You may have seen them in restaurants, cat-faced robots gliding between tables, delivering plates of food. These robots, many of…
Penlink’s CEO, Peter Weber, shares how leaders can reduce their odds of becoming yet another statistic through a debilitating cyber-attack by…
Apple appears poised to remove the physical SIM card slot from its upcoming iPhone 17 models in more countries, with…
A newly disclosed security vulnerability, tracked as CVE-2025-0165, has been reported, specifically concerning the users of the IBM Watsonx Orchestrate…
Crooks exploit Meta malvertising to target Android users with Brokewell Pierluigi Paganini September 01, 2025 Cybercriminals spread Brokewell via fake…
Cybercriminals are increasingly exploiting legitimate email marketing platforms to launch sophisticated phishing campaigns, leveraging the trusted reputation of these services…
A high-severity vulnerability in SUSE’s Fleet, a GitOps management tool for Kubernetes clusters, has been disclosed by security researcher samjustus…
As enterprises continue to shift their operations to the browser, security teams face a growing set of cyber challenges. In…
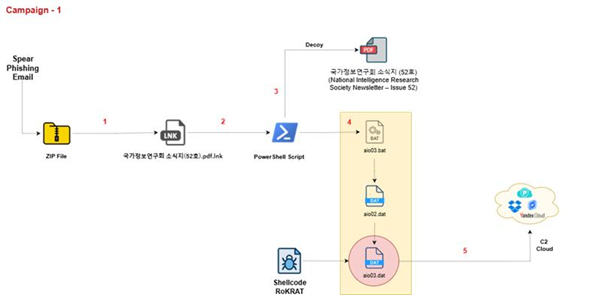
North Korea’s APT37 deploys RokRAT in new phishing campaign against academics Pierluigi Paganini September 01, 2025 ScarCruft (APT37) launches Operation…
A sophisticated Android malware campaign has emerged in recent months, targeting students in Bangladesh by masquerading as legitimate scholarship applications….
In recent months, Trustwave SpiderLabs—a LevelBlue company renowned for its threat intelligence and incident response services—has observed a marked uptick…
Amazon has disrupted a Russian APT29 watering hole campaign that used compromised sites to target Microsoft authentication with malicious redirects….