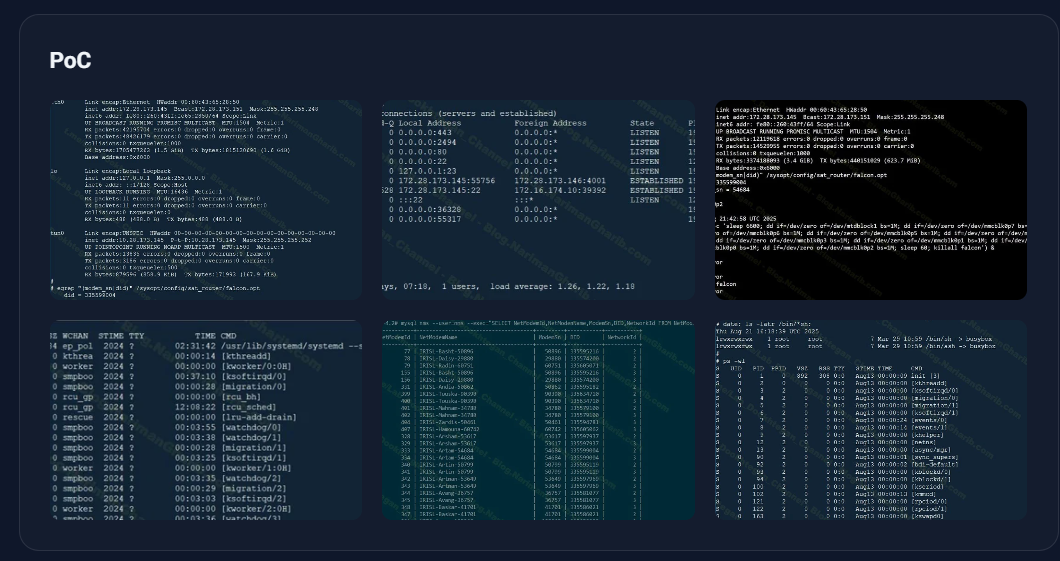
A critical zero-day vulnerability in Citrix NetScaler products, identified as CVE-2025-6543, has been actively exploited by threat actors since at…
QNAP Systems has released security patches to address multiple vulnerabilities affecting QVR firmware in legacy VioStor Network Video Recorder (NVR)…
Lab Dookhtegan hacking group disrupts communications on dozens of Iranian ships Pierluigi Paganini August 30, 2025 Lab Dookhtegan hacking group…
A new malware campaign, dubbed “Sindoor Dropper,” is targeting Linux systems using sophisticated spear-phishing techniques and a multi-stage infection chain….
As students returned to school this week, WIRED spoke to a self-proclaimed leader of a violent online group known as…
Security researcher Kevin Beaumont has revealed alarming details about CVE-2025-6543, a critical Citrix NetScaler vulnerability that was actively exploited as…
Amazon’s cybersecurity team has successfully disrupted a sophisticated watering hole campaign orchestrated by APT29, a notorious hacking group linked to…
Google has issued a broad security alert to its 2.5 billion Gmail users, advising them to enhance their account security…
Aug 30, 2025Ravie LakshmananZero-Day / Vulnerability WhatsApp has addressed a security vulnerability in its messaging apps for Apple iOS and…
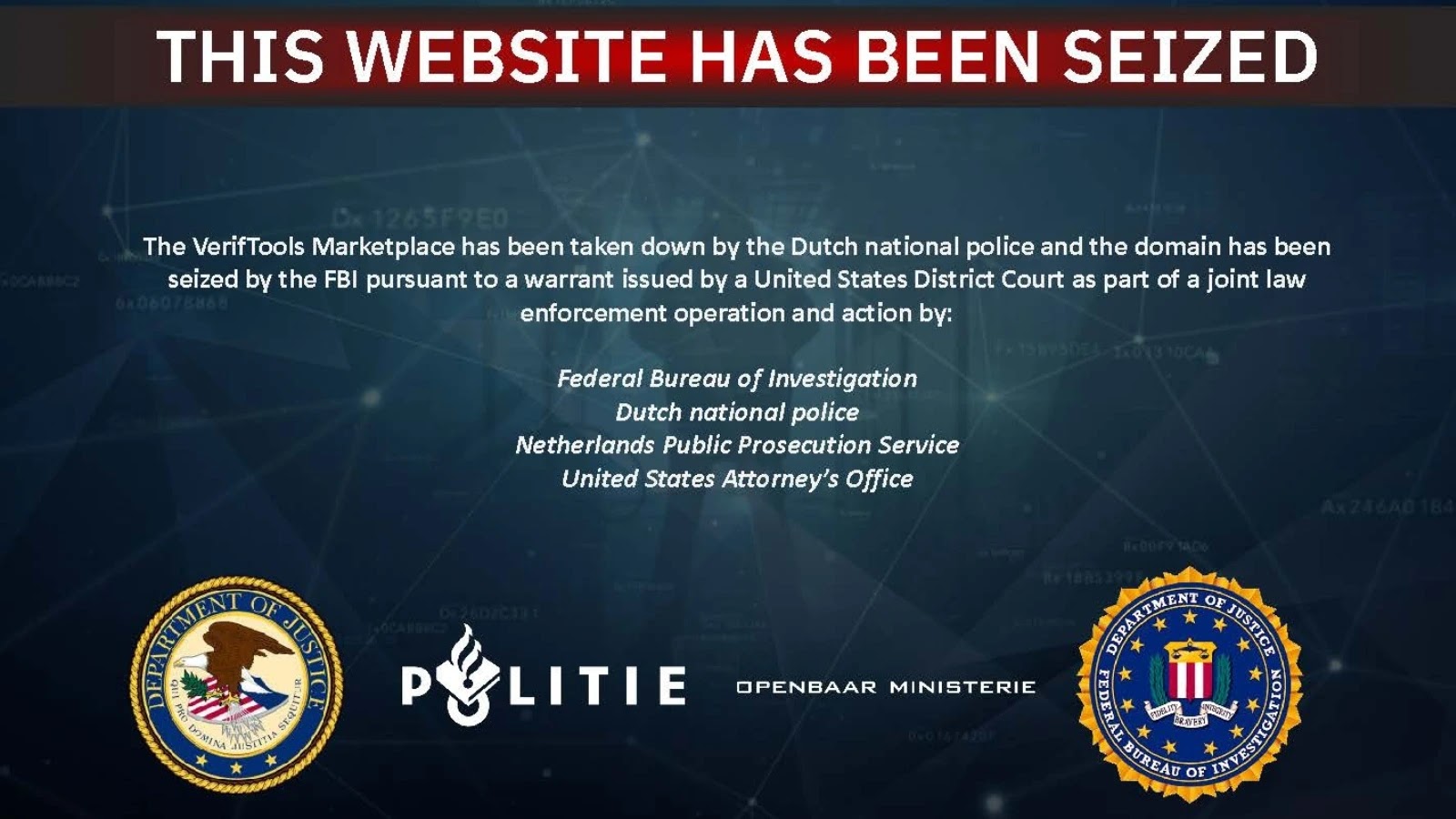
The U.S. Attorney’s Office for the District of New Mexico announced Thursday that federal authorities have executed a court-authorized seizure…
Online medical consultations expanded during the pandemic, especially for the elderly. Like with online classes and working from home, they…
On Friday, the Social Security Administration’s chief data officer, Chuck Borges, sent an email to agency staff claiming that he…