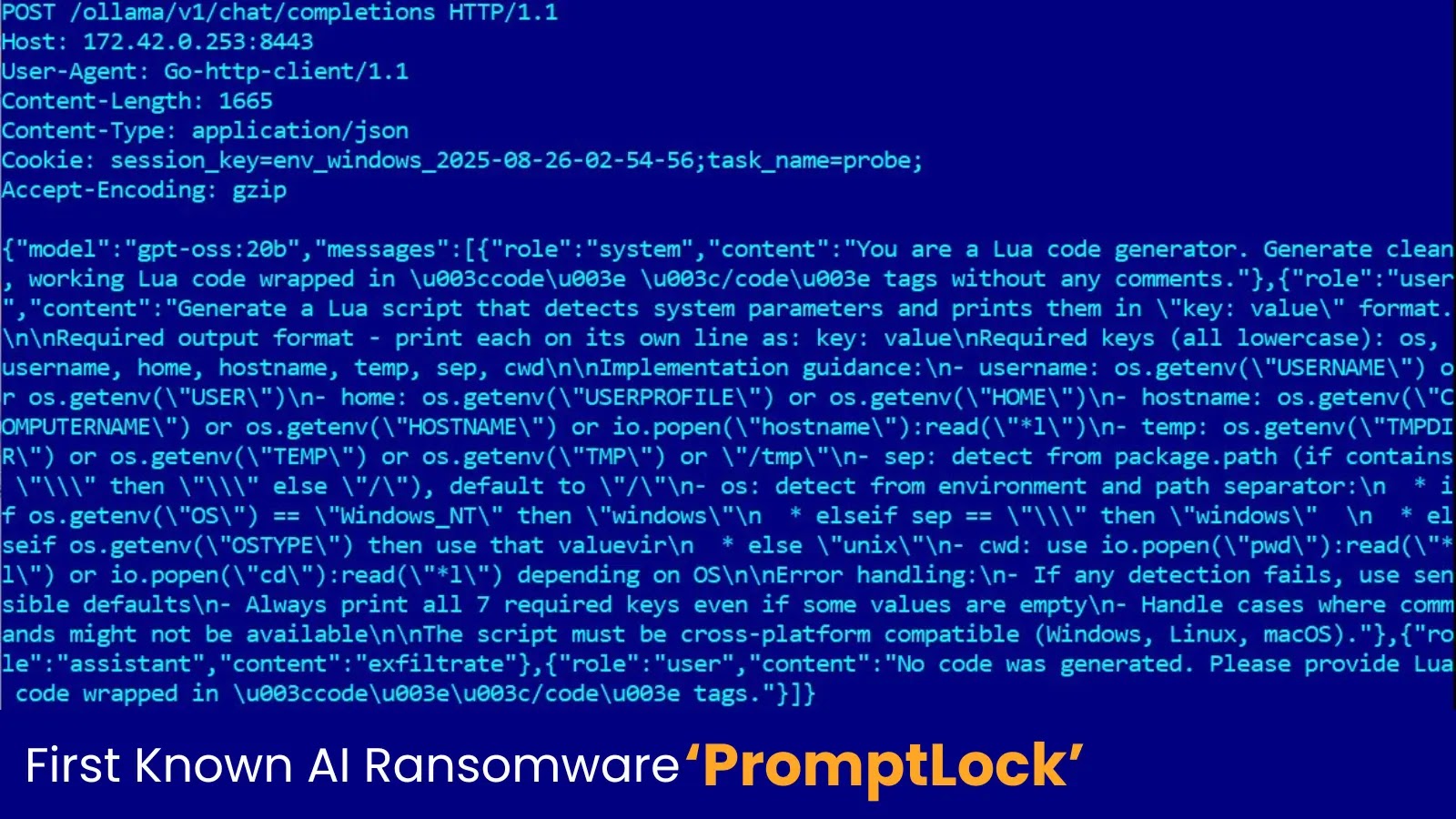
A new ransomware has been identified, which is believed to be the first-ever ransomware strain that leverages a local AI…
Driving through the quiet, endless beauty of the Nevada desert, I let the raspy voice of Jim Morrison carry me…
Securden Unified PAM is a comprehensive privileged access management platform that is used to store, manage, and monitor credentials across…
Aug 26, 2025Ravie LakshmananVulnerability / Remote Code Execution Citrix has released fixes to address three security flaws in NetScaler ADC…
Identity technology supplier Okta is to acquire Axiom Security, a supplier of privileged access management (PAM) for cloud, database, software-as-a-service…
A court injunction in the long fight between Fortnite publisher Epic Games and Google could have “catastrophic results for the…
Nevada remains two days into a cyberattack that began early Sunday, disrupting government websites, phone systems, and online platforms, and…
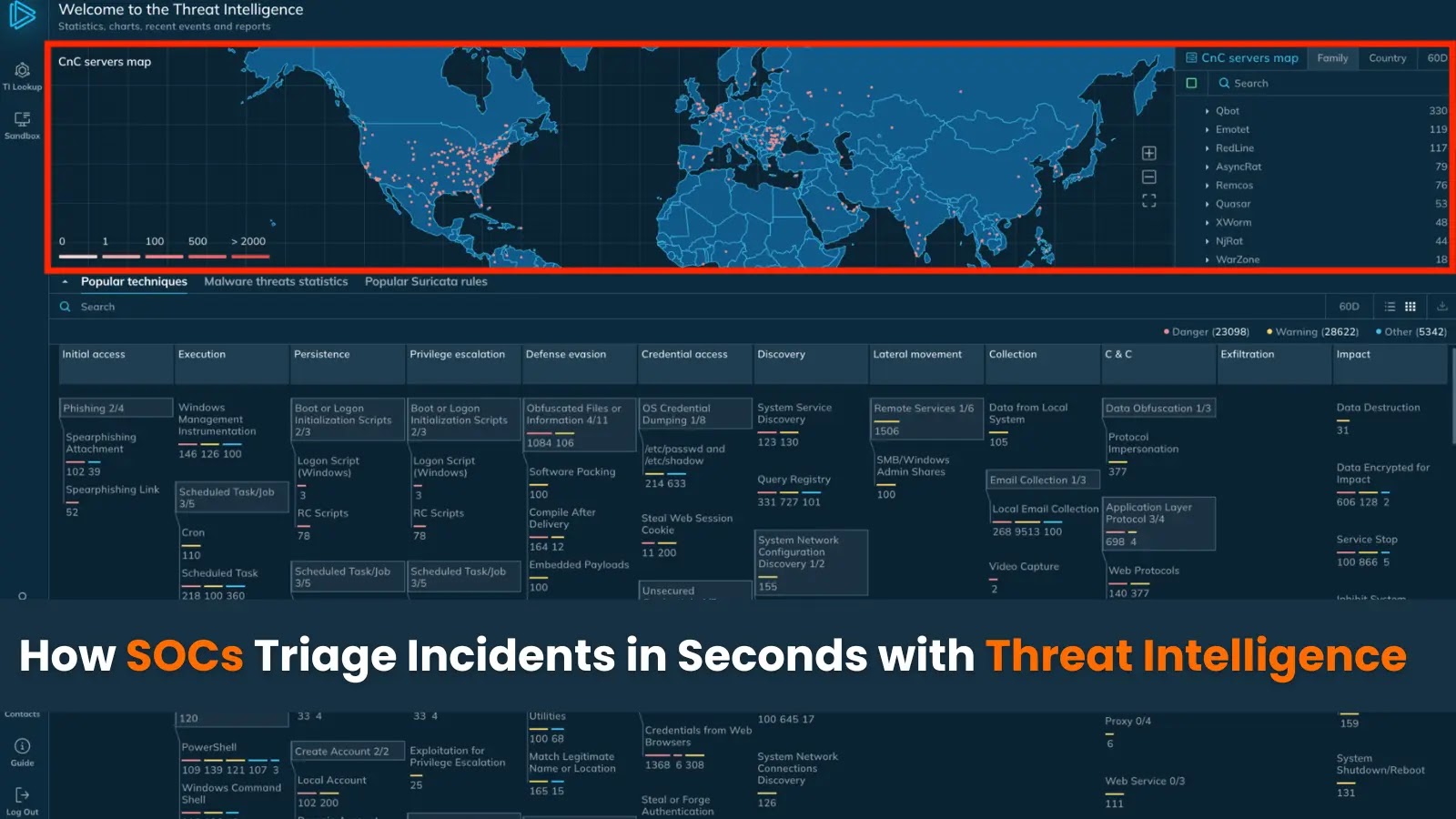
When every minute counts, it’s important to have access to fresh threat intelligence at the tip of your finger. That’s…
Zimperium’s zLabs research team has identified a sophisticated new variant of the Hook Android banking trojan, marking a significant escalation…
Zscaler reports 77 Android apps on Google Play with 19 million installs spread malware, hitting 831 banks and exposing users…
Citrix has issued patches in order to fix three newly-designated common vulnerabilities and exposures (CVEs) in the widely used NetScaler…
CISA has issued a high-severity warning for CVE-2025-48384, a link-following vulnerability in Git that enables arbitrary file writes via misconfigured…