Maryland’s transit network experienced widespread disruption this week after a sophisticated cyberattack targeted critical information systems, forcing the Maryland Transit…
Social media algorithms are pushing unsolicited pornographic content into children’s feeds, according to a report by the Children’s Commissioner. The…
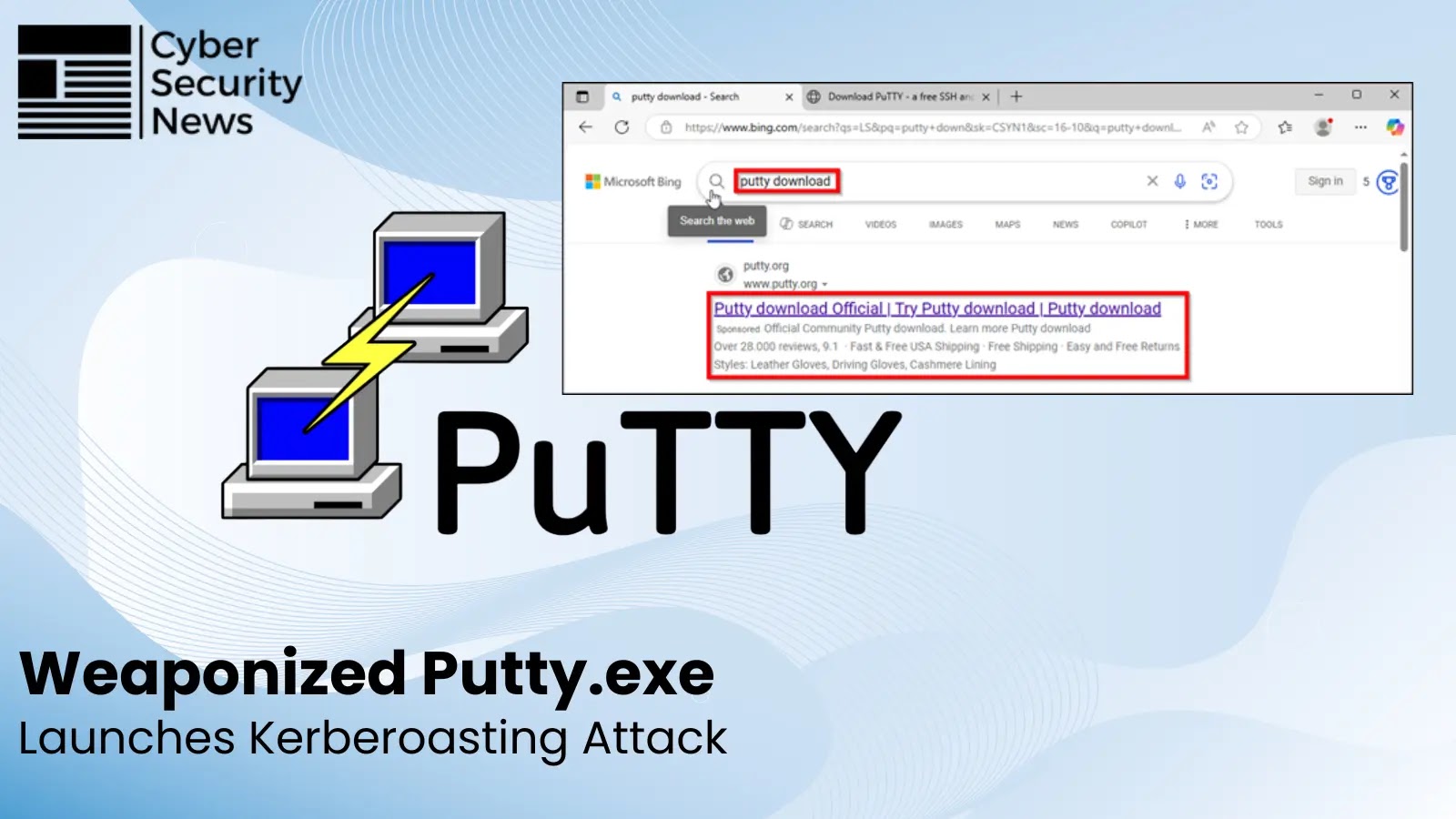
A malvertising campaign using sponsored results on Microsoft’s search platform delivered a weaponized PuTTY that established persistence, enabled hands-on keyboard…
A comprehensive study examining the location data practices of the top 10 social media platforms has uncovered concerning patterns of…
Ty Peavey is a proud man – not proud as in ‘arrogant’, but he can rightly pat himself on the…
Android droppers have evolved from niche installers for heavyweight banking Trojans into universal delivery frameworks, capable of deploying even rudimentary…
Aug 26, 2025Ravie LakshmananVulnerability / Data Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added three security…
For the better part of a decade, digital transformation has been discussed in terms of apps, data and cloud platforms….
A stealthy espionage campaign emerged in early 2025 targeting diplomats and government entities in Southeast Asia and beyond. At the…
Aug 26, 2025Ravie LakshmananMobile Security / Data Privacy Google has announced plans to begin verifying the identity of all developers…
French retail giant Auchan announced on August 21 that it fell victim to a cyberattack that resulted in the theft of loyalty…
Agriculture is a connected, software-driven industry where cybersecurity is just as essential as tractors and harvesters. From embedded hardware in…