PagerDuty has confirmed that it experienced a data breach following a compromise of its Salesforce account. The company was first…
K–12 education in the U.S. still largely overlooks cybersecurity. As a result, children remain vulnerable to risks such as identity…
Sep 03, 2025Ravie LakshmananArtificial Intelligence / Vulnerability Threat actors are attempting to leverage a newly released artificial intelligence (AI) offensive…
U.S. CISA adds WhatsApp, and TP-link flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini September 03, 2025 U.S. Cybersecurity…
The recently emerged DireWolf ransomware group has launched a sophisticated new campaign targeting Windows systems worldwide, employing ruthless tactics to…
A co-worker forwarded this rather convincing PayPal scam to me. Thanks Elena. A highly sophisticated email scam is targeting PayPal…
Donald Trump’s second term in office as the president of the United States has witnessed fundamental changes to how the…
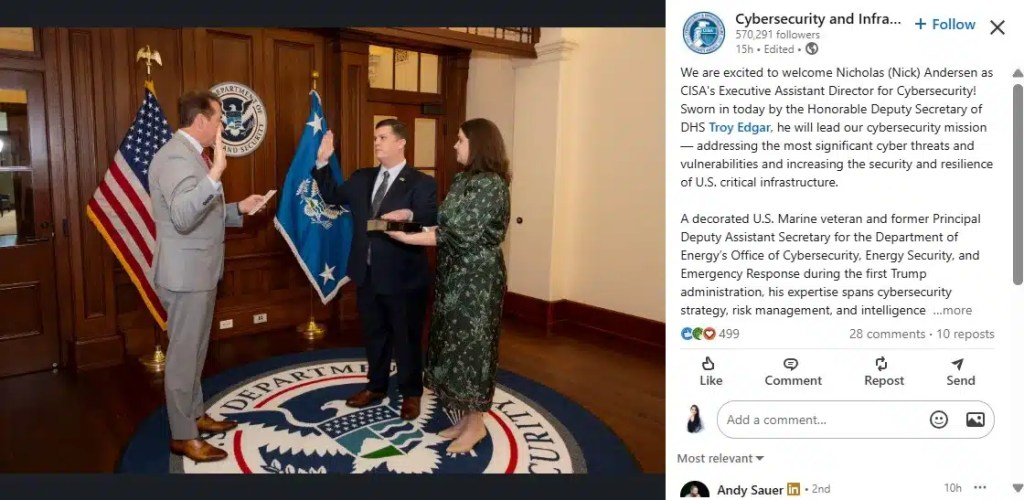
The Cybersecurity and Infrastructure Security Agency (CISA) has announced the appointment of Nicholas Andersen as its new Executive Assistant Director…
OpenAI announced today its definitive agreement to acquire Statsig, a product experimentation and analytics platform, for $1.1 billion. The acquisition…
The U.S. District Court for the District of Columbia today imposed landmark remedies in the Justice Department’s monopolization case against…
With a password, there’s a ton of room for an attacker to potentially steal your password. Data breaches might expose…
The BC-SECURITY team has released a major update to its flagship offensive security framework, Empire, introducing enhanced agent capabilities and comprehensive…