In August 2025, researchers at George Mason University published a groundbreaking study at the 34th USENIX Security Symposium, introducing OneFlip,…
Threat actors are increasingly refining Android droppers to circumvent enhanced security measures, extending their utility beyond sophisticated banking trojans to…
Menlo Park, United States, August 26th, 2025, CyberNewsWire AccuKnox, a leader in Zero Trust Kubernetes and cloud-native security solutions, has…
The cybersecurity landscape has been significantly impacted by the discovery and active exploitation of two critical zero-day vulnerabilities in WinRAR,…
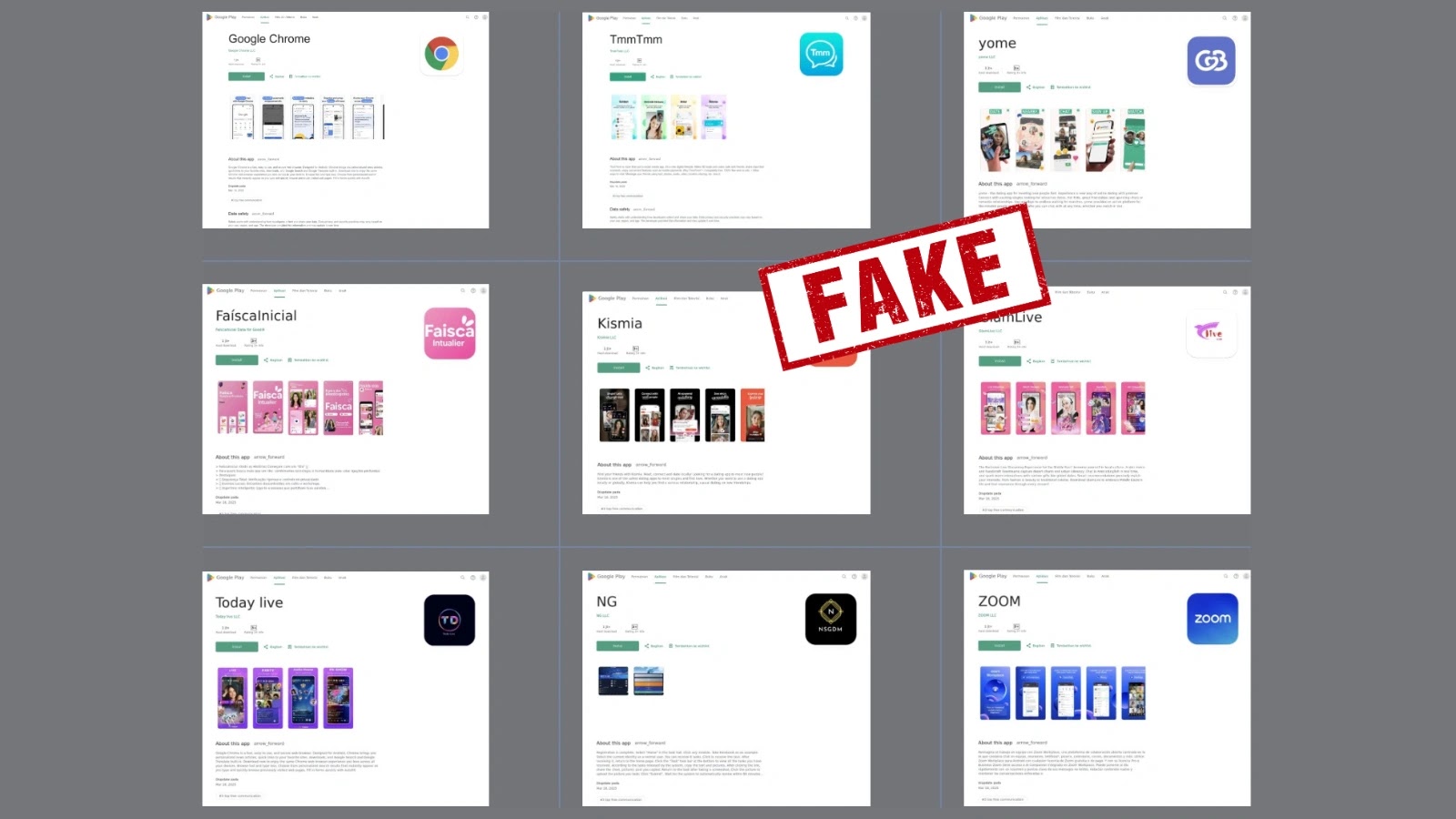
Cybersecurity researchers have identified a resurgence of SpyNote malware campaigns targeting Android users through sophisticated fake Google Play Store websites….
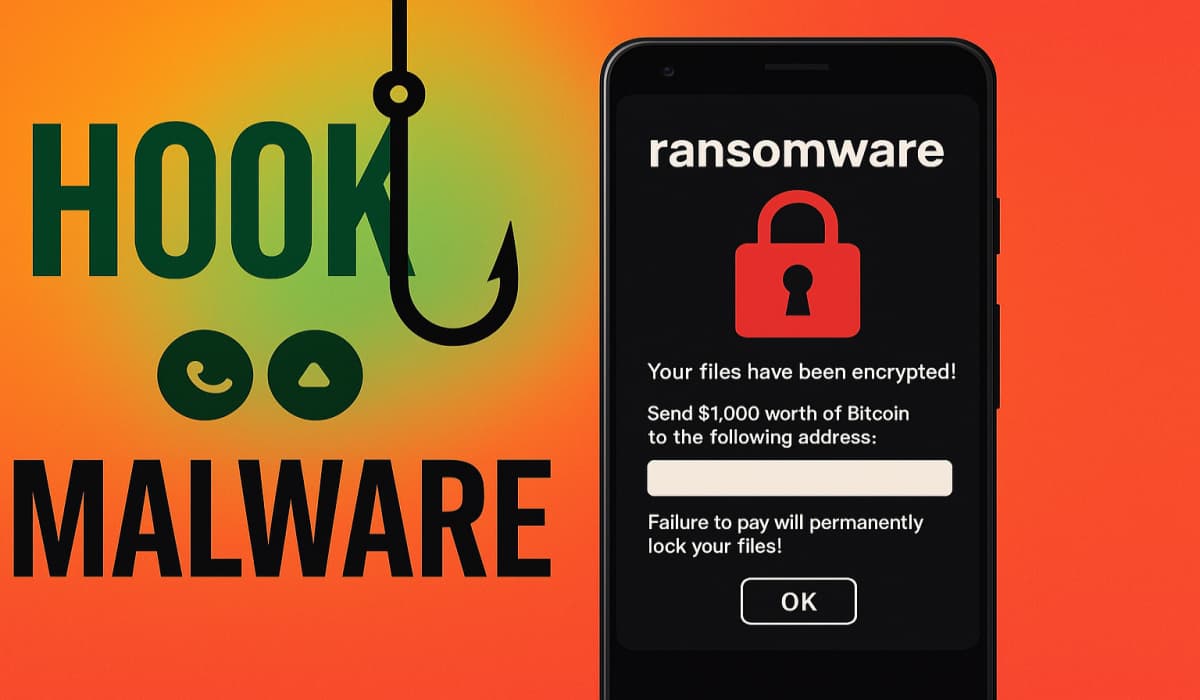
Zimperium’s research reveals the Hook Android malware is now a hybrid threat, using ransomware and spyware to steal data via…
Google has disclosed a critical zero-day vulnerability in the V8 JavaScript engine used by Chrome, tracked as CVE-2025-5419. Before a…
A critical security risk has emerged for Windows users of WhatsApp Desktop who also have Python installed. Attackers can exploit…
CVE-2025-48384, a recently patched vulnerability in the popular distributed revision control system Git, is being exploited by attackers. Details about…
Major French retail chain Auchan announced on August 21, 2025, that it suffered a significant cybersecurity incident resulting in the…
Google Threat Intelligence Group (GTIG) has uncovered a multifaceted cyber espionage operation attributed to the PRC-nexus threat actor UNC6384, believed…
Aug 26, 2025Ravie Lakshmanan Cybersecurity researchers have discovered a new variant of an Android banking trojan called HOOK that features…