Aug 29, 2025Ravie LakshmananZero-Day / Vulnerability The Sangoma FreePBX Security Team has issued an advisory warning about an actively exploited…
I think I’ve finally figured out what’s up with podcast audio. At least in terms of: So what I’m going…
Security researchers have uncovered significant vulnerabilities in code generated by Large Language Models (LLMs), demonstrating how “vibe coding” with AI…
In a significant data breach disclosed by TransUnion LLC, more than 4.4 million consumers had sensitive personal information compromised in…
Aug 29, 2025Ravie LakshmananVulnerability / Enterprise Security Click Studios, the developer of enterprise-focused password management solution Passwordstate, said it has…
Even after 25 years, Microsoft Active Directory (AD) remains the backbone of identity and access management in up to 90%…
Continue reading online to avoid the email cutoff issue > SECURITY | AI | MEANING :: Unsupervised Learning is my…
A high-severity Server-Side Request Forgery (SSRF) vulnerability has been identified in the widely used PhpSpreadsheet library, potentially allowing attackers to…
In a concerning development for enterprise security, cybercriminals have begun exploiting Microsoft Teams—long trusted as an internal messaging and collaboration…
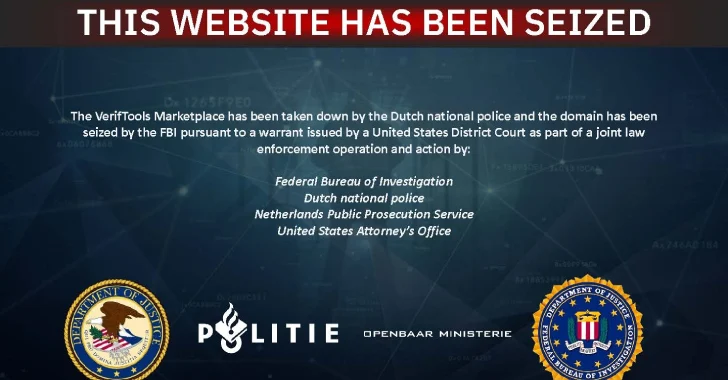
Aug 29, 2025Ravie LakshmananCryptocurrency / Cybercrime Authorities from the Netherlands and the United States have announced the dismantling of an…
Google: Salesloft Drift breach hits all integrations Pierluigi Paganini August 29, 2025 Google warns that Salesloft Drift OAuth breach affects…
I’m working on my context.md file for my personal Digital Assistant, and one part of that will be my model.md…