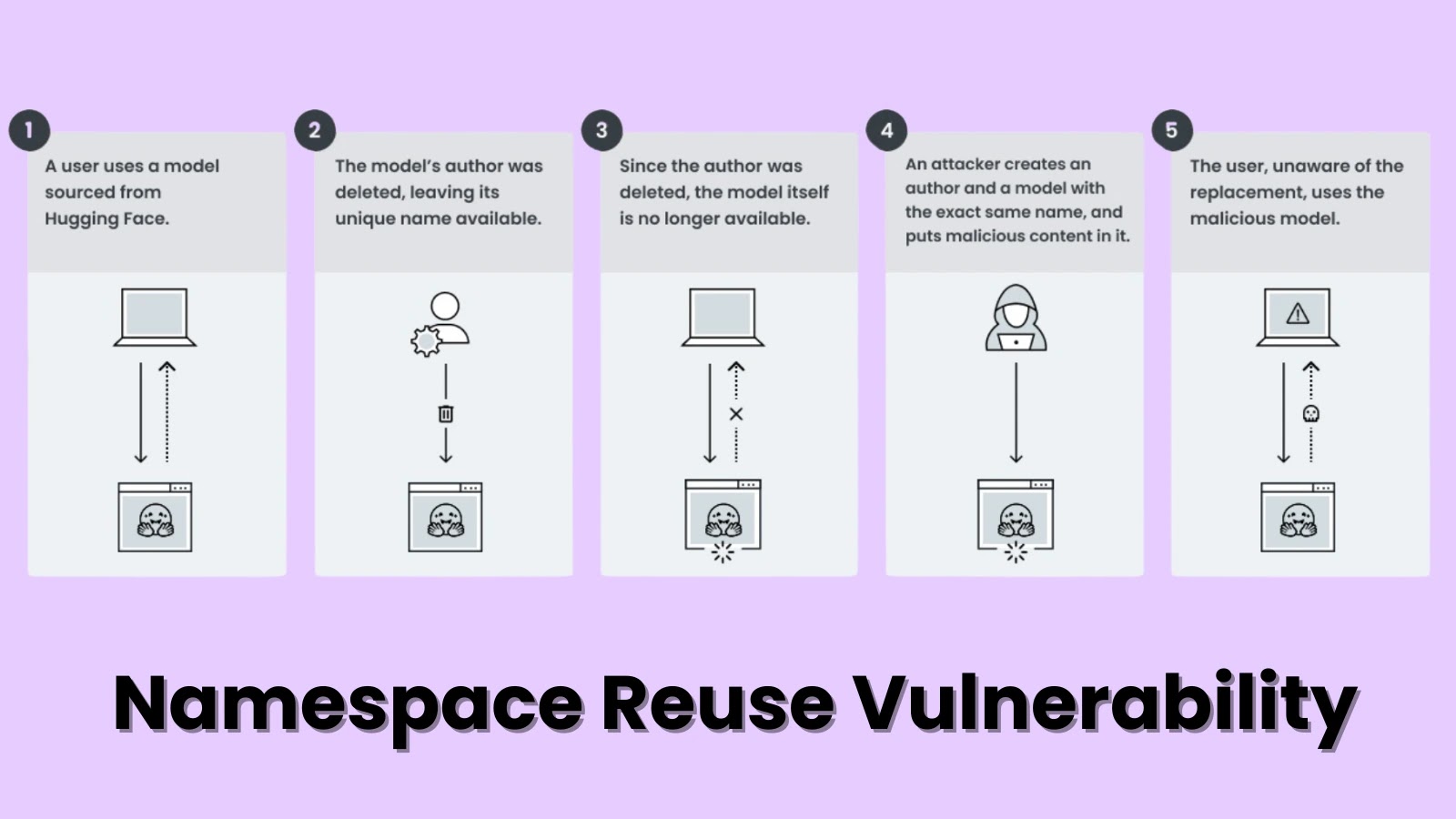
A newly discovered vulnerability in the AI supply chain—termed Model Namespace Reuse—permits attackers to achieve Remote Code Execution (RCE) across…
Cloudflare has also been affected by the Salesloft Drift breach, the US web infrastructure and security company confirmed on Tuesday,…
In January 2025, cybersecurity experts at Wiz Research found that Chinese AI specialist DeepSeek had suffered a data leak, putting…
PagerDuty, a leader in digital operations management, has confirmed a security incident that resulted in unauthorized access to some of…