Google has disputed a widely reported story about the company warning all Gmail users to reset their passwords due to…
A newly discovered WhatsApp scam has begun circulating on messaging platforms, exploiting the popular device linking feature to seize full…
Google has firmly rejected widespread reports suggesting it issued a global security alert to its 2.5 billion Gmail users, calling…
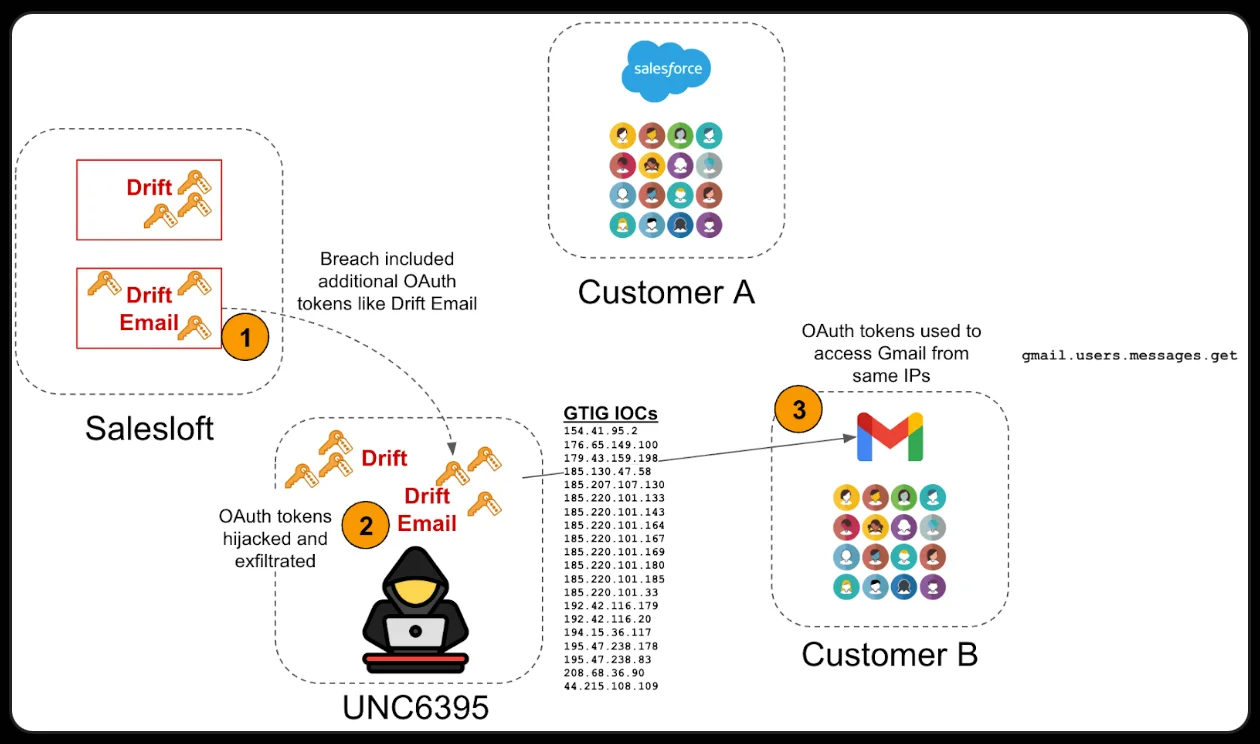
Hackers exploited the Salesloft Drift app to steal OAuth tokens and access Salesforce data, exposing customer details at major tech…
In the wake of last week’s revelation of a breach at Salesloft by a group tracked by Google as UNC6395,…
Restaurants with three Michelin stars represent the pinnacle of fine dining. In the UK, The Fat Duck by Heston Blumenthal,…
At Intigriti, we hold monthly web-based Capture The Flag (CTF) challenges as a way to engage with the security research…
Varonis has acquired SlashNext, an AI-driven email security company, for up to $150 million in a move that reflects the…
Jaguar Land Rover (JLR) announced that a cyberattack forced the company to shut down certain systems as part of the mitigation…
Luxury automaker Jaguar Land Rover (JLR) has been forced to halt production at its Halewood plant and shut down its…
A critical authentication bypass flaw in ESPHome’s ESP-IDF web server component allows unauthorized users on the same local network to…
The Black Hat USA 2025 CISO Podcast Series by The Cyber Express, in collaboration with Suraksha Catalyst, has released its highly…