The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding a critical vulnerability in Git (CVE-2025-48384) that…
By Eirik Salmi, System Analyst at Passwork Even though 88% of businesses spend over €1 million on GDPR compliance and…
Cloud Software Group has disclosed multiple high-severity vulnerabilities in NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway)…
There’s a lot of noise around compliance. New regulations seem to pop up every year, each promising to fix the…
Google has announced that all Android apps installed on approved devices will soon need to be able to be traced…
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is warning of hackers exploiting an arbitrary code execution flaw in the…
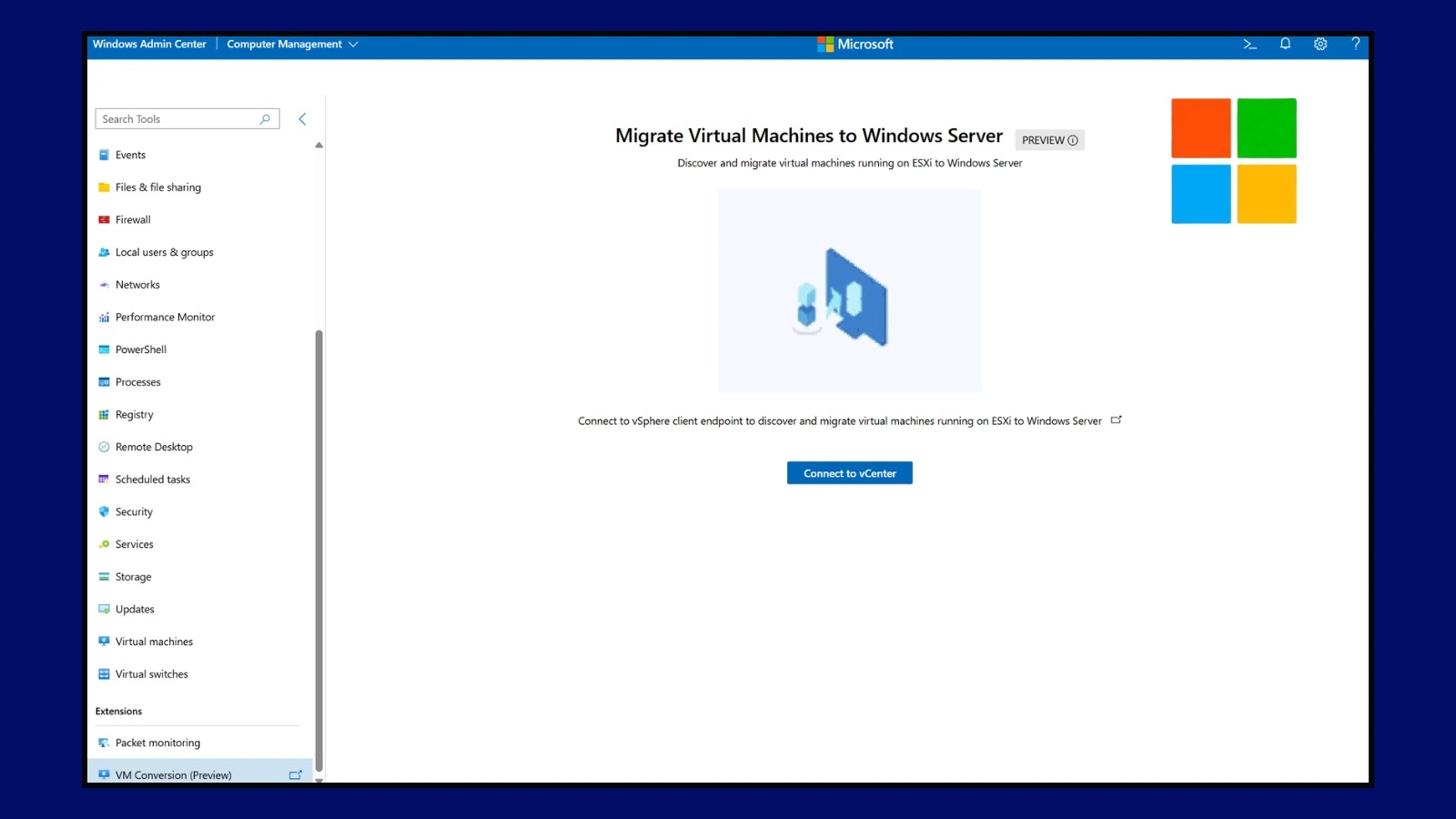
Microsoft has released a new VM Conversion extension for Windows Admin Center, designed to streamline the migration of VMware virtual…
CYFIRMA researchers have uncovered a campaign they have codenamed “OneFlip”, an operation that demonstrates how a single-bit modification inside a…
Chief information security officers are increasingly concerned about the risk of a cyberattack, and a growing number say they have…
Online PDF editors have become common tools for quick document manipulation, providing convenient alternatives to desktop software. However, their cloud-based…
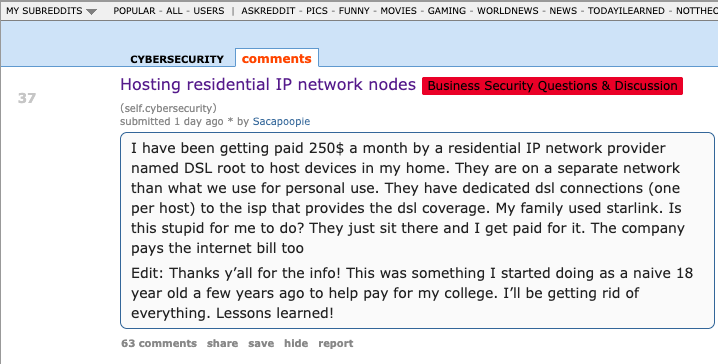
The cybersecurity community on Reddit responded in disbelief this month when a self-described Air National Guard member with top secret…
A proof-of-concept exploit for a high-severity Google Chrome zero-day vulnerability has been published publicly, less than three months after the…