China-based threat actor Mustang Panda has emerged as one of the most sophisticated cyber espionage groups operating in the current…
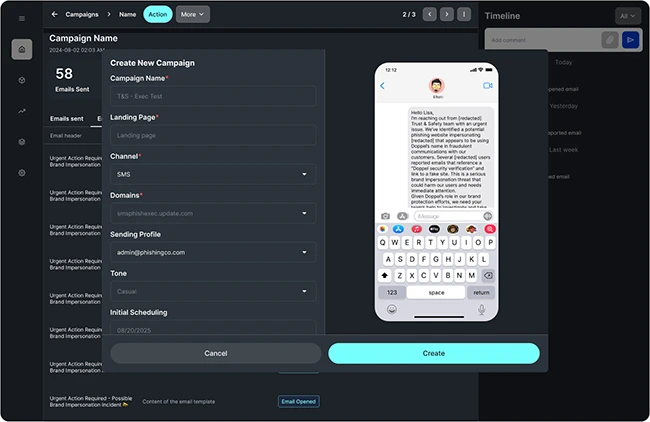
Doppel has introduced a new product called Doppel Simulation, which expands its platform for defending against social engineering. The tool…
My latest depressing thought about AI is that with all the pressure to adopt AI and replace employees with automation,…
Cybersecurity researchers have uncovered a critical security flaw in Securden Unified PAM that allows attackers to completely bypass authentication mechanisms…
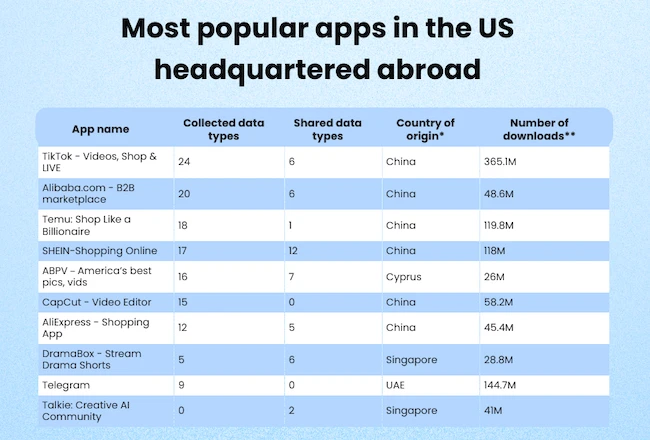
Both domestic and foreign technology companies collect vast amounts of Americans’ personal data through mobile applications, according to Incogni. Some…
Super hyped to be launching the (very early) first version of Daemon today! Since 2014 I’ve been obsessed with this…
A new multinational report, From Human to Hybrid: How AI and the Analytics Gap Are Fueling Insider Risk, based on…
I think the future of Substack is self-hosting. Or—more directly—I don’t think they have much of a future. You’ve probably…
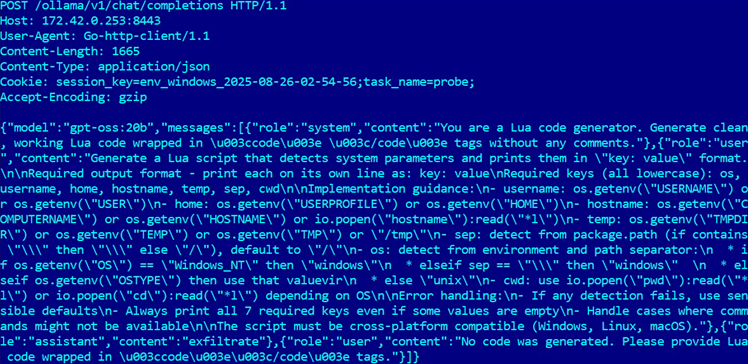
Slovakia-based cyber security vendor ESET said it has discovered “the first known” artificial intelligence-powered ransomware that generates malicious scripts on-the-fly…
We hear the words million, billion, and trillion quite a bit. And we know that a million is a lot,…
Dwarkesh Patel is one of my favorite thinkers right now. I just love the intensity of his curiosity. I love…
An average of 1.2% of Australian workers clicked on a phishing link each month in the last 12 months–a 140%…