Microsoft has begun rolling out the Windows 11, version 25H2 (Build 26200.5074) preview to the Release Preview Channel, offering enthusiasts…
Platform engineering is based on the principles of product management and the product model applied to digital and IT systems….
Fraudster stole over $1.5 million from city of Baltimore Pierluigi Paganini September 01, 2025 Scammer stole $1.5M from Baltimore by…
A sophisticated malware campaign targeting niche Large Language Model (LLM) role-playing communities has emerged, leveraging advanced social engineering tactics to…
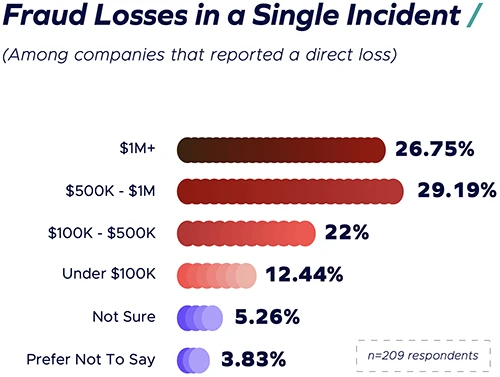
More than 80 percent of large U.S. companies were targeted by socially engineered fraud in the past year, according to…
August 28, 2025 – The FCC has disconnected over a thousand voice operators from the public telephone network for not…
Cohesity has appointed James Eagleton as Managing Director for Australia and New Zealand (ANZ). In this role, Eagleton will be…
Cybercriminals are now weaponizing Windows Defender Application Control (WDAC) policies to disable Endpoint Detection and Response (EDR) agents en masse….
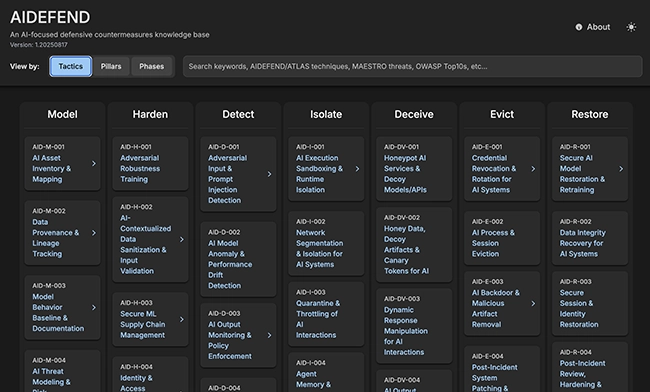
AIDEFEND (Artificial Intelligence Defense Framework) is an open knowledge base dedicated to AI security, providing defensive countermeasures and best practices…
A critical security vulnerability has been discovered in the Linux UDisks daemon that could allow unprivileged attackers to gain access…
The cybersecurity landscape has witnessed a dangerous evolution as Advanced Persistent Threat (APT) groups increasingly weaponize opportunistic infostealer malware for…
A team of researchers from Frondeur Labs, DistributedApps.ai, and OWASP has developed a new machine learning framework designed to help…