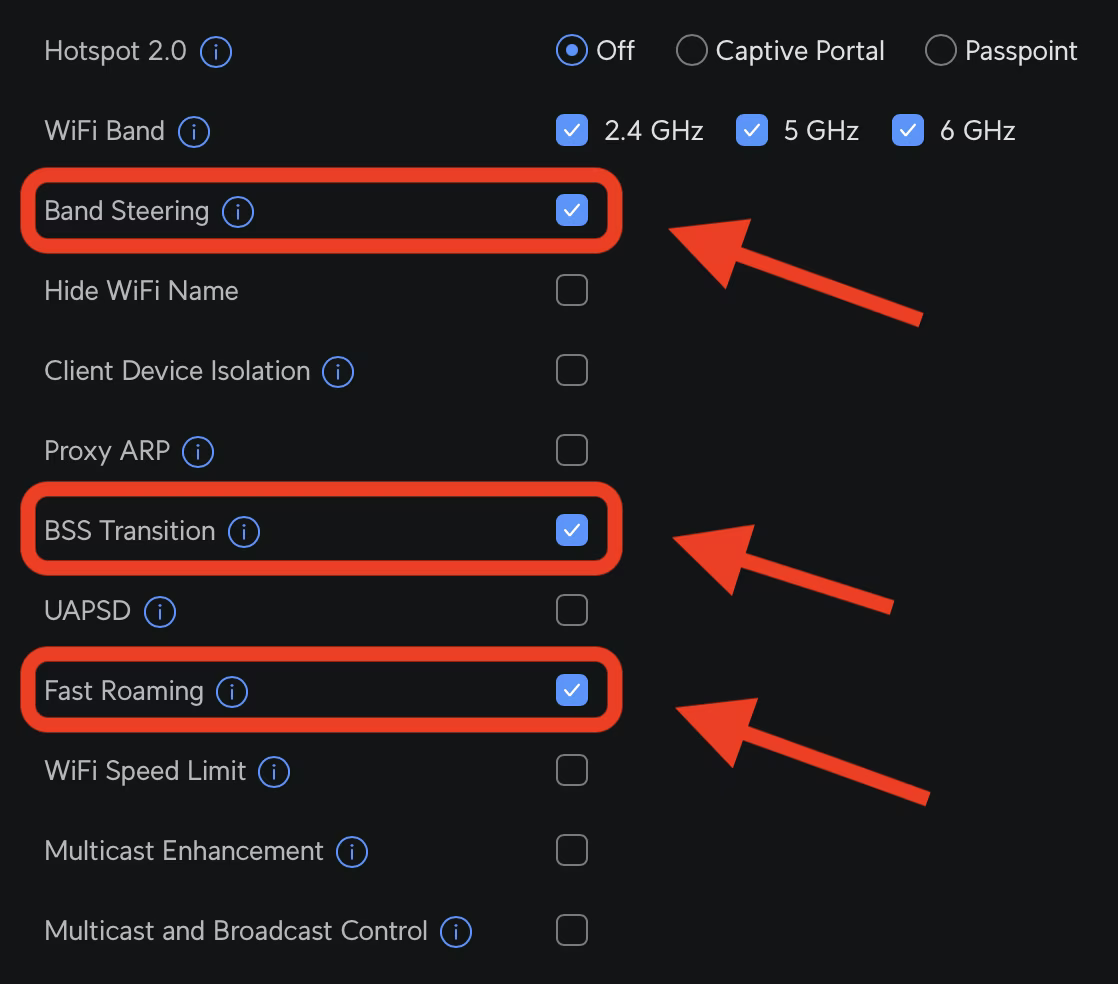
The three settings I had to enable to get proper WiFi roaming The problem I’m a massive fan of Ubiquiti…
Nx malware uses AI CLIs to find secrets, ESET discovers malware sample leveraging OpenAI’s OSS model, binary exploitation CTF for…
Election officials should brace for direct attacks from the Trump administration and its state GOP allies on the integrity of…
Shadow IT – the systems your security team doesn’t know about – is a persistent challenge. Policies may ban them,…
Anthropic has thwarted multiple sophisticated attempts by cybercriminals to misuse its Claude AI platform, according to a newly released Threat…
The China-linked advanced persistent threat (APT) actor known as Salt Typhoon has continued its attacks targeting networks across the world,…
The European Union Agency for Cybersecurity (ENISA) and the European Commission have signed a landmark contribution agreement to establish and…
I have some interesting thoughts going into the big day tomorrow, and I wanted to try to capture them concisely….
Consumer credit reporting giant TransUnion warns it suffered a data breach exposing the personal information of over 4.4 million people…
ShadowSilk first surfaced in late 2023 as a sophisticated threat cluster targeting government entities across Central Asia and the broader…
The notorious Lazarus advanced persistent threat (APT) organization, which Qi’anxin internally tracks as APT-Q-1, has been seen using the ClickFix…
A coalition of international cybersecurity agencies led by the UK’s National Cyber Security Centre (NCSC) has publicly linked three China-based…
![[tl;dr sec] #294 – Nx Backdoored, AI-powered Ransomware, PhrackCTF [tl;dr sec] #294 - Nx Backdoored, AI-powered Ransomware, PhrackCTF](https://image.cybernoz.com/wp-content/uploads/2025/08/tldr-sec-294-Nx-Backdoored-AI-powered-Ransomware-PhrackCTF.png)








