Welcome back to this series, introducing the IEC 62443 standard. The first article was a general introduction to IEC 62443,…
As an Apple Fanboy going back to 2007, this is the first year I’ve felt fear for Apple’s future. And…
Google is introducing a new defense for Android called ‘Developer Verification’ to block malware installations from sideloaded apps sourced from outside the official…
A critical zero-day remote code execution (RCE) vulnerability, tracked as CVE-2025-7775, is affecting over 28,000 Citrix instances worldwide. The flaw…
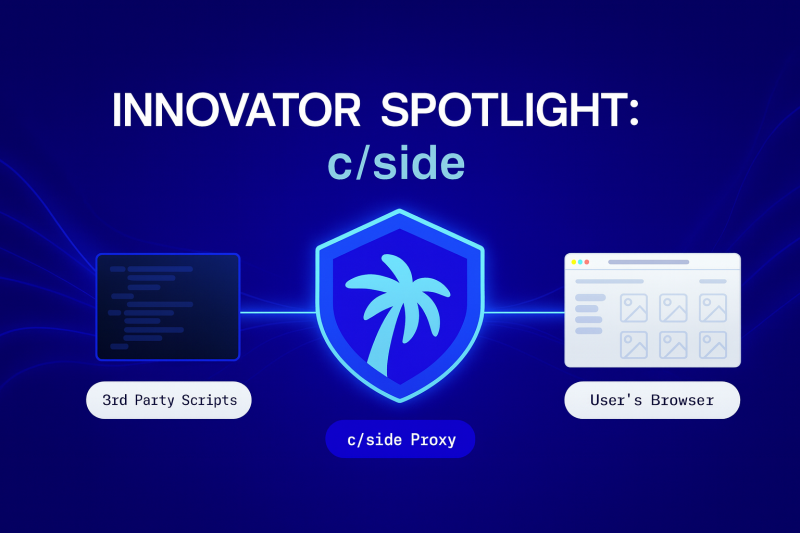
Securing the Browser’s Blind Spot By Victoria Hargrove, CDM Reporter What CSide Does Most security stacks fortify servers, databases, and…
U.S. CISA adds Citrix NetScaler flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini August 27, 2025 U.S. Cybersecurity and Infrastructure…
Don’t get me wrong—Cursor is genuinely awesome. It’s probably the best AI-native code editor ever built, with incredibly thoughtful integrations…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. Chinese government-backed…
Google says it is starting a cyber “disruption unit,” a development that arrives in a potentially shifting U.S. landscape toward…
A cyberattack on Miljödata, an IT systems supplier for roughly 80% of Sweden’s municipal systems, has caused accessibility problems in…
A weaponized proof-of-concept exploit has been publicly released targeting CVE-2025-54309, a severe authentication bypass vulnerability affecting CrushFTP file transfer servers. …
Cross-domain solutions (CDS) consist of the secure exchange of information between security domains. This type of solution, which emerged as…