Apple has issued emergency security updates across its entire ecosystem to address CVE-2025-43300, a critical zero-day vulnerability in the ImageIO framework that…
The federal government is set to pilot the use of artificial intelligence to help review applications for its Digital Marketplace…
You don’t have to believe that companies want to fire all their employees to see AI’s threat to jobs. That’s…
A notorious Chinese hacking campaign against telecommunications companies has now reached into a variety of additional sectors across the globe,…
NVIDIA has issued a critical security bulletin addressing a high-severity vulnerability in its NeMo Curator platform that could allow attackers…
Path traversal flaws like Zip Slip, which give hackers the ability to alter file systems while decompressing, remain a serious…
Cybersecurity firm Netcraft has discovered a new task scam cluster that has stolen over $1 million in crypto. The scammers…
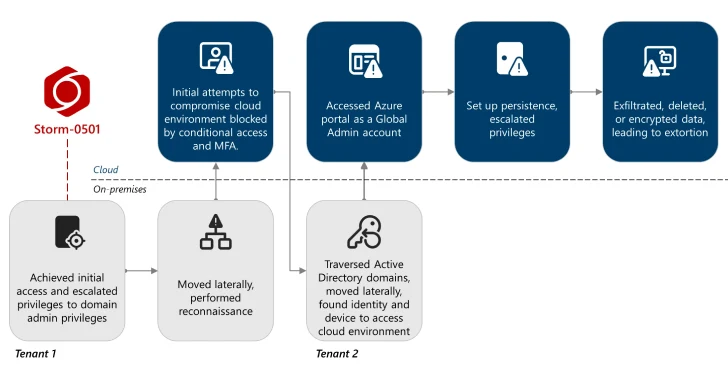
The financially motivated threat actor known as Storm-0501 has been observed refining its tactics to conduct data exfiltration and extortion…
Over 28,000 Citrix instances remain exposed to critical RCE flaw CVE-2025-7775 Pierluigi Paganini August 27, 2025 Over 28,200 Citrix NetScaler…
I’m sure you’ve heard the argument that LLMs aren’t really thinking because, according to them, LLMs are just predicting the…
The Sangoma FreePBX Security Team is warning about an actively exploited FreePBX zero-day vulnerability that impacts systems with the Administrator…
August 2025 has marked a significant evolution in cybercrime tactics, with threat actors deploying increasingly sophisticated phishing frameworks and social…